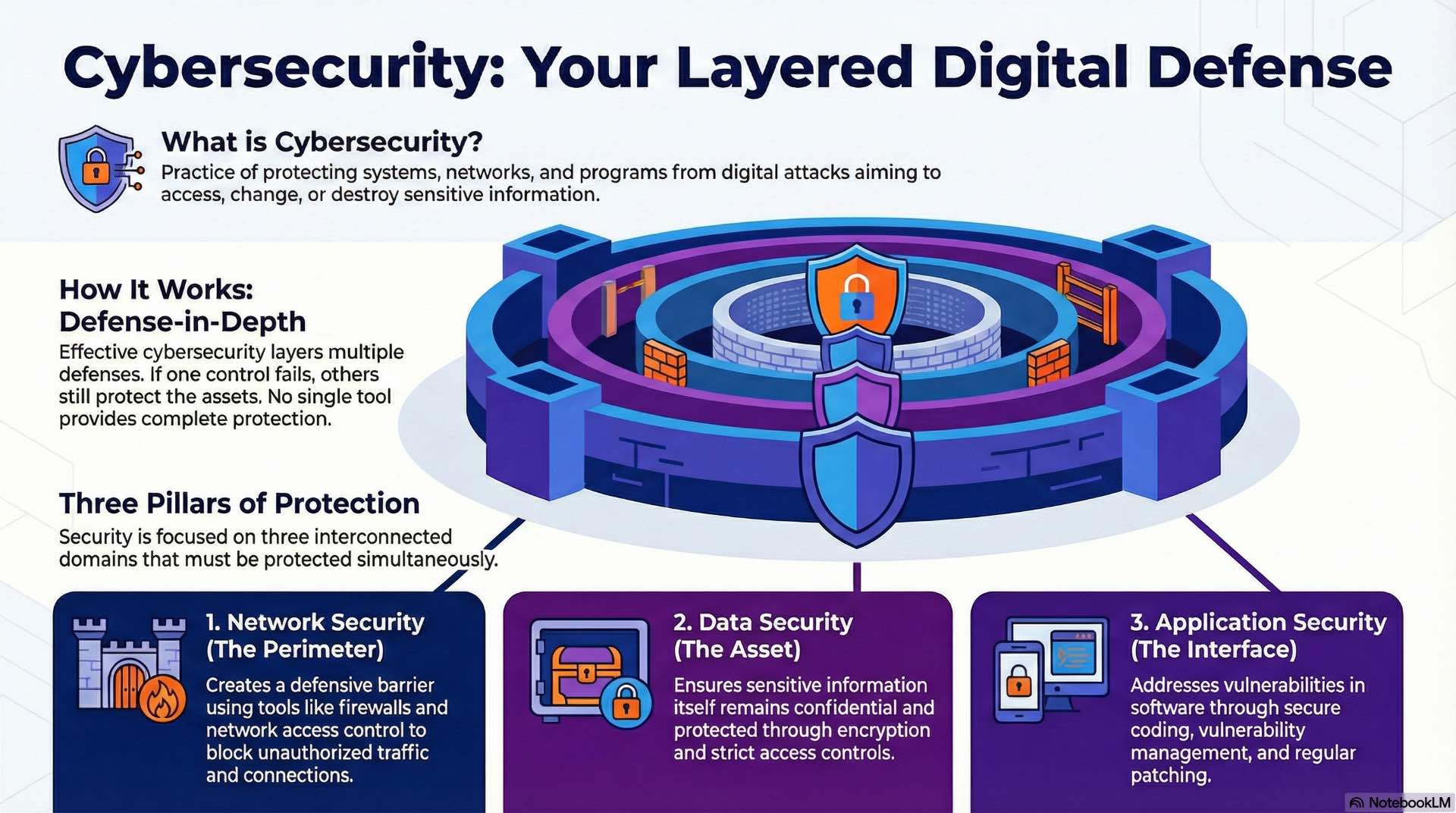
Cybersecurity protects network, data, and application assets using layered protection methods to reduce threats, manage risk, and secure digital systems.
Modern organizations face continuous digital threats targeting their infrastructure and information assets. Cybersecurity establishes the technical controls and operational practices that defend against unauthorized access, theft, and system disruption. Network security creates defensive perimeters around communication pathways, controlling traffic flow and preventing unauthorized connections. Data protection ensures sensitive information remains confidential through encryption and access controls. Application security addresses vulnerabilities in software systems that handle business processes and user interactions.
Effective cybersecurity programs layer these protections so that failure in one area doesn’t compromise the entire environment. Firewalls block unauthorized traffic, but encryption ensures intercepted data remains unreadable. Access controls restrict user privileges, but monitoring systems detect anomalies when legitimate credentials are misused. This defense-in-depth approach recognizes that no single control provides complete protection against sophisticated attackers.
The core challenge lies in protecting three interconnected domains simultaneously. When attackers breach network perimeters, data encryption serves as the last line of defense. When application vulnerabilities expose databases, access controls limit what attackers can extract. Organizations that implement layered cybersecurity defenses across all domains significantly reduce their exposure to costly breaches.
What Is Cybersecurity and How Does It Work
Cybersecurity is the practice of protecting systems, networks, and programs from digital attacks aimed at accessing, changing, or destroying sensitive information. Modern security operations work through technical controls combined with operational procedures that maintain confidentiality, integrity, and availability of digital assets.
The technical foundation starts with boundary defenses. Firewalls inspect incoming and outgoing traffic against rule sets that define permitted communications. Network Access Control solutions verify device security posture before granting connectivity—checking for updated antivirus signatures, proper patch levels, and compliance with organizational policies. Segmentation isolates critical assets from general network traffic, limiting lateral movement when attackers gain initial access.
Detection mechanisms add a second layer. Intrusion detection systems monitor traffic for malicious patterns, comparing network activity against known attack signatures and behavioral baselines. Security Information and Event Management platforms aggregate logs from across the infrastructure, correlating events from multiple sources to identify attacks that individual systems might miss.
Response capabilities complete the operational cycle. When detection systems identify threats, incident response procedures guide containment and recovery activities. Security teams investigate alerts using forensic tools to understand attack scope, identify compromised systems, and close vulnerabilities that enabled the breach.
The governance layer ties cybersecurity controls to business objectives. Risk assessments identify critical assets and prioritize defenses based on potential impact. Security policies translate risk decisions into operational requirements. Compliance programs verify that controls meet regulatory obligations like HIPAA for healthcare information, PCI DSS for payment card information, or ISO 27001 for information security management.
What Are Common Cybersecurity Threats and Attack Types

Understanding threat categories helps security teams prioritize defenses and allocate resources effectively. Attack techniques evolve constantly, but most cybersecurity threats fall into recognizable patterns that organizations can prepare for through appropriate security controls.
Malware, ransomware, phishing, and social engineering
Malware encompasses any software designed to harm or compromise computer systems. Traditional viruses replicate by attaching to legitimate files, while worms spread autonomously across networks without user interaction. Trojans disguise themselves as legitimate software to trick users into installation, then execute malicious payloads that bypass security defenses.
Ransomware represents a particularly damaging threat that encrypts victim files using strong cryptographic algorithms and demands payment for decryption keys. Modern ransomware operations often exfiltrate information before encryption, enabling double extortion—threatening to publish stolen information if victims refuse to pay. Recovery without decryption keys requires restoring from backups, assuming those backups weren’t also compromised during the attack.
Phishing attacks exploit human psychology rather than technical vulnerabilities in cybersecurity systems. Attackers craft emails impersonating legitimate entities like banks, vendors, or internal IT departments to trick recipients into revealing credentials, installing malware, or transferring funds. Spear phishing targets specific individuals using personalized content gathered from social media or previous data breaches.
Social engineering extends beyond digital channels and represents a significant security challenge. Attackers may call help desks claiming to be locked-out executives, drop USB drives in parking lots hoping employees will plug them into corporate systems, or tailgate through secured doors. These techniques bypass technical security controls by exploiting trust and natural human helpfulness.
Internal threats and external attack vectors
External attackers range from opportunistic criminals scanning for vulnerable systems to sophisticated nation-state actors conducting targeted espionage campaigns. Attackers exploit unpatched software vulnerabilities and weak credentials through methods including brute-force attacks and purchasing stolen passwords from underground markets. Cybersecurity teams must defend against this entire spectrum of threats.
Internal threats present different challenges. Malicious insiders—disgruntled employees, contractors with excessive access, or personnel recruited by competitors—already have legitimate credentials and knowledge of valuable targets. Behavioral analytics detect unusual data access patterns such as employees suddenly downloading large volumes of files or accessing systems outside their normal responsibilities.
Negligent insiders cause damage without malicious intent, creating security gaps that external attackers exploit. Employees who reuse passwords, click phishing links, or misconfigure cloud storage create vulnerabilities exposing sensitive information. Security awareness training reduces human error risks, while technical security controls like multi-factor authentication provide additional defensive layers.
How Network Security Protects Systems and Data
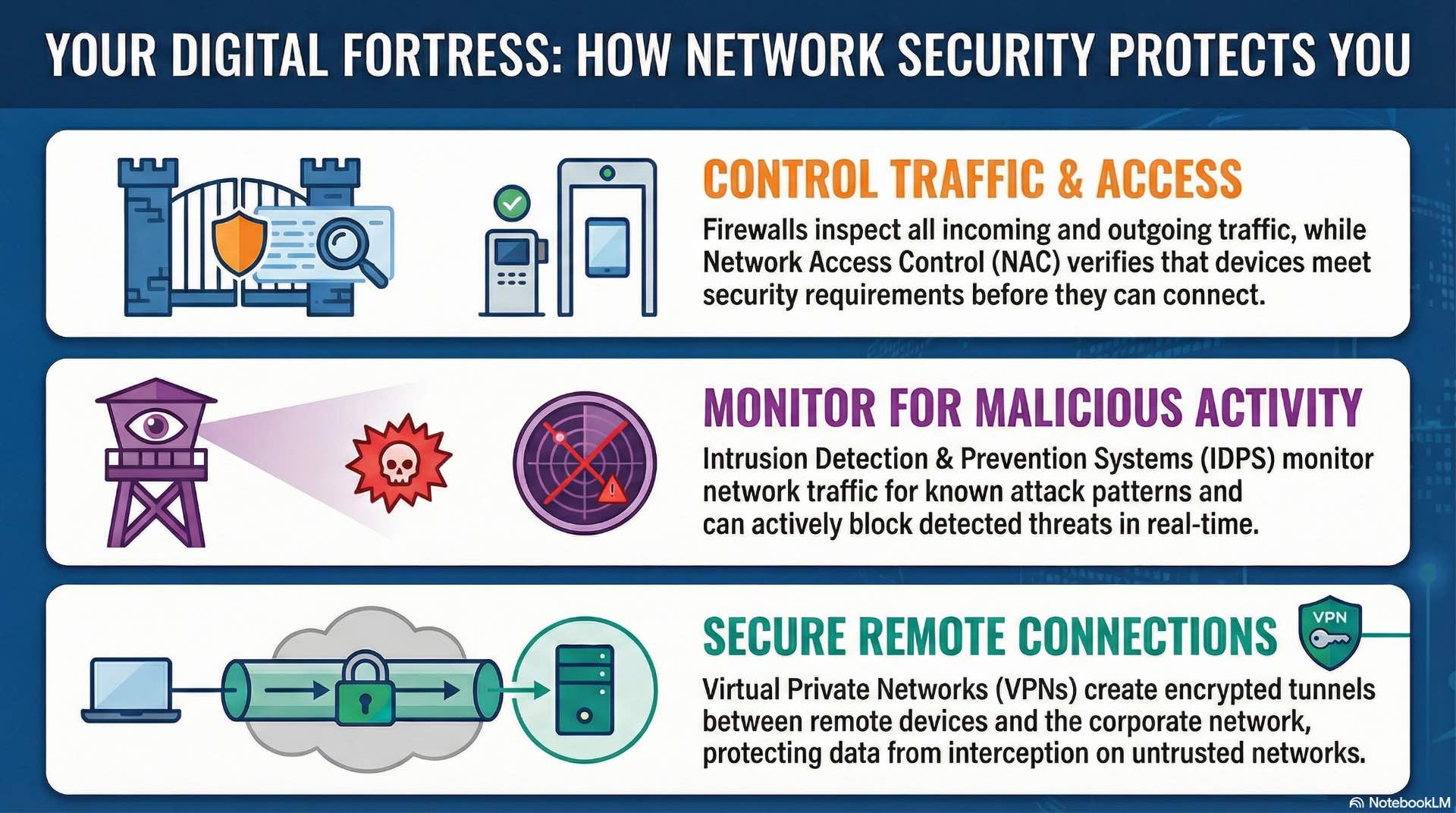
Network security establishes the defensive perimeter controlling access to organizational resources and monitoring traffic for threats. Secure network design builds protection into the architecture from initial planning, using segmentation, defense-in-depth, and minimized attack surfaces as core cybersecurity principles.
Firewalls and network access control
Firewalls operate as traffic enforcement points comparing each connection attempt against configured rule sets. Stateful firewalls track connection states and permit return traffic for established sessions. Next-generation firewalls add application awareness, identifying specific applications regardless of port and enabling policies like allowing web browsing while blocking file sharing.
Network Access Control verifies that devices meet security requirements before connecting to organizational resources. NAC solutions quarantine devices missing critical patches, directing them to remediation networks where updates can be installed before granting full access. This safeguard prevents compromised or misconfigured devices from becoming attack platforms within the trusted network.
Network segmentation divides infrastructure into zones with controlled communication paths. Segmentation isolates payment data systems from general business applications, restricts server-to-server communication to required protocols, and separates guest wireless from internal networks. Attackers who breach one segment face additional barriers before reaching high-value information targets.
Intrusion detection and prevention systems
IDPS platforms monitor network traffic for indicators of malicious activity using multiple detection methods as part of layered security architecture. Signature-based detection identifies known attack patterns including specific exploit payloads, command-and-control protocols, and malware download sequences. Anomaly-based detection establishes baseline traffic patterns and alerts on deviations that might indicate novel attacks.
Inline prevention systems actively block detected threats rather than just alerting administrators. IPS devices drop packets containing injection attempts, terminate connections to known malicious domains, and reset sessions exhibiting scanning behavior. Passive detection systems generate alerts for human review without blocking traffic, reducing risk of disrupting legitimate communications while maintaining security visibility.
Sensor placement determines visibility across the environment. Perimeter sensors detect external attack attempts while internal sensors detect lateral movement after attackers gain initial access. Sensors monitoring traffic to critical servers identify targeted attacks against high-value information assets that perimeter defenses might miss.
Secure remote access and VPN solutions
Remote access extends the network perimeter to wherever employees work, creating new security considerations. VPNs create encrypted tunnels between remote devices and corporate networks, reducing risk from interception on untrusted networks like hotel Wi-Fi or home broadband connections.
Modern remote access architectures move beyond traditional VPN approaches to enhance security. Zero Trust verifies identity and device health for each request rather than trusting all traffic from VPN-connected devices. This protection approach limits exposure when credentials are stolen or devices are compromised by requiring continuous authentication.
Multi-factor authentication strengthens remote access by requiring something the user knows (password), something they have (phone or token), and sometimes something they are (biometric). MFA prevents credential theft attacks from succeeding since attackers can’t complete authentication without the additional factor even when they obtain passwords through phishing.
How Data Security Protects Sensitive Information
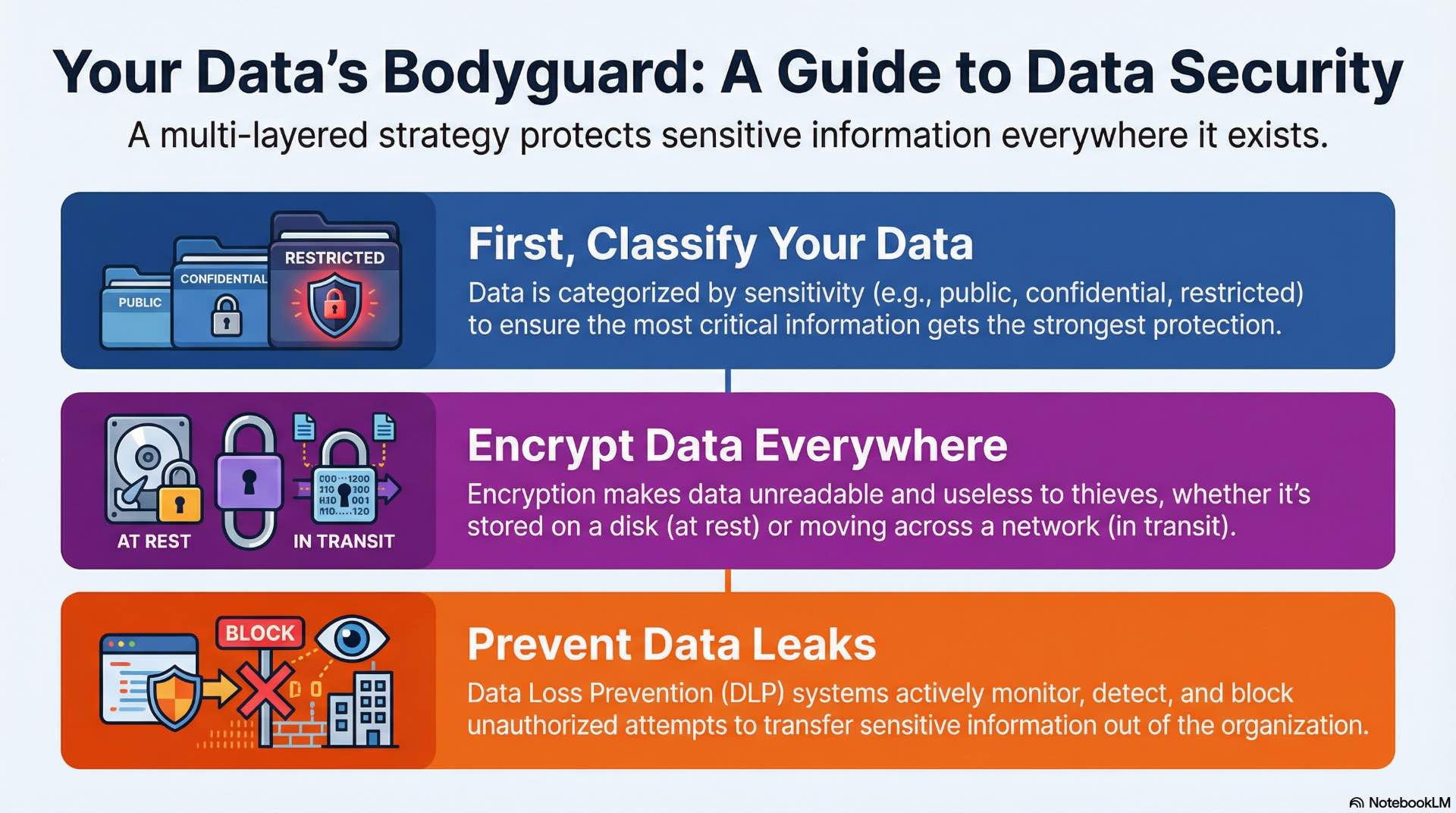
Data security focuses on protecting information itself, recognizing that organizational assets represents the ultimate target of most attacks. Encryption and access controls reduce risk throughout the data lifecycle—at rest in storage, in transit across networks, and during processing. Cybersecurity programs must address these requirements across all stages.
Data classification and exposure risks
Not all data requires the same protection level. Classification schemes categorize data by sensitivity: public information freely shared, internal data restricted to employees, confidential data accessible only on need-to-know basis, and highly restricted data subject to regulatory requirements.
Classification drives security control selection. Public information flows freely without encryption. Confidential data requires encryption and access logging while highly restricted data adds geographic restrictions, enhanced monitoring, and specialized handling procedures. Proper classification ensures resources focus on protecting the most sensitive information.
Data discovery identifies where sensitive information actually resides—often in unexpected locations like email archives, backup systems, or shadow IT applications. Discovery tools scan storage systems for sensitive information patterns including credit card numbers, social security numbers, and health records. You can’t reduce risk for data you don’t know exists.
Encryption for data at rest and in transit
Encryption transforms readable plaintext into ciphertext that appears random without the decryption key, providing essential data protection. AES-256 provides strong symmetric encryption while RSA and elliptic curve algorithms handle asymmetric encryption for key exchange. Properly implemented encryption ensures that stolen data remains useless to attackers.
Data at rest encryption protects stored information from unauthorized access as a core cybersecurity measure. Full-disk encryption protects data on stolen laptops and decommissioned drives. Database encryption protects records even when attackers gain file system access. Application-level encryption protects specific sensitive information fields, limiting exposure even to database administrators.
Data in transit encryption protects information moving across networks. TLS secures web traffic and API communications while IPsec protects network-layer communications between sites. End-to-end encryption ensures that even service providers cannot access data content during transmission.
Data loss prevention methods
Data Loss Prevention systems monitor, detect, and block unauthorized transfers of sensitive information as part of organization-wide security programs. Content-aware DLP inspects data for sensitive patterns like credit card numbers and document classifications. Context-aware DLP considers who is accessing data, from what device, and where they’re sending it.
Endpoint DLP monitors user workstations to prevent unauthorized data movement. DLP blocks copying sensitive information to USB drives and uploads to personal cloud storage. Network DLP inspects traffic leaving the organization, blocking emails containing confidential attachments or detecting sensitive information in encrypted channels.
Effective DLP requires integration with data classification systems so cybersecurity tools know which information requires protection. False positive rates impact usability—too many alerts train users to ignore warnings while excessive blocking disrupts legitimate business activities.
How Application Security Prevents Software Attacks
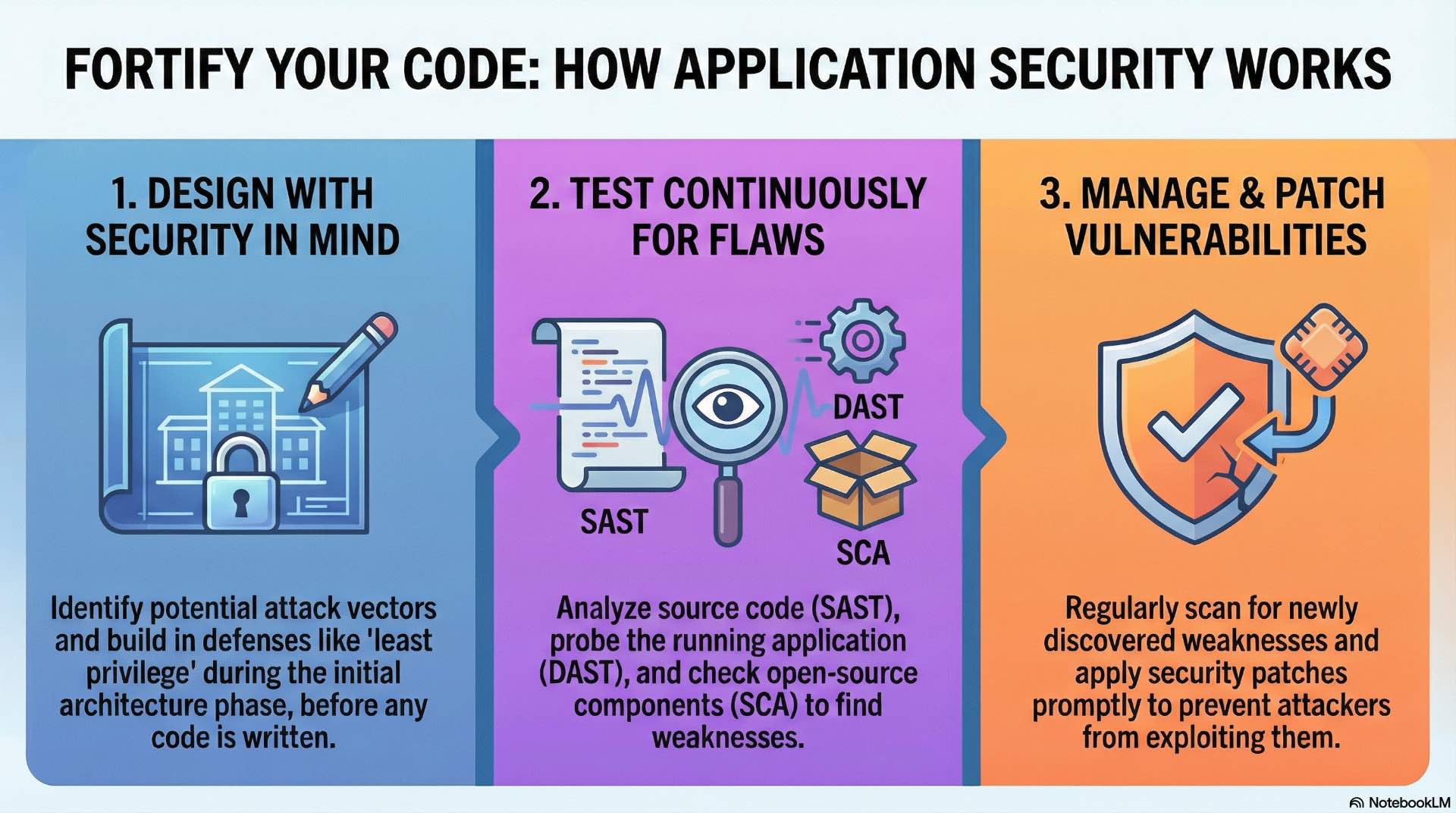
Applications represent the interface between organizations and their users, customers, and partners. Vulnerabilities in application code enable attackers to steal information, manipulate transactions, or pivot to backend systems. Cybersecurity must address risks throughout the software lifecycle from design through deployment and ongoing operation.
Secure application design principles
Security considerations should begin during application design rather than as testing afterthought. Threat modeling identifies attack vectors during architecture phase when changes remain feasible. Developers consider what could go wrong, how attackers might abuse functionality, and which security controls prevent those attacks against application content.
Secure design principles guide implementation decisions in cybersecurity-conscious development. Least privilege limits application permissions to minimum necessary for functionality. Defense in depth ensures multiple security controls safeguard sensitive functions. Input validation treats all external data as potentially malicious, sanitizing it before processing.
Industry frameworks guide secure development practices within cybersecurity programs. OWASP Top 10 identifies critical web application risks including injection flaws, broken authentication, and sensitive information exposure. The SANS CWE Top 25 catalogs dangerous software weaknesses across all application types that developers must understand and avoid.
Vulnerability management and patching
Vulnerability management identifies and remediates security weaknesses before attackers exploit them. Automated scanners probe systems for known vulnerabilities including missing patches, insecure configurations, and outdated software versions. Penetration testers simulate real attacks to find issues that automated tools miss.
Prioritization determines which vulnerabilities receive immediate cybersecurity attention. CVSS scores indicate vulnerability severity and potential impact but context matters. A critical vulnerability in internet-facing systems demands faster response than the same issue in isolated test environments.
Patch management applies vendor-released fixes in timely manner while balancing testing requirements. Compensating controls provide protection during patch testing periods—network segmentation limits exposure, enhanced monitoring detects exploitation attempts, and web application firewalls reduce risk against known attack patterns.
Application security testing methods
Static Application Security Testing analyzes source code without executing the application as part of cybersecurity quality assurance. SAST tools identify coding errors during development enabling fixes before deployment. These tools examine code paths, data flows, and function calls to detect vulnerabilities that could be exploited.
Dynamic Application Security Testing probes running applications by simulating attacks. DAST tests for injection vulnerabilities and authentication weaknesses that only manifest during runtime. Unlike SAST, DAST doesn’t require source code access, enabling security testing of third-party applications.
Software Composition Analysis identifies vulnerabilities in open-source components that comprise significant portions of modern applications. SCA tools track component versions against vulnerability databases alerting cybersecurity teams when dependencies require updates due to newly discovered security issues.
How Infrastructure and System Security Reduce Risk
Infrastructure security protects foundational services—DNS, email, logging systems—upon which all IT operations depend. System security hardens individual computing assets against attack and unauthorized use, treating every endpoint as its own perimeter requiring protection.
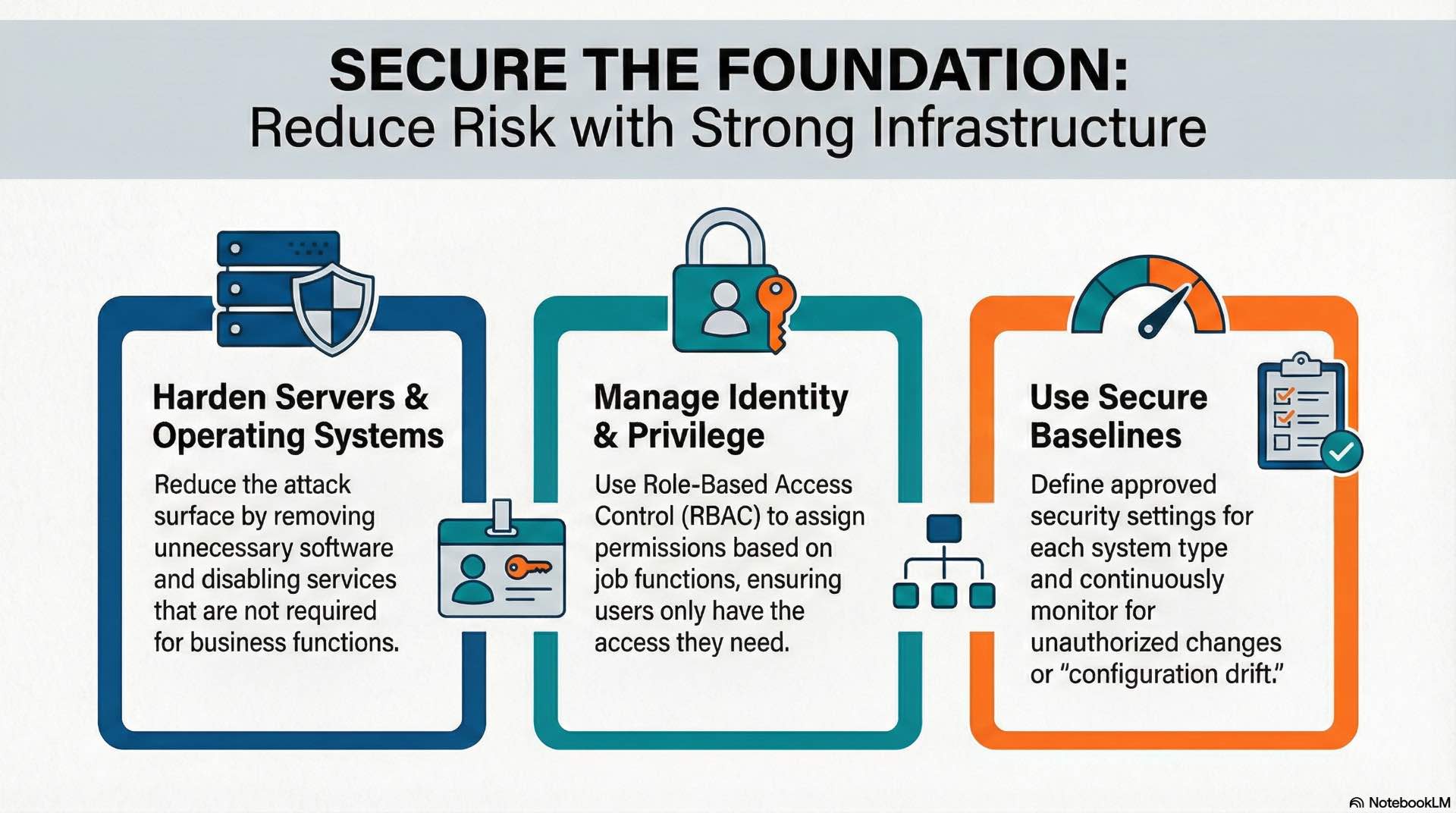
Server and operating system hardening
Hardening reduces attack surface by removing unnecessary services and applying restrictive permissions as fundamental cybersecurity practice. Default installations include features most deployments don’t need, each representing potential vulnerabilities attackers could exploit to access sensitive information.
Windows and Linux require different hardening approaches though security principles remain consistent. Disable unused services and remove unnecessary software to minimize attack surface. Configure logging to capture security-relevant events. Apply file system permissions restricting access to sensitive configuration files and executables.
Security baselines from CIS Benchmarks provide configuration checklists for each operating system and role. Automated tools enforce baseline compliance and detect drift when systems are modified outside approved change processes. Configuration management ensures systems remain hardened over time, maintaining security.
Identity and privilege management
Identity management controls who can access systems and what actions they can perform within the cybersecurity framework. Centralized identity providers enable consistent authentication across applications through Active Directory, LDAP directories, or cloud identity services.
Privileged access management applies additional controls to high-value administrative accounts. PAM solutions store credentials in secure vaults with session recording, just-in-time access grants, and mandatory approval workflows. This protection prevents attackers from easily exploiting stolen administrative credentials to access sensitive information.
Role-based access control assigns permissions based on job functions rather than individual users. RBAC ensures access changes when employees change roles, removing permissions no longer needed. Regular access reviews verify users retain only permissions their current responsibilities require, supporting cybersecurity governance.
Secure system configuration baselines
Configuration baselines define approved settings for each system type within the cybersecurity program. Baselines specify required security settings and prohibited configurations covering everything from enabled services to encryption cipher suites.
Configuration compliance tools continuously verify systems match their baselines as ongoing security monitoring. Compliance monitoring detects unauthorized changes and configuration drift that might indicate attacker modifications or improper maintenance procedures. Automated remediation restores compliant settings without manual intervention.
Infrastructure as Code extends baseline concepts to cloud environments for consistent security. IaC templates define infrastructure as version-controlled configurations enabling consistent deployment and preventing drift through immutable infrastructure patterns where systems are replaced rather than modified.
How Advanced Threat Protection and Incident Response Work
Advanced cybersecurity threats require sophisticated defenses beyond signature-based detection. Incident response ensures organizations can contain and recover from successful attacks through structured procedures and trained personnel.
Threat detection and continuous monitoring
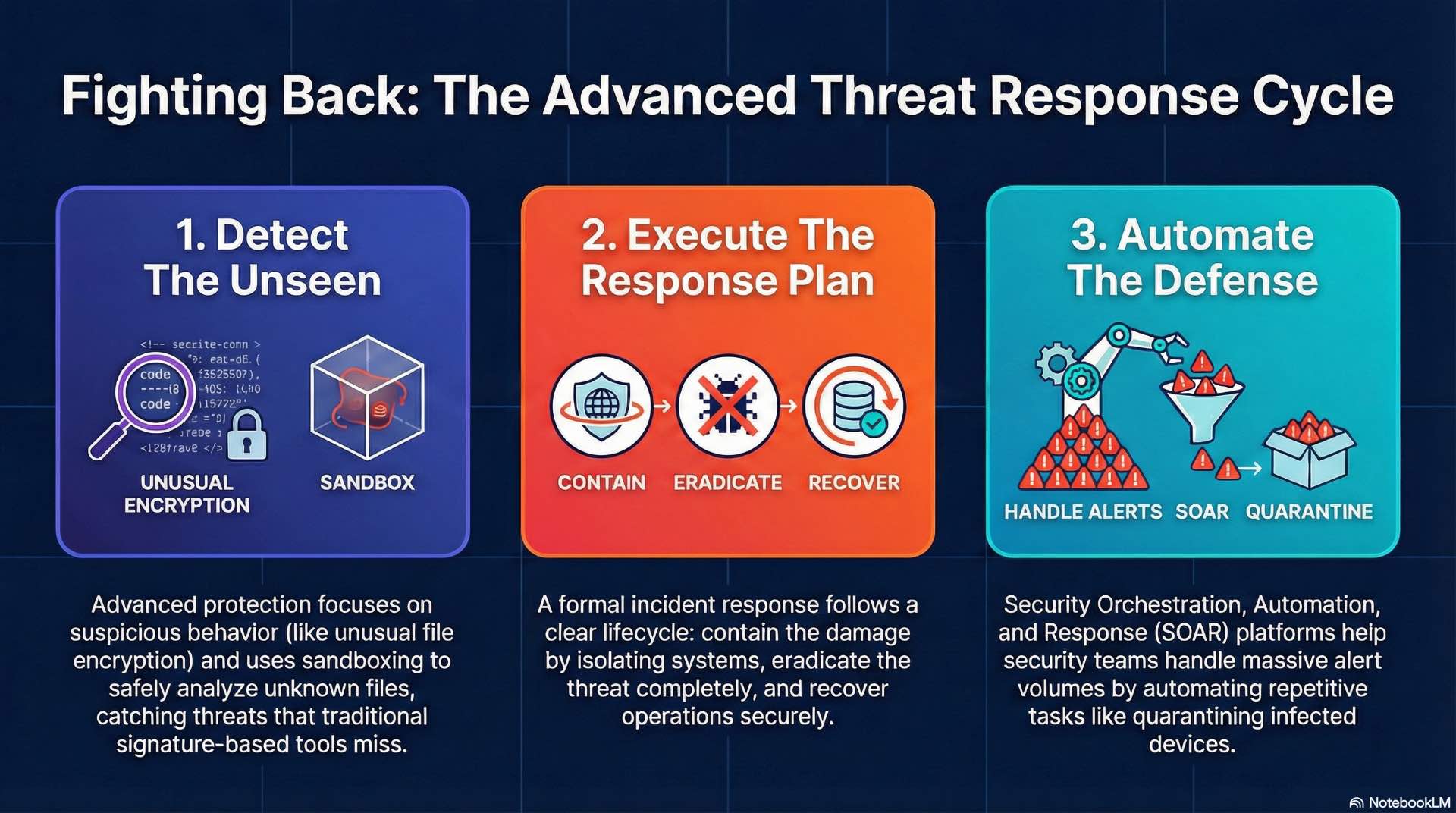
Advanced Threat Protection focuses on sophisticated attackers who evade traditional defenses through novel techniques. Behavioral analysis identifies malicious activity based on actions rather than signatures—detecting ransomware by file encryption behavior, identifying command-and-control traffic by communication patterns, and flagging credential theft by unusual authentication sequences.
Sandboxing isolates suspicious files in virtual environments for safe observation as part of cybersecurity analysis. Sandboxes observe file behavior without risking production systems, noting registry modifications, network connections, and file system changes that reveal malicious intent. This enables security teams to analyze potential zero-day threats before they can cause damage to organizational assets.
Threat intelligence feeds provide context about known attackers and their techniques to enhance security awareness. Intelligence correlates internal telemetry against known indicators to identify when adversary infrastructure contacts organizational networks or observed behaviors match documented attack patterns.
Incident response process and lifecycle
Incident response follows structured phases: preparation, detection, containment, eradication, recovery, and post-incident review. Preparation establishes cybersecurity teams and procedures before incidents occur so organizations can respond effectively under pressure.
Containment limits damage by isolating affected systems and blocking attacker access to sensitive information. Short-term containment prioritizes speed over completeness—disconnecting compromised systems from networks immediately. Long-term containment maintains business operations while investigation continues and eradication plans develop.
Eradication removes attacker presence completely: deleting malware, closing vulnerabilities, resetting compromised credentials, and eliminating backdoors. Recovery restores systems with confidence threats are eliminated while post-incident reviews identify lessons learned and drive cybersecurity improvements preventing similar incidents.
Security operations and automation tools
Security Operations Centers provide centralized monitoring and response capabilities around the clock. SOC analysts triage alerts and coordinate response actions investigating suspicious activity and escalating confirmed incidents to response teams.
Security Orchestration, Automation, and Response platforms automate repetitive cybersecurity tasks that would overwhelm manual processes. SOAR playbooks execute automated responses to common alerts—enriching indicators with threat intelligence, isolating compromised endpoints, and creating tickets for analyst review.
Automation enables security teams to handle massive alert volumes efficiently. When phishing is reported, automation searches for other recipients, quarantines related messages, extracts and analyzes attachments, and blocks sending infrastructure—all within minutes rather than hours.
How Mobile and Endpoint Security Protect Devices
Mobile devices and endpoints represent the network edge where users interact with organizational assets. The endpoint protection must address diverse devices and usage patterns across corporate-owned and personal equipment as part of end-to-end security strategy.
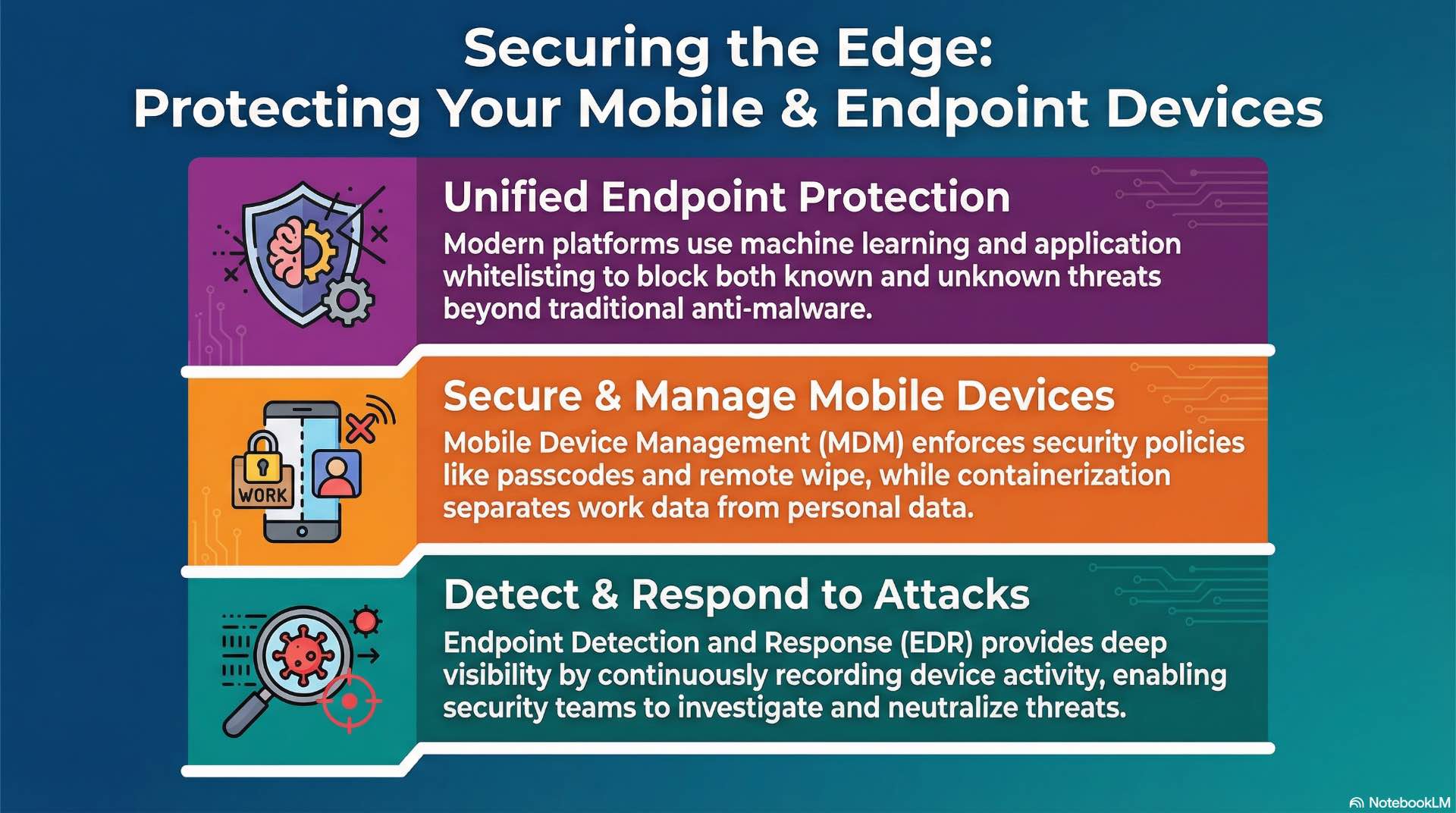
Endpoint protection platforms
Endpoint Protection Platforms consolidate multiple security functions including anti-malware, host-based firewalls, and device control. Modern EPP uses machine learning to identify malicious files without relying solely on signature databases, detecting novel malware variants that signature-based tools miss.
Application whitelisting inverts traditional security models by permitting only approved applications to execute. Whitelisting blocks unknown executables including zero-day malware that hasn’t been identified by antivirus vendors. This default-deny protection approach provides strong protection against diverse attack vectors threatening data.
Device control manages removable media and peripheral connections according to organizational cybersecurity policy. USB device policies prevent data exfiltration and malware introduction through physical media. Policies might prohibit storage devices entirely, allow only encrypted devices, or permit specific approved hardware.
Mobile device security controls
Mobile Device Management extends organizational security control to smartphones and tablets used for work purposes. MDM enforces passcode requirements and enables remote wipe of lost devices. Containerization separates work content from personal information on BYOD devices, reducing risk for corporate assets without controlling personal content.
Mobile Threat Defense detects cybersecurity threats specific to mobile platforms including malicious applications and network attacks. MTD identifies suspicious app behavior and rogue networks that might intercept traffic. Integration with MDM enables automated security responses like quarantining devices exhibiting suspicious behavior.
Wireless security controls address risks from untrusted networks that mobile devices frequently encounter. Rogue access point detection identifies unauthorized Wi-Fi networks that attackers might use to intercept traffic. VPN enforcement ensures mobile devices route traffic through encrypted tunnels when accessing corporate resources, maintaining data protection remotely.
Endpoint detection and response
Endpoint Detection and Response provides visibility into endpoint activity and enables investigation of suspicious behaviors within cybersecurity operations. EDR continuously records process executions and network connections, creating detailed timelines of endpoint activity available for forensic analysis.
When alerts fire, security analysts query EDR to understand attack sequences. Did the suspicious file execute? What processes did it spawn? EDR answers forensic questions and enables response actions including isolating endpoints, terminating processes, and collecting evidence for investigation.
Extended Detection and Response correlates endpoint telemetry with network, email, and cloud sources. XDR reveals attack chains spanning multiple systems helping security analysts understand full attack scope rather than investigating isolated endpoints without broader context.
How Cybersecurity Governance and Compliance Manage Risk
Governance provides the strategic framework directing cybersecurity programs and ensuring accountability across the organization. Compliance verifies security controls meet regulatory obligations and contractual requirements imposed by partners and customers.
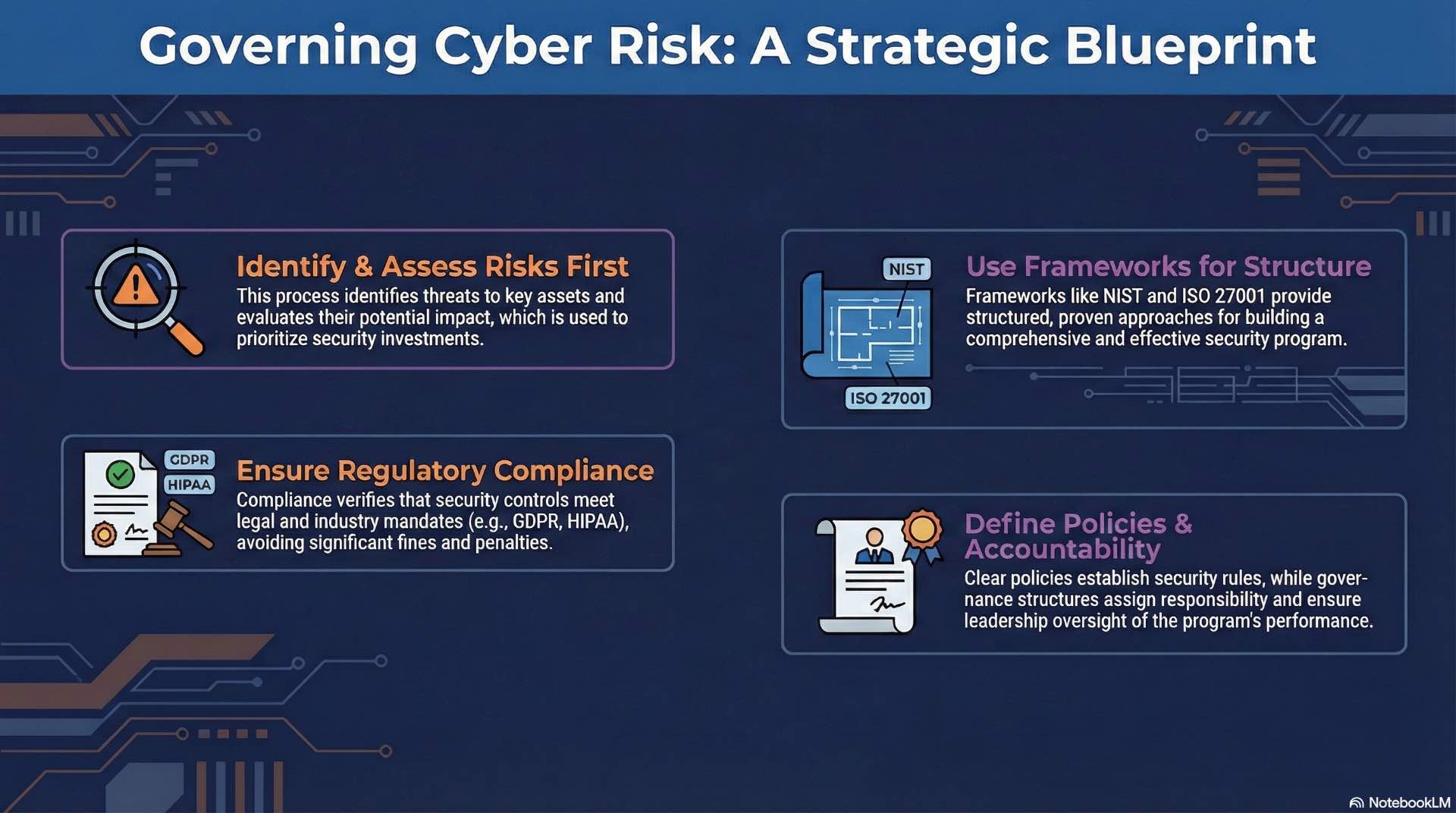
Risk assessment and security frameworks
Risk assessment identifies threats to organizational assets and evaluates likelihood and impact of potential incidents. Qualitative assessments categorize risks by severity levels while quantitative approaches estimate potential losses in financial terms enabling cost-benefit analysis of cybersecurity investments.
Security frameworks provide structured approaches to implementing full-scope programs. ISO 27001 specifies requirements for information security management covering policies, risk assessment, control selection, and continuous improvement. The NIST Cybersecurity Framework organizes protection activities into Identify, Protect, Detect, Respond, and Recover functions.
Framework selection depends on organizational context and regulatory environment. Regulated industries adopt frameworks aligned with compliance requirements while organizations serving government clients might implement NIST 800-53 controls. International operations often choose ISO 27001 for global recognition.
Regulatory compliance requirements
Industry-specific regulations mandate cybersecurity controls for sensitive information categories. HIPAA governs healthcare information security and privacy while PCI DSS specifies requirements for payment card information handling. SOX addresses financial reporting controls and GDPR covers personal information protection requirements for EU residents.
Compliance programs translate regulatory requirements into technical and operational controls. Gap assessments identify where current practices fall short of requirements. Remediation projects close gaps before audits while evidence collection demonstrates compliance to regulators and auditors.
Non-compliance carries significant consequences including regulatory fines, contractual penalties, and reputational damage. Compliance requirements often represent cybersecurity best practices so meeting obligations typically improves actual security posture beyond minimum regulatory thresholds.
Security policies and organizational governance
Security policies establish organizational requirements defining acceptable behavior and mandatory controls. High-level policies state security objectives and management commitment while standards specify required configurations and procedures provide step-by-step task instructions.
Governance structures assign accountability for cybersecurity decisions at appropriate organizational levels. Security committees prioritize initiatives and resolve conflicts between security requirements and business objectives. Boards set risk tolerance while security teams implement security controls and report on effectiveness.
Metrics and reporting enable governance oversight of cybersecurity program performance. Key indicators track vulnerability remediation and incident response times along with compliance status and program maturity. Dashboards translate technical data details into business-relevant insights for leadership audiences.
Organizational cybersecurity depends on sustained commitment across network, data, and application domains to maintain effective defenses. Technical security controls block attacks, but governance ensures those controls align with business risk tolerance and regulatory requirements. Effective cybersecurity requires layered data protection working together so that weaknesses in one area don’t compromise the entire security posture. Security teams must continuously monitor emerging threats, evaluate new defensive technologies, and adapt programs to address evolving threat conditions. Organizations that invest in layered security controls across all security domains and maintain mature governance frameworks position themselves to withstand the inevitable attacks they will face.





