Optimize access control in data center facilities to protect server room access, limit unauthorized entry, and support stable and controlled operations.
Physical security demands that access control protects critical infrastructure from unauthorized entry in mission-critical environments. A data center requires strict access management to protect equipment affecting service continuity, data integrity, and operational trust. The server room restricts entry to authorized personnel only, requiring authentication methods that balance security with operational efficiency.
Modern facilities don’t rely on single-point solutions. Identification technologies, physical barriers, and access policies work together to ensure personnel reach only the areas required for their role. Access control systems must remain reliable under routine operations, maintenance activities, and emergency conditions without introducing friction or risk.
Selecting the right methods depends on understanding environmental risks, operational needs, and future scalability. A well-structured design aligns physical security with daily workflows, enabling protection while supporting auditable entry across the facility.
Access management risks specific to data center environments
Data center facilities face security threats that differ significantly from typical commercial spaces. Equipment density, high-value targets, and continuous operation create unique vulnerabilities that standard access control methods cannot address alone. Understanding these risks shapes how organizations deploy protective measures across each server room and support area.
Unauthorized access and insider threat exposure
External threats receive attention, but insider risks often cause greater damage. Employees, contractors, and vendors with legitimate credentials may access areas beyond their authorization. Disgruntled staff, social engineering victims, or compromised accounts can lead to data theft, sabotage, or service disruption.
Mitigating insider threats requires granular access control permission management across every zone. Role-based access ensures technicians enter only equipment areas relevant to their work orders. Time-based restrictions prevent after-hours entry without supervisor approval. Activity logging creates accountability for every transaction—each badge tap and door transition gets recorded with timestamps.
Tailgating risks at shared entry points
Tailgating occurs when an unauthorized person follows an authorized user through a secured door. This simple attack bypasses sophisticated authentication entirely. High-traffic areas like lobbies and corridors are especially vulnerable during shift changes or maintenance windows.
Staffing guards at entry points helps, but human monitoring can’t scale across large facilities. Physical countermeasures enforce consistent access control through turnstiles, optical barriers, and mantraps. Anti-passback rules in the access control software detect when someone exits without entering, flagging credential sharing or tailgating incidents for security review.
Maintaining access management during emergency situations
Emergencies test whether security and safety objectives can coexist. Fire codes require egress paths that unlock automatically during alarms. Power failures affect electronic locks and readers. Evacuation scenarios may require doors to remain unlocked while security staff respond to the incident.
Fail-safe and fail-secure configurations address these conflicts. Egress doors use fail-safe locks that release during power loss, ensuring occupant safety. The server room uses fail-secure locks that remain locked without power, preventing unauthorized access during outages. Battery backup systems maintain controller operation during short-term power events.
Access control methods commonly used in data centers
Several technologies address data center security requirements effectively. Most facilities deploy multiple access control methods in combination, matching each technology to specific zones and threat profiles. The server room typically requires the most stringent verification while perimeter areas use faster throughput methods.
Card-based access systems for controlled entry
Proximity cards and smart cards remain the most widely deployed credential type. Employees carry a single badge for facility-wide access, with permissions varying by zone. Card readers mount at each controlled door and communicate with centralized management software for real-time validation.
Legacy 125 kHz proximity cards offer convenience but provide minimal security—their signals can be cloned with inexpensive equipment. High-frequency smart cards include encryption using DESFire or MIFARE technology that prevents credential duplication. Most security-conscious data center facilities have migrated to encrypted credentials, with OSDP reader communication replacing vulnerable Wiegand protocol connections.
Biometric authentication for high-security areas
Biometrics verify identity through physical characteristics rather than something carried or remembered. Fingerprint, palm vein, iris, and facial recognition systems confirm that the person presenting credentials is actually authorized. Biometric verification eliminates risks from lost credentials including stolen or shared cards.
Server room areas and network operations centers frequently require biometric verification as a second factor. A technician presents their badge, then scans their fingerprint before the door releases. False rejection rates have dropped significantly as sensor technology improves, making biometrics practical for high-traffic applications. Palm vein scanners offer high accuracy with contactless operation.
Mobile access credentials for flexible authorization
Smartphones can now function as access credentials through NFC or Bluetooth communication. Users tap or approach readers with their phones instead of carrying separate badges. Credential provisioning happens remotely through management platforms, eliminating card printing and physical distribution logistics.
Mobile credentials suit contractor and visitor management particularly well in facility environments. Temporary access gets pushed to mobile devices and automatically expires after the scheduled work window. Revocation happens instantly through the management platform. The convenience comes with considerations—device battery life, phone replacement procedures, and ensuring the credential app works across operating systems.
Mantraps and interlocking doors to prevent tailgating
Mantraps create an airlock-style entry where only one door can open at a time. A person enters the first door, which closes behind them before the second door unlocks. Enforced sequencing prevents tailgating at critical transitionsand creates a controlled space for additional verification.
Data center deployments often combine mantraps with weight sensors or overhead cameras to confirm single-person occupancy. If the system detects multiple people, both doors remain locked until security responds. High-security facilities add biometric verification inside the mantrap, ensuring badge holders match the persons actually presentbefore granting server room entry.
Zoning and layered access management design in data centers
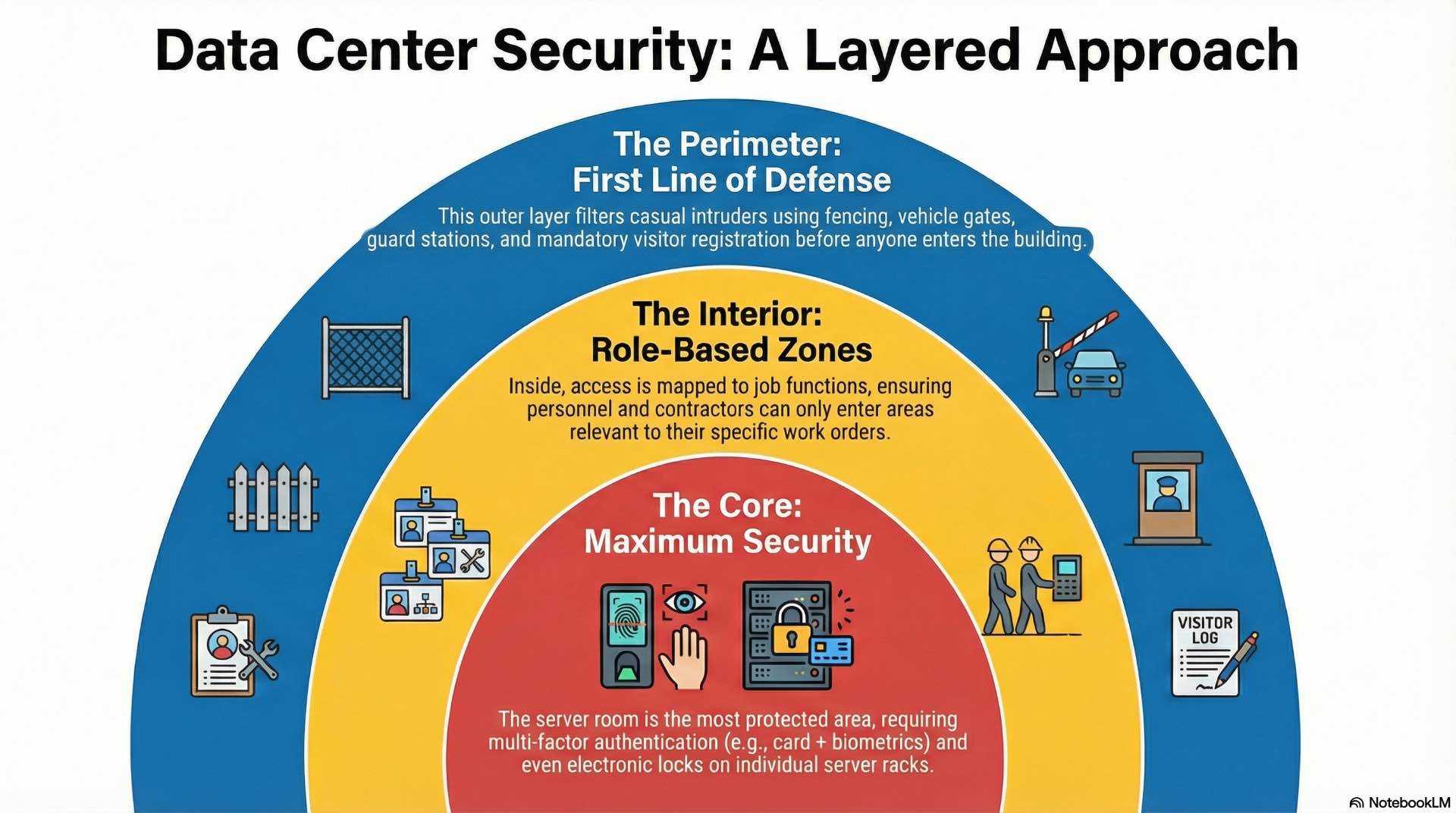
Effective security uses multiple barriers arranged in concentric layers. Each zone applies access control appropriate to its sensitivity level, with more restrictive authentication required as visitors approach critical infrastructure. Most facilities define three to five distinct security zones based on asset value and operational requirements.
Perimeter and facility-level access management
The first layer controls who enters the building or campus. Fencing, gates, vehicle barriers, and guard stations establish the initial boundary. Visitor management systems capture identification and verify appointments before issuing temporary credentials for lobby access.
Parking areas may include license plate recognition to track vehicle access throughout the data center campus. Loading docks require separate credentials and often appointment scheduling to prevent unauthorized deliveries. The perimeter layer filters out casual intruders effectively, leaving only vetted individuals to challenge deeper security layers.
Server room and rack-level access restrictions
The server room requires the highest authentication standards in any data center. Multi-factor combinations—card plus PIN, card plus biometric—are standard practice. Doors include sensors detecting forced entry attempts, propped conditions, or tampering activity that triggers immediate alerts.
Some facilities extend access control to individual cabinets. Electronic rack locks release only when credentials match the specific equipment assignment in the database. This granular approach prevents cross-customer access in colocation environments and limits blast radius if credentials become compromised. Cabinet access logs provide detailed audit trails showing exactly which racks each person opened.
Role-based access zones for personnel separation
Different staff categories need different access patterns within the data center. Operations personnel require 24/7 access to monitoring spaces but may never enter the physical server room floor. Technicians need equipment access but shouldn’t reach administrative offices containing sensitive business data.
Zone definitions map to job functions rather than organizational charts. Contractor badges grant entry to specific project areas only, expiring automatically when work orders close. Badge holders can’t accumulate permissions over time—access control reviews remove stale authorizations regularly. This separation limits exposure when any single credential becomes compromised.
Integrating access control with data center operations
Security systems don’t operate in isolation within a critical facility environment. Integration with operational workflows improves efficiency while maintaining protection across all access points. In any data center, the server room benefits most from tight integration between physical security and IT operations.
Aligning access management with maintenance workflows
Maintenance activities require temporary access changes that must be carefully controlled. Scheduled work orders should automatically grant necessary permissions through integration with ticketing systems, then revoke them upon completion. This lifecycle automation reduces manual credential management burden.
Escort requirements apply when visitors or contractors need access beyond their clearance level. The system can enforce escort rules by requiring authorized badge taps before visitor credentials activate. Some facilities use mustering features during maintenance, requiring personnel to check in and out of work zones.
Access event logging and monitoring practices
Every access attempt—successful or denied—generates log entries in the security system. These records support security investigations, compliance audits, and operational analysis. Real-time monitoring dashboards alert security staff to unusual patterns requiring immediate attention.
Anomaly detection flags behaviors like repeated denied attempts, access at unusual hours, or entry to areas outside normal work patterns. Integration with video surveillance allows rapid review of footage associated with specific access events. Retention policies keep logs available for the duration required by compliance frameworks, often several years.
Coordinating access management with incident response
Security incidents require rapid response that may conflict with normal access control rules. Lockdown procedures instantly restrict non-essential access to contain threats within specific server room zones or building areas. Emergency credential override allows authorized responders to bypass normal authentication during active incidents.
Pre-planned response procedures define who can initiate lockdowns, which doors respond, and how normal operations resume afterward. Tabletop exercises test these procedures regularly to identify gaps before real incidents occur. Integration with building management systems enables coordinated responses—triggering camera recording, activating intercoms, and notifying security personnel simultaneously.
Scaling access control for growing data center needs
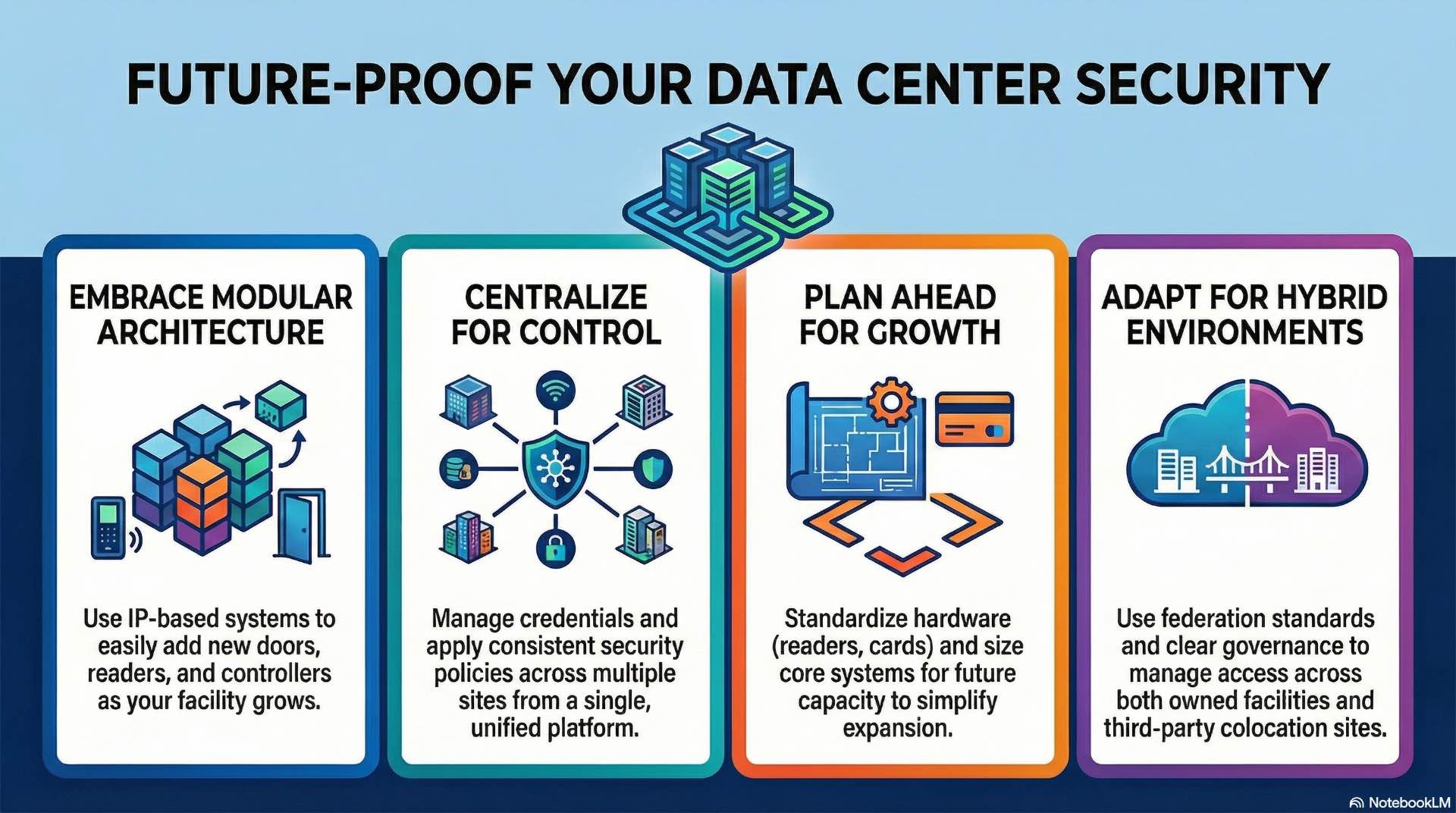
Data center capacity expands over time as organizations add equipment and customers. Access control infrastructure must accommodate growth without requiring complete system replacement. The server room footprint often doubles or triples during facility lifecycle.
Expanding access management as data center capacity grows
Modular architectures allow adding controllers, readers, and doors without system overhaul. IP-based infrastructure leverages existing network capacity rather than requiring dedicated wiring runs for each new access point. Cloud-hosted access control platforms eliminate on-premises constraints for multi-site data center growth.
Planning for expansion means sizing head-end systems appropriately and selecting controllers with available port capacity. Standardizing credential types simplifies inventory management and staff training across multiple deployment phases. Phased deployments allow budget spreading while maintaining consistent security posture across areas as old and new sections come online.
Supporting multi-site and hybrid data center environments
Organizations operating multiple data center facilities need unified credential management across all locations. A technician traveling between sites shouldn’t require separate badges for each location. Centralized platforms synchronize permissions across distributed controllers, applying consistent access control policies enterprise-wide.
Hybrid environments mixing owned facilities with colocation or cloud providers present additional challenges. Federation standards allow cross-platform credential recognition between different vendors, though implementation varies. Clear governance defines who can grant permissions, how access requests flow between organizations, and how audit requirements get satisfied when multiple parties share responsibility.
Designing effective access control for data center facilities demands careful planning across layered security zones and operational integration points. The server room requires the strongest authentication methods available, including multi-factor biometric verification at mantrap entries. Supporting zones apply proportionate controls using card-based credentials and mobile access where appropriate. A well-designed data center balances access control with operational efficiency, enabling authorized personnel to work effectively while keeping unauthorized individuals away from critical infrastructure.





