Access control systems boost security by using authentication to decide who can open each door, when they enter and which areas of a building they reach.
Modern facilities rely on access control systems that regulate physical entry through electronic credentials, biometric verification, and intelligent software platforms. These systems use authentication methods to verify user identities before granting or denying passage to protected spaces. The underlying architecture connects readers, controllers, locks, and management software into a unified security infrastructure that protects buildings and assets at every entry point.
What Is Access Control and How Does It Work
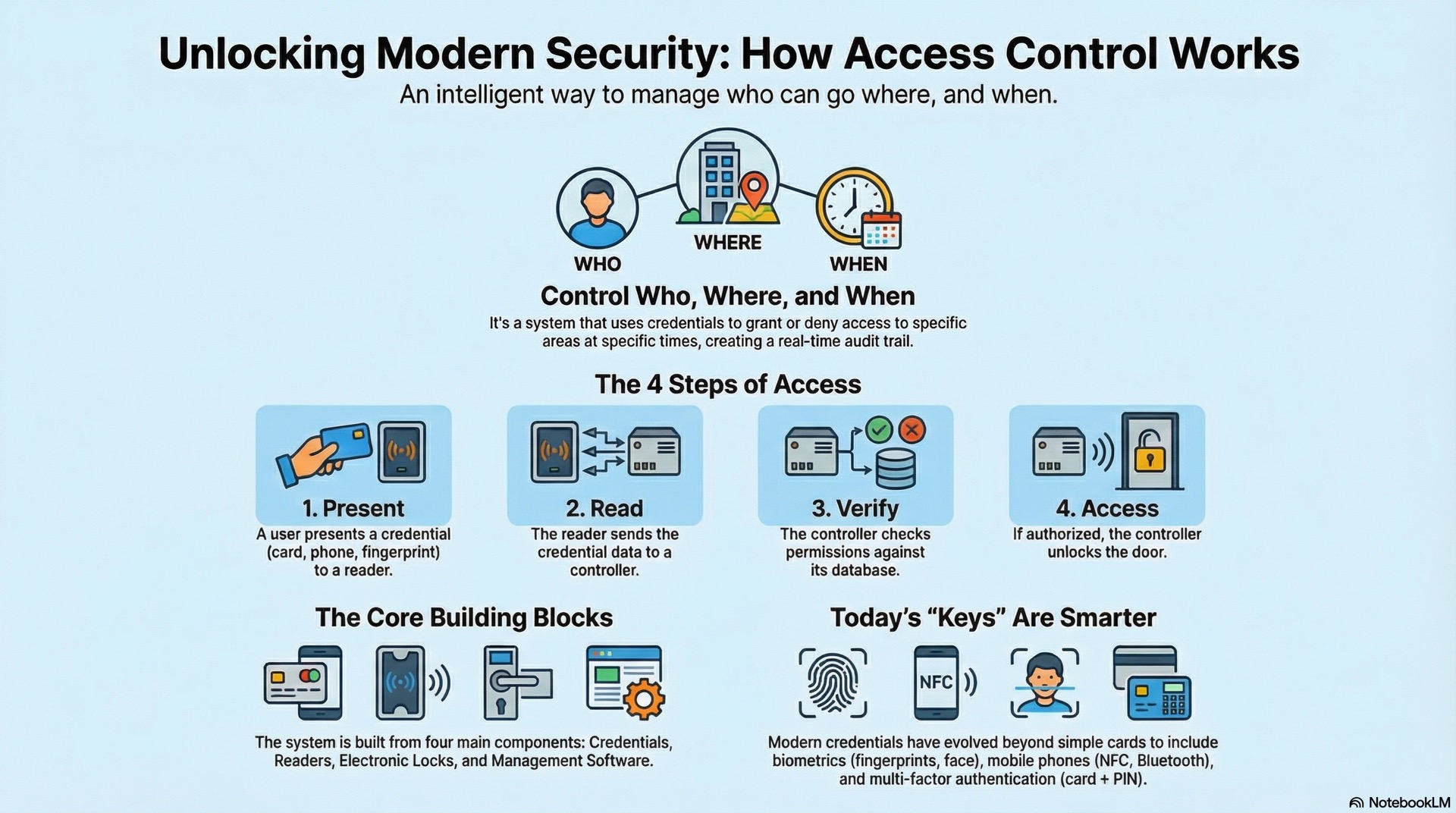
Access control regulates physical entry by applying electronic rules that verify identities and enforce organizational policies. Unlike mechanical locks that rely solely on physical keys, electronic access control authenticates users through credentials and logs every transaction for audit purposes. The basic operation follows a consistent sequence that completes in under one second.
A user presents a credential to a reader mounted at the door. The reader extracts identifying data and transmits it to a controller for processing. The controller compares this data against its database of authorized users, checks time restrictions and area rules, then makes a grant or deny decision. If access is granted, the controller signals the lock to release.
Controllers store access rules locally, allowing doors to function during network outages. This distributed intelligence maintains building security when connectivity is lost. The management platform provides administrators with tools to enroll users, assign permissions, monitor events in real time, and generate compliance reports.
Access Control Technologies
Authentication technology determines how users prove their identity to the system. Each method offers distinct trade-offs between security strength and user convenience, cost, and operational complexity.
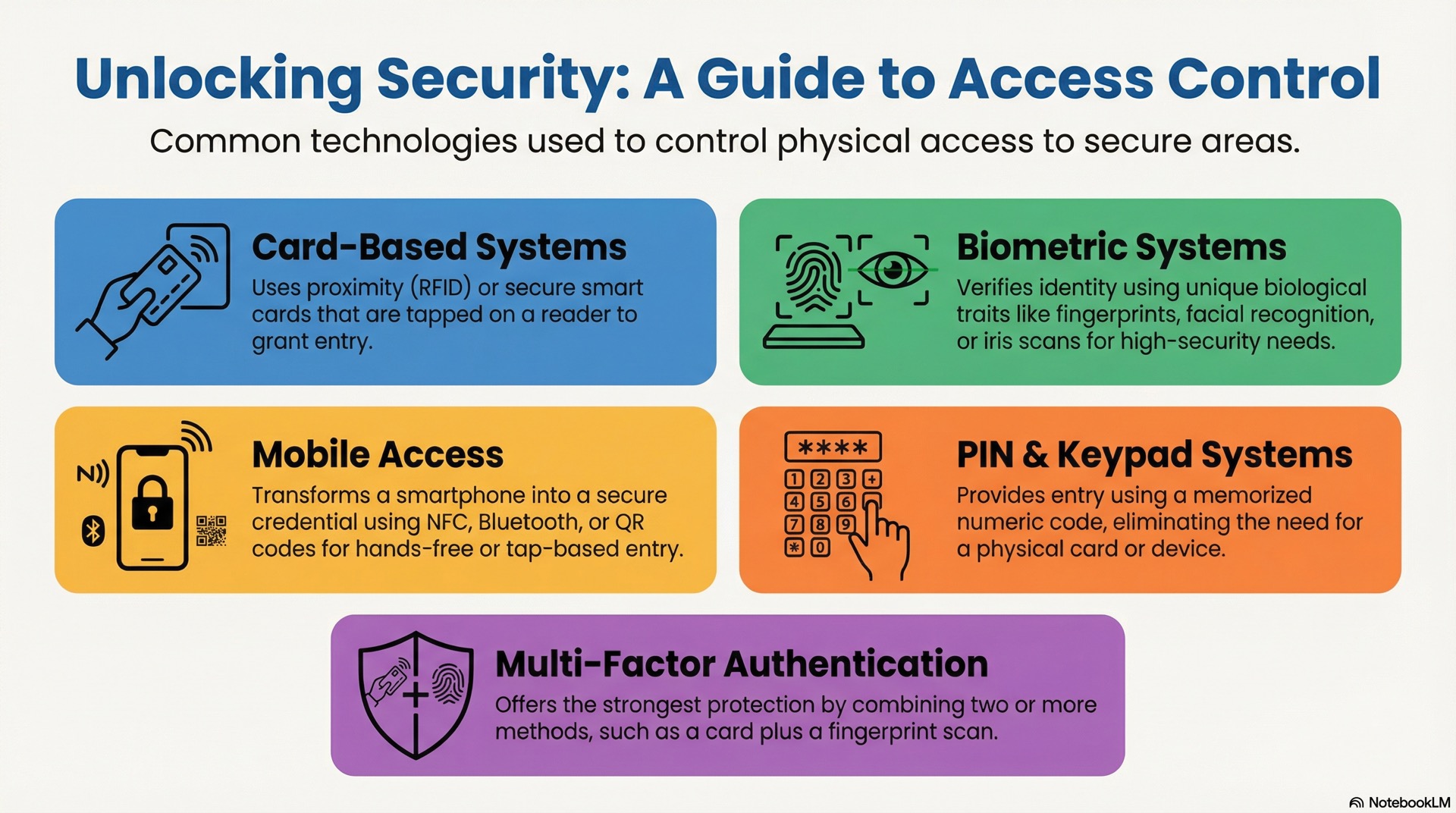
Card-based access systems
Card-based systems remain the most widely deployed credential technology in commercial environments. Proximity cards use low-frequency RFID to transmit unique identifiers when held near a reader. The user simply waves the card within a few centimeters for contactless authentication at the door.
Smart cards offer significantly stronger security through onboard microprocessors. Technologies like MIFARE and DESFire store credential data in protected memory using AES encryption to prevent cloning. DESFire cards are preferred for high-security applications because their advanced encryption resists credential duplication attacks.
Biometric authentication systems
Biometric authentication verifies users based on unique physiological characteristics. Fingerprint authentication scanners analyze ridge patterns and minutiae points to create mathematical templates stored in the system database.
Facial recognition provides touchless authentication by analyzing geometric relationships between facial features. Modern systems use infrared imaging and liveness detection to prevent spoofing. Iris scanners offer the highest accuracy because iris patterns remain stable throughout life.
Mobile access methods
Mobile credentials transform smartphones into access badges using NFC, Bluetooth Low Energy, or QR codes. The management platform sends secure authentication credentials to user devices through a dedicated app.
Bluetooth credentials can work at longer range for hands-free entry where approaching the reader triggers the unlock automatically. Administrators can issue and revoke mobile credentials remotely, eliminating logistics of physical card distribution.
PIN and keypad authentication
Keypad systems require users to enter a numeric code to unlock a door. They eliminate credential management entirely since there’s no physical token to issue or track. Small offices and residential applications often use standalone keypads.
The security weakness is that PINs can be observed, shared, or guessed. Keypads work best as a second factor for multi-factor authentication combined with a card or biometric.
Multi-factor authentication approaches
Multi-factor authentication combines two or more credential types from distinct categories to create layered security. The three categories are something you know, have, and are—representing PINs, cards, and biometrics.
High-security areas like data centers may require card plus biometric verification for entry. Requiring multiple factors ensures that compromise of a single credential doesn’t lead to unauthorized access.
Access System Architecture
Architecture determines how access control components are organized, how decisions are distributed, and how the system responds to failures. Design choices affect reliability and scalability as well as security posture.
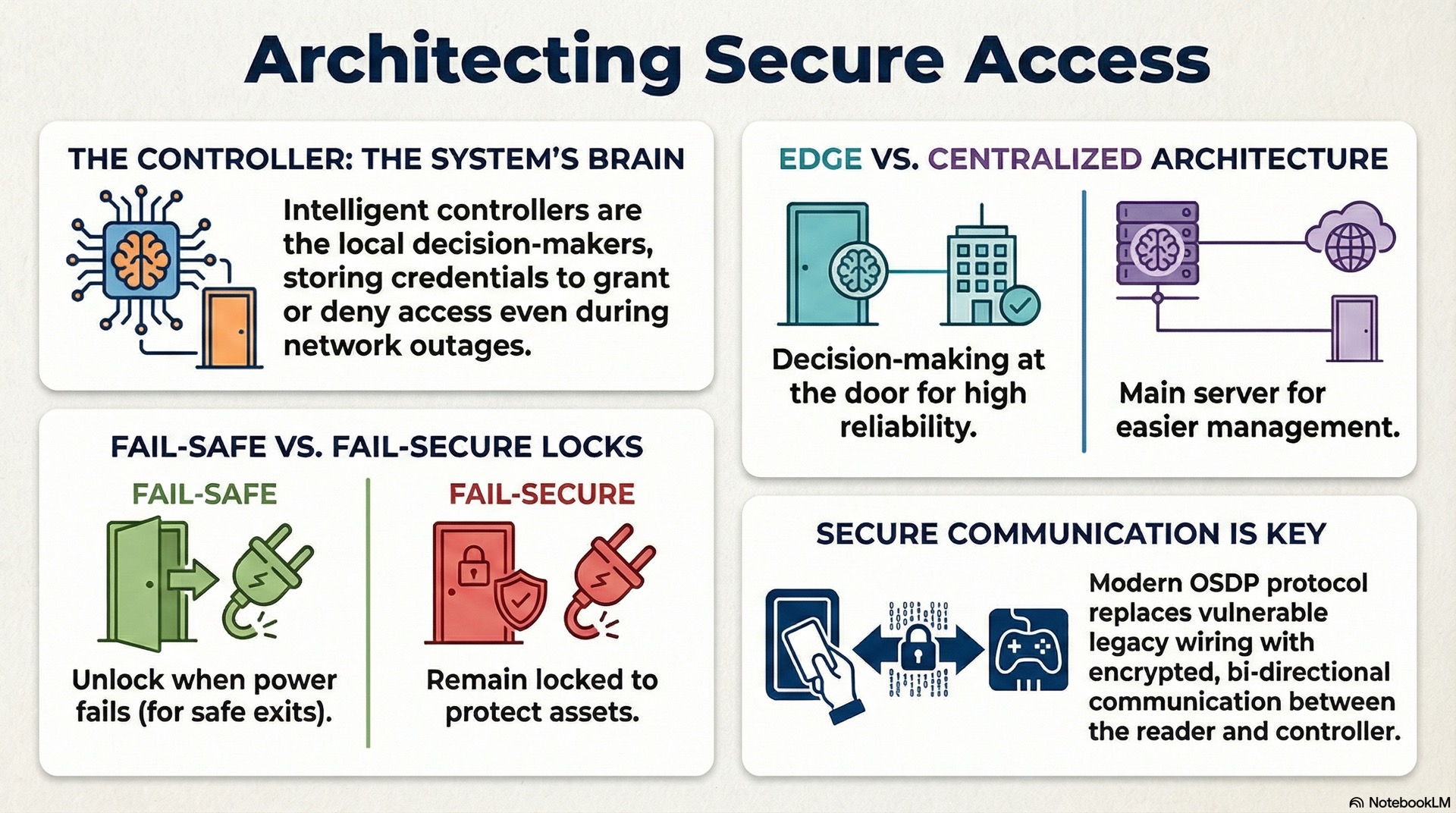
Reader-to-controller system flow
In a typical topology, readers wire directly to a dedicated controller. The reader captures credential data and forwards it to the controller over Wiegand or OSDP protocol. The controller compares received data against locally stored rules and commands the lock.
OSDP addresses Wiegand’s weaknesses with AES-128 encryption and bidirectional messaging. Controllers detect reader tampering or communication failures immediately under OSDP.
Centralized and distributed architectures
In a centralized access control architecture, a server holds the master database and makes all access decisions. Controllers act as relays that forward credential data and wait for responses. This model simplifies database management but creates a single point of failure.
Distributed architectures push decision-making intelligence to local controllers. Each controller maintains relevant access rules and operates independently. The server synchronizes rule changes but doesn’t participate in real-time decisions.
Fail-safe and fail-secure design logic
Fail-safe and fail-secure describe lock behavior during power loss. A fail-safe lock releases when power is removed, ensuring occupants can exit freely during emergencies. Fire exits and stairwell doors typically use fail-safe locks to comply with life safety codes.
A fail-secure lock remains locked during power failure, maintaining security even without electricity. Server rooms and exterior perimeter doors use fail-secure hardware where protection takes priority.
Power supplies and backup strategies
Access control controllers and locks operate on 12 or 24 VDC supplied by dedicated power boards. Power supplies include battery backup to maintain operation during outages. Most installations target four to eight hours of standby time.
Fire alarm integration may require locks to release during alarm conditions. Power distribution must account for total current draw across all connected devices including readers, locks, and sensors.
Redundancy and system resilience
Critical environments require architecture that ensures uninterrupted operation. Redundancy strategies include deploying controllers in primary-backup pairs and maintaining redundant network paths.
Edge controllers that store local copies of rules provide resilience when network connectivity is lost. Database replication keeps access rules synchronized across multiple servers for failover capability.
Access Credentials and Authentication
Credentials are the portable objects or data that users present for authentication to prove their identity. The management and security of these credentials are as important as the physical hardware itself.
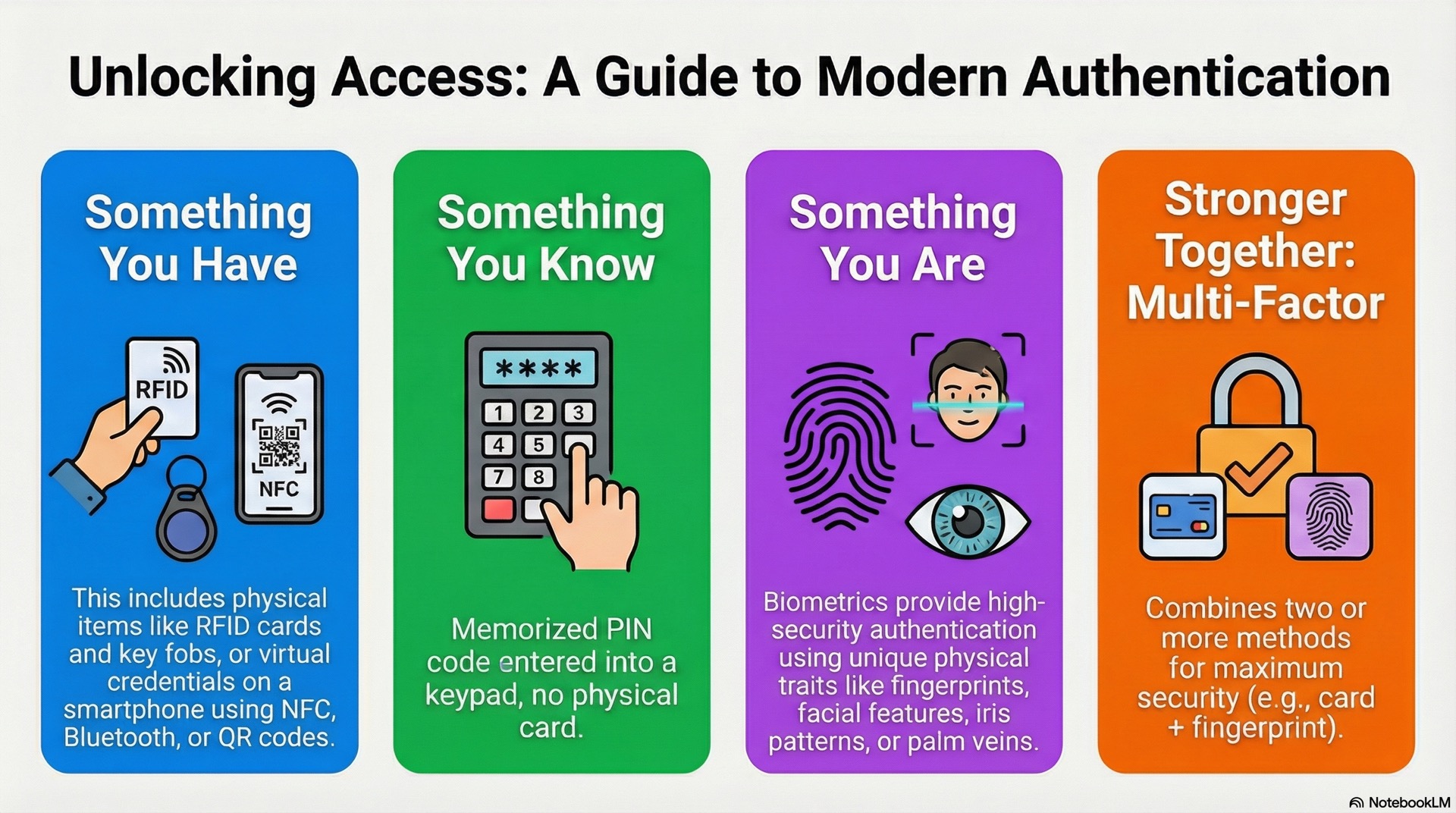
Credential types and formats
Card encoding formats define how data is stored on and transmitted from a credential. Wiegand is an older format that is easily cloned using available hardware. DESFire uses AES encryption to securely store data with strong protection against duplication.
Mobile credentials store encrypted data within smartphone apps. Each format offers different balances of securityand compatibility with existing infrastructure.
Credential issuance and enrollment
Enrollment workflows capture user information and associate it with credentials. For card systems, the administrator assigns a card number to the user record and configures appropriate access permissions.
Biometric enrollment requires capturing reference templates during an initial registration session. The enrollment process must verify user identity through existing HR records before issuing credentials.
Identity verification process
When a reader captures credential data, the authentication process begins immediately. The controller searches its local database for matching records and determines whether the credential is valid for the specific door at the current time.
For biometric systems, the controller compares captured templates against enrolled records and calculates a similarity score. Threshold settings balance false acceptance rates against false rejection rates.
Access rules, schedules, and permissions
Permissions define which doors a credential can open. Administrators assign access levels or groups to users rather than configuring each door individually. A user assigned to the “Engineering Staff” group inherits all associated doors.
Time profiles restrict when access permissions are valid. An employee might have 24/7 access to the main entrancebut only business-hours access to labs or storage areas.
Credential revocation and lifecycle management
Credential lifecycle management tracks cards from issuance through deactivation. When an employee reports a lost card, the administrator immediately deactivates the credential to prevent misuse.
Integration with HR systems automates the credential lifecycle. Terminations revoke credentials within minutes of the HR action, closing the security gap that manual processes often leave open.
Access Technologies Hardware Components
Hardware components form the tangible ecosystem of an access control system. These devices are installed at entry points to read credentials and control locks.
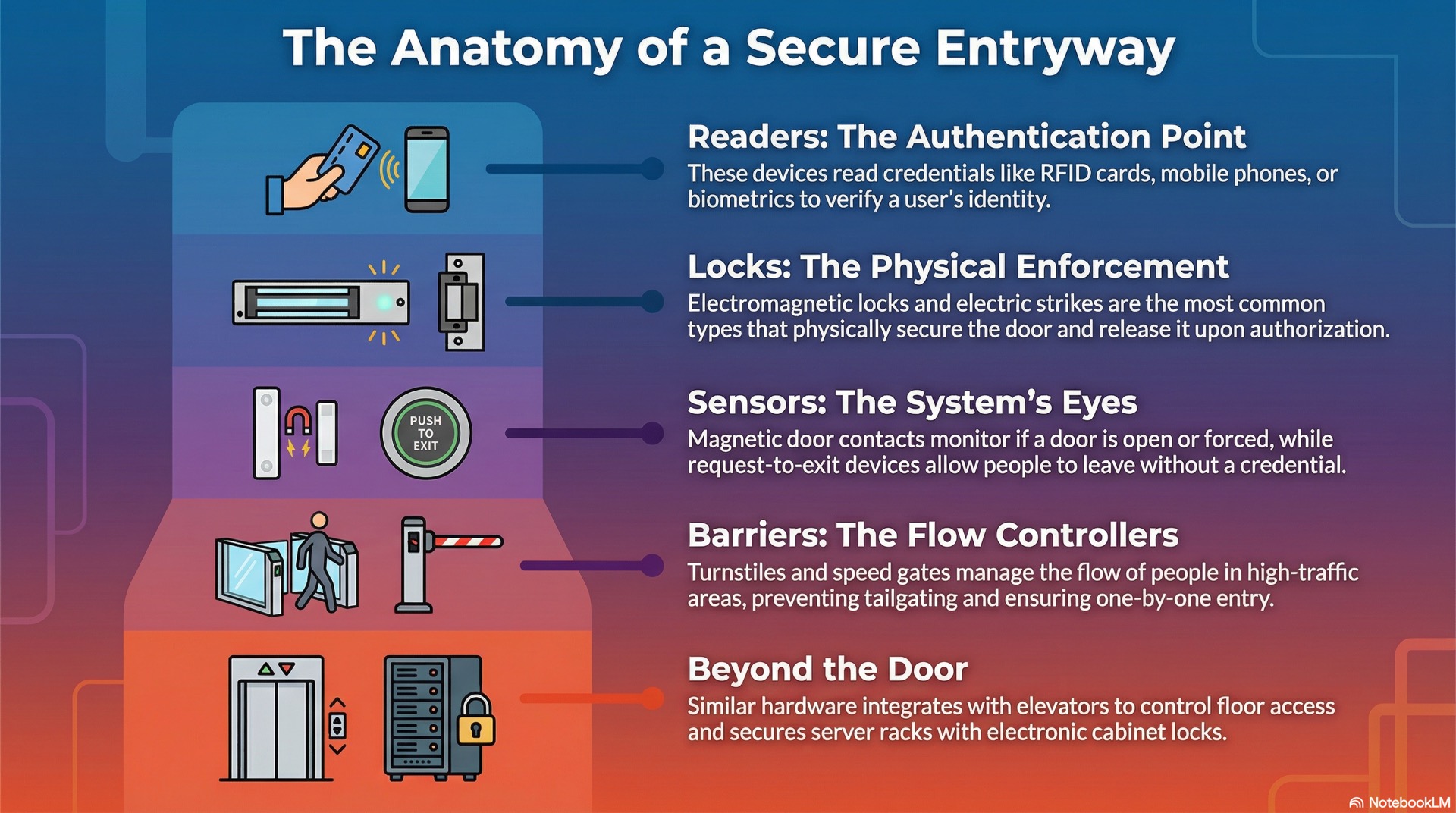
Readers and input devices
Proximity readers detect low-frequency RFID cards at ranges of 5 to 15 centimeters. They provide fast contactless reads for high-traffic entrances and are the most common reader type in commercial installations.
Smart card readers support encrypted credential technologies. Multi-technology readers accept both legacy and modern cards, easing migration during system upgrades.
Controllers and control panels
Single-door controllers manage one entry point with connections for a reader, lock, and sensors. Multi-door controllers handle four or more doors and reduce per-door hardware costs while simplifying installation.
Intelligent controllers store user databases and access rules in flash memory. Capacities range from hundreds to tens of thousands of cardholders depending on the controller model.
Locks, strikes, and door hardware
Electric strikes replace the fixed strike plate in a door frame. When energized or de-energized, the strike pivots to release the latch bolt. The door can then be pushed open without turning the handle.
Magnetic locks use a powerful electromagnet that holds the door with 600 to 1200 pounds of force. Removing power releases the door instantly, making magnetic locks inherently fail-safe.
Door position sensors and REX devices
Door position sensors enable alarms for door forced open or held open events that indicate security breaches. Sensors mount on the door frame with a corresponding magnet on the door.
Request-to-exit devices allow egress from the secure side. Motion sensors detect approaching users and automatically release the lock for free egress without requiring a credential.
Power supplies and peripheral modules
Dedicated power supplies convert AC line voltage to the 12 or 24 VDC required by controllers and locks. Battery backup modules maintain operation during outages with typical capacities supporting four to eight hours.
Relay modules and input expansion boards add capacity for additional doors and auxiliary devices based on access events.
Access Control Software and Management Platforms
Software platforms provide the administrative interface for configuring access control rules, managing users, and monitoring system activity.
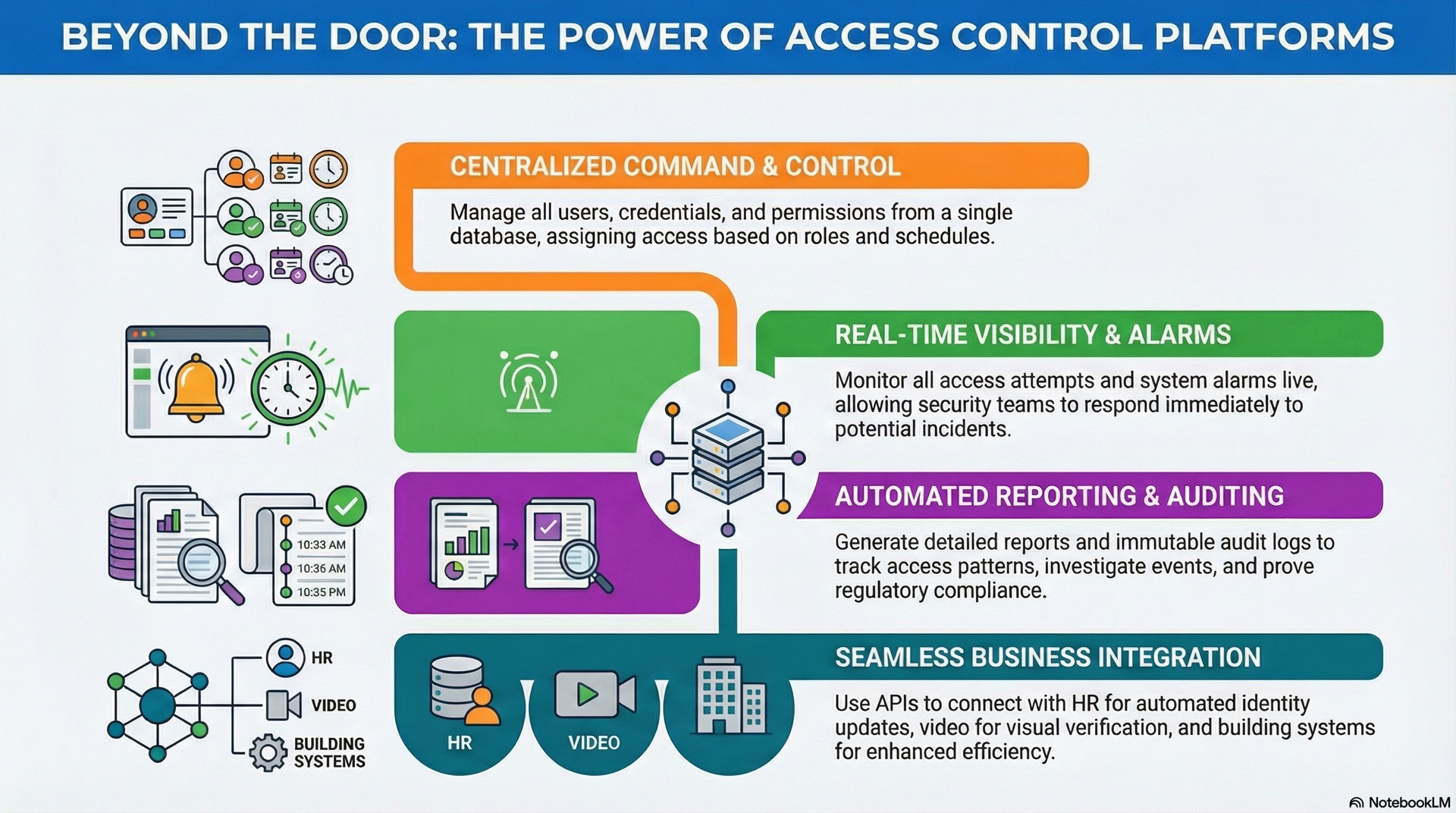
User and identity management
Enrollment workflows capture user information and associate it with credentials. Group and role assignments determine authentication permissions through access levels that bundle multiple doors under a single permission set.
Assigning a user to a role automatically grants all associated permissions. Role-based management simplifies administration for large user populations.
Access policy configuration
Policy configuration defines who can access which doors and when. Administrators create access levels that combine door groups with time schedules into reusable permission templates.
Temporary access policies handle visitors and contractors with automatic expiration after the authorized period to prevent lingering access rights.
Event logging and audit trails
Every access transaction generates an event record that includes timestamp, credential ID, door, and result. Event logs provide the audit trail required for security compliance and investigations.
Retention periods vary by regulation but commonly span one to seven years. Tamper-evident storage protects audit trail integrity for forensic analysis.
Monitoring dashboards and alerts
Real-time monitoring dashboards display door status and alarm conditions. Security operators can acknowledge alarms and lock doors remotely while initiating lockdown procedures.
Alert workflows route events to appropriate responders based on severity and type. Critical alarms trigger immediate notifications.
On-premise and cloud platforms
On-premise systems run server software on hardware located within the facility. The organization maintains full control over database and infrastructure. This model suits environments with strict data sovereignty requirements.
Cloud-based platforms host server functions in secure data centers. Administrators manage access control through web browsers from any location with automatic updates.
Access Control Networking and Integration
Modern access control systems do not operate in isolation. Integration with other building systems multiplies the value of access control data and enables automated workflows across the enterprise.
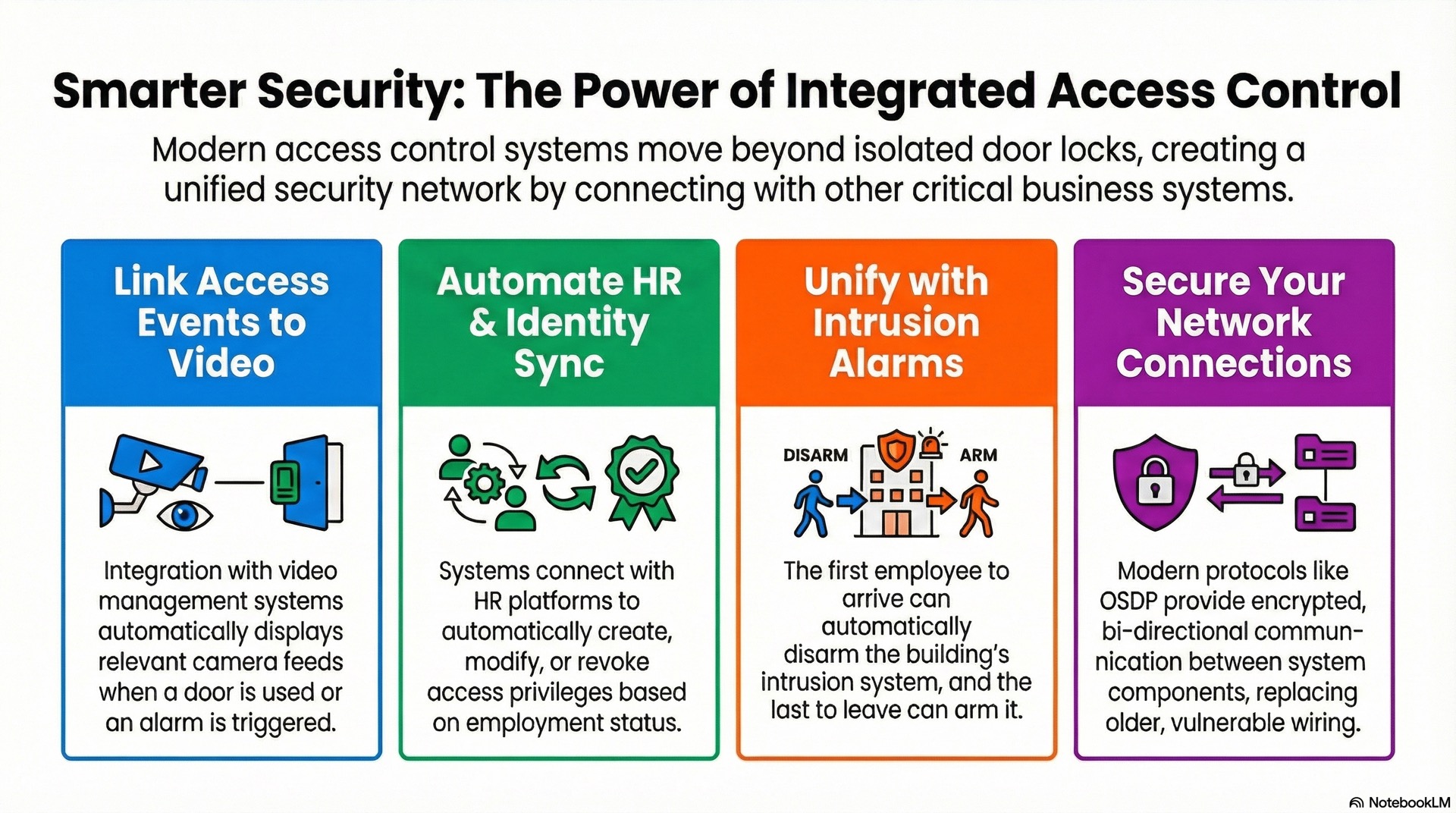
Communication protocols and interfaces
Wiegand remains the most common reader-to-controller protocol despite its security limitations. The interface uses separate data lines that transmit credential bits as electrical pulses without encryption.
OSDP provides encrypted, bidirectional communication between readers and controllers. TCP/IP networking connects controllers to servers using standard Ethernet infrastructure with TLS authentication and encryption.
Network topology and segmentation
Access control networks should be segmented from general IT networks for security. Dedicated VLANs isolate controller traffic from other building systems and limit exposure to network-based attacks.
Fiber optic runs extend communication to remote buildings beyond the 100-meter copper distance limit.
Integration with CCTV and alarm systems
Video surveillance integration links access events to camera footage, providing visual context for every entry. This linkage improves security response times and reduces investigation time from hours to seconds.
Intrusion alarm integration allows systems to arm and disarm based on access activity. The first badge-in can automatically disarm the building’s perimeter alarm.
Integration with building management systems
BMS integration enables automated responses to occupancy changes. When the last person badges out, the system signals the BMS to reduce energy consumption by adjusting HVAC and lighting.
Elevator integration restricts floor access based on cardholder permissions. Destination dispatch systems direct users to elevators and automatically select authorized floors.
Cloud connectivity and remote access
Cloud connectivity enables remote administration of access control systems from any location. Administrators can add users, modify permissions, and review events through secure web portals.
Mobile apps provide on-the-go access to system status. Push notifications alert administrators to security eventsrequiring immediate attention.
Access Control Installation and Commissioning
Proper installation ensures the system functions correctly and meets design specifications. The commissioning phase validates that all components work together to enforce access policies as intended.

Reader and hardware placement
Reader placement affects both security and user convenience. Mounting height of 42 to 48 inches accommodates most users while maintaining accessibility compliance requirements.
Outdoor installations require weatherproof housings rated for the local climate. Vandal-resistant enclosures protect readers in parking garages and remote entrances.
Cabling standards and power distribution
Reader wiring typically uses 18 AWG stranded, shielded cable. Shielding reduces interference from nearby equipment and maintains signal integrity. Wiegand supports runs up to 150 meters.
Low-voltage wiring follows local electrical codes and fire-rated plenum requirements. Conduit protects cables from physical damage in exposed locations.
Controller configuration and addressing
Each controller requires a unique network address and connection to the management server. Configuration includes defining connected readers, locks, and input devices for each door.
Initial programming establishes communication parameters and local database size. Firmware updates should be applied during commissioning to ensure current software versions.
Credential enrollment and validation
Initial credential enrollment populates the database with authorized users. Administrators assign access levels and verify credential functionality at each door before system handover.
Validation testing confirms that permissions and schedules work correctly. Test scenarios should include after-hours access attempts and restricted area denials.
Testing, acceptance, and documentation
Comprehensive acceptance testing verifies all functions meet specifications. Testing protocols cover door lock and unlock operation, alarm generation, and event logging for every controlled opening.
Documentation packages include as-built drawings, equipment lists, and configuration backups. Complete documentation supports ongoing maintenance and future modifications.
Access Control Operations and Maintenance
Long-term reliability depends on consistent operational practices and preventive maintenance. Neglecting these aspects can undermine even the most advanced security technology over time.

Firmware and software updates
Regular firmware updates protect against security vulnerabilities and add new features. Update schedules should balance security patches against operational stability by testing before deployment.
Software updates to management platforms may require database migrations. Maintaining current versions ensures vendor support and compatibility with newer hardware.
Credential lifecycle administration
Ongoing credential management includes issuing new cards, handling lost credentials, and processing terminations. Automated workflows reduce administrative burden and close security gaps by synchronizing with HR systems.
Periodic access reviews verify that permissions remain appropriate. Users who change roles may retain access to areas no longer required for their position.
Hardware health checks
Preventive maintenance includes cleaning readers, testing locks, and inspecting power supplies. Regular inspection identifies failing components before they cause outages or security breaches.
Battery testing verifies backup capacity remains adequate. Batteries typically require replacement every three to five years depending on usage conditions.
Backup and restore procedures
Regular database backups protect against data loss from hardware failures or cyberattacks. Backup procedures should capture configuration, user records, and event history on automated schedules.
Documented restore procedures ensure rapid recovery after failures. Periodic restore testing validates backup integrity and confirms recovery processes.
End-of-life and upgrade planning
Proactive planning addresses aging hardware before failures occur. Manufacturers typically support products for seven to ten years before declaring end-of-life.
Upgrade planning should account for technology evolution and changing security requirements. Migration strategies minimize disruption while transitioning to newer platforms.
Access Control Privacy, Policy and Compliance
Privacy and compliance considerations shape how access control systems are designed and operated. Failure to address these requirements can result in significant legal and financial penalties.
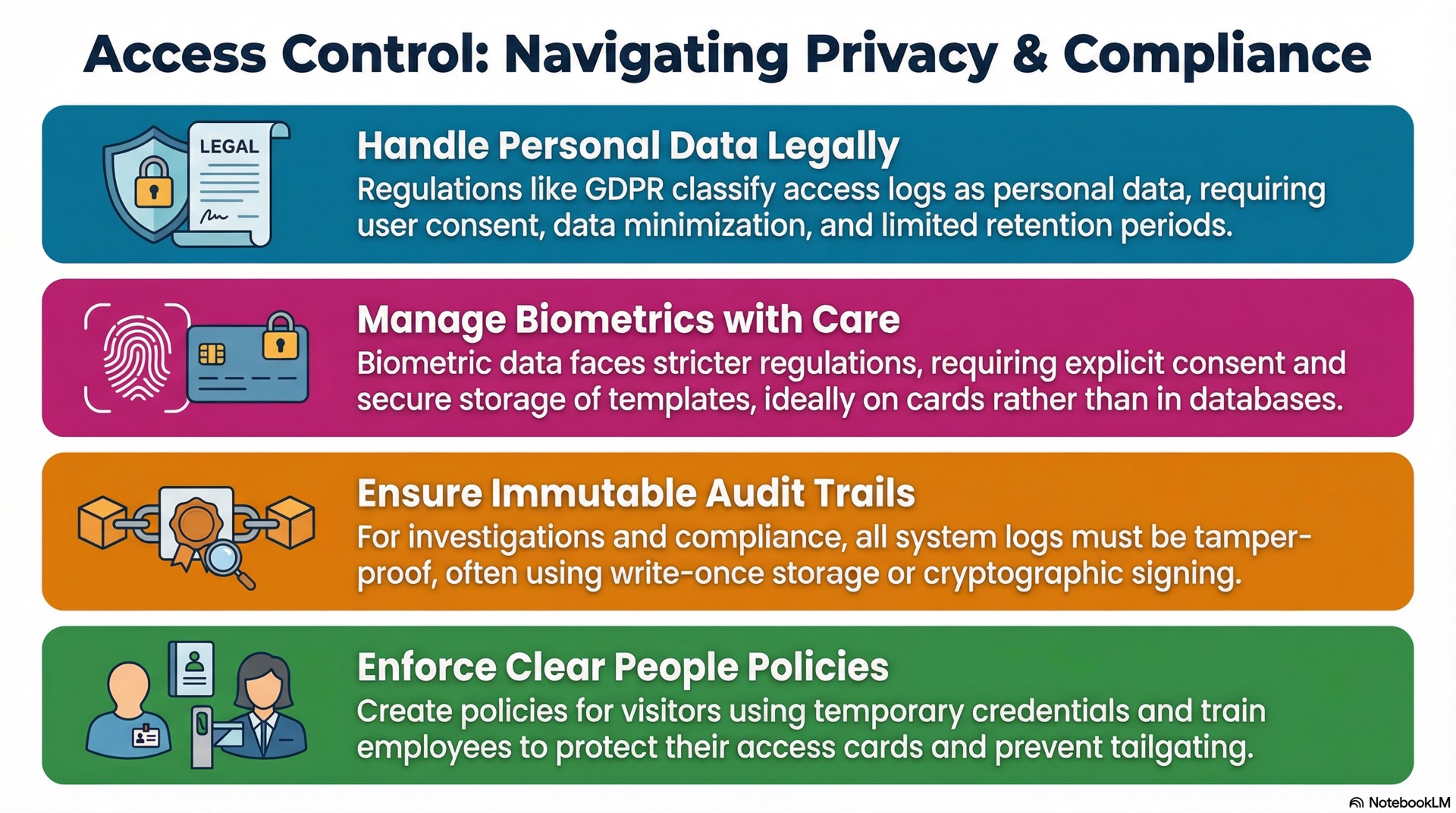
Personal data and identity protection
Access control systems collect personally identifiable information including names, photos, and movement history. Data protection regulations govern how this information is collected and stored.
Minimizing data collection reduces compliance burden and breach exposure. Role-based access to administrative functions limits who can view sensitive user information.
Biometric data handling requirements
Biometric data receives special protection under most privacy regulations. Collection typically requires explicit user consent with clear disclosure of how templates will be stored.
Template storage should use encryption and access controls that exceed protections for other credential types. Some jurisdictions require biometric data deletion upon employment termination.
Audit logs and access records
Maintaining immutable, time-stamped audit trails is a non-negotiable requirement for many industries. Logs must capture every access attempt with sufficient detail for forensic analysis.
Retention periods vary by industry and jurisdiction. Financial services and healthcare typically require longer retention than general commercial applications.
Regulatory compliance considerations
Industry-specific regulations impose requirements on access control implementations. Healthcare facilities must comply with HIPAA requirements for protecting patient areas and medication storage.
Standards from ISO and NIST provide frameworks for security best practices. Demonstrating compliance with recognized standards supports audit processes.
Policy enforcement and governance
Written security policies define organizational expectations for access control. Policies should address credential handling, visitor management, and incident response procedures.
Regular training ensures users understand their responsibilities. Security awareness programs reduce tailgating and other behavioral vulnerabilities.
A well-designed access control system protects facilities and assets while supporting operational efficiency across the enterprise. Credential technologies ranging from cards to biometrics provide authentication mechanisms for identity verification at every entry point. Layered defenses and proper architecture create security controls that prevent unauthorized access through hardware, software, and integration with building systems.





