Cybersecurity in banking and financial services focuses on strong data protection and fraud prevention to secure digital channels and customer trust.
Modern cybersecurity challenges in banking institutions demand integrated defenses that combine technical controls with operational discipline. Financial services organizations face constant pressure from sophisticated attackers who target customer accounts, transaction systems, and sensitive records. Strong data protection and fraud prevention capabilities form the foundation of customer trust. The shift to digital channels, mobile apps, and cloud infrastructure expands the attack surface while raising customer expectations for seamless, secure experiences.
Banks and other financial institutions operate in a heavily regulated environment where compliance failures can result in penalties, reputational damage, and lost customer confidence. Effective cybersecurity strategies balance regulatory requirements with practical risk management, recognizing that security controls must enable business operations rather than obstruct them. The challenge lies in protecting critical assets while maintaining the speed and flexibility that competitive financial services demand.
This article explores cybersecurity as a layered discipline that spans network architecture, access controls, encryption, fraud detection, and security operations. The discussion covers both preventive measures and detective capabilities, showing how financial institutions can build resilient defenses against evolving threats.
Why Cybersecurity Matters in Banking and Financial Services
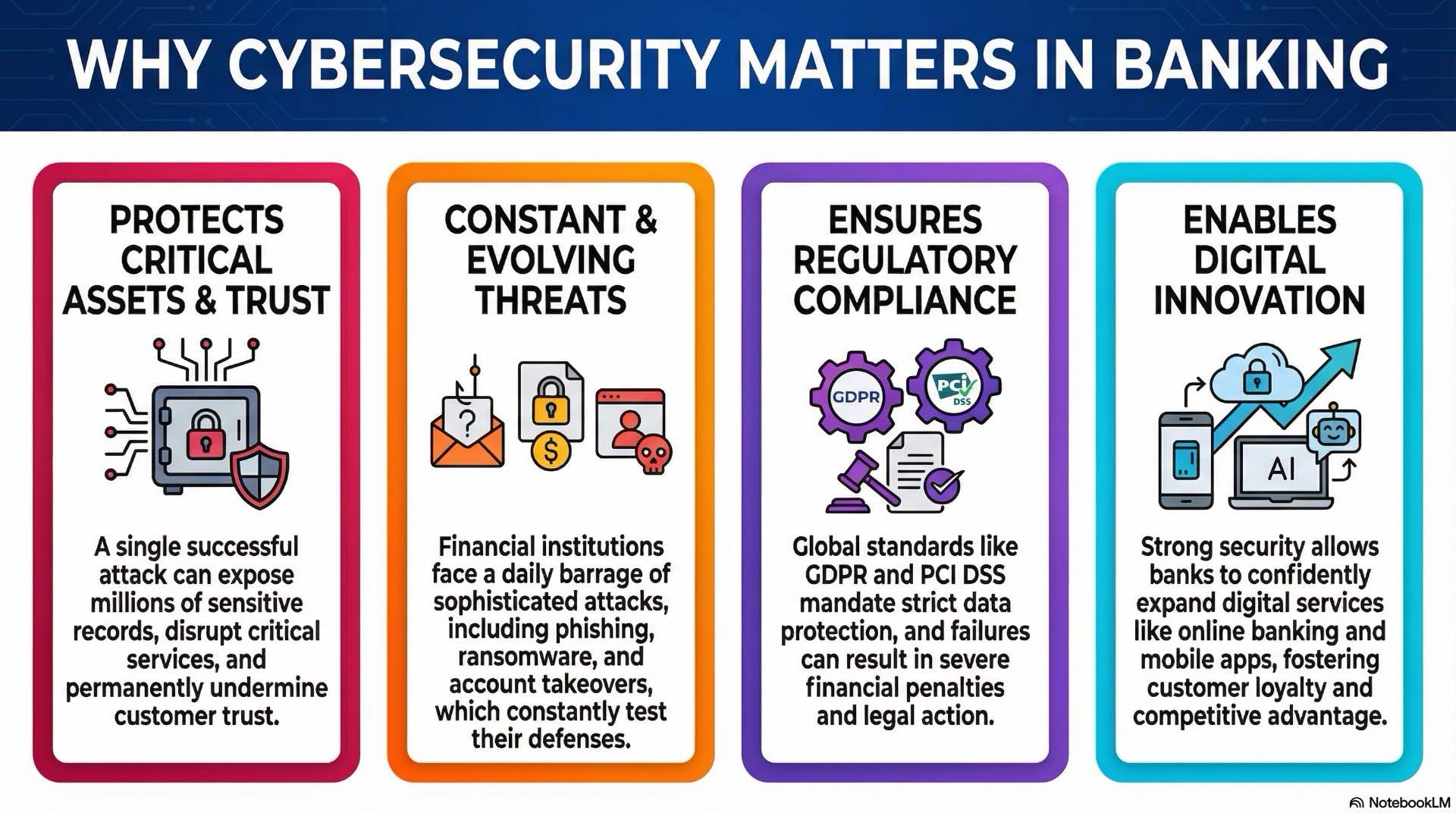
Financial institutions store and process large volumes of sensitive data, from account information to transaction records and portfolios. A successful cyberattack can expose millions of records, disrupt critical services, and undermine customer trust built over decades. The consequences extend beyond immediate financial losses to include regulatory investigations, lawsuits, and long-term brand damage.
Digital transformation accelerates these risks. Online banking, mobile payment apps, and open banking APIs create new entry points for attackers. Each new channel adds complexity to the security perimeter and increases the potential for misconfiguration or oversight. The reality is that modern banking happens across multiple platforms, devices, and geographic locations, making traditional perimeter defenses insufficient.
Cybersecurity in banking and financial services functions as both a defensive mechanism and an enabler of innovation. Strong security controls allow financial services organizations to expand digital services confidently, knowing that customer data and transaction integrity remain protected. The investment in security infrastructure pays dividends through reduced incident costs, faster regulatory approvals, and improved customer loyalty.
Threat Landscape for Banking and Financial Institutions

Common cyber attack types in financial services
Phishing attacks remain one of the most effective methods for compromising banking systems. Attackers craft convincing emails that mimic legitimate communications from financial services providers, tricking employees or customers into revealing credentials. These campaigns often target specific individuals with access to critical systems, using information gathered from social media or previous data breaches to increase credibility.
Account takeover attacks exploit weak authentication mechanisms or stolen credentials to gain unauthorized access to customer accounts. Once inside, attackers can initiate fraudulent transactions, modify account details, or extract funds before detection. Financial services firms see thousands of these attempts daily, requiring robust monitoring systems to identify suspicious login patterns and transaction behaviors.
Ransomware poses a severe threat to operational continuity. A successful ransomware deployment can encrypt critical banking systems, halt transaction processing, and prevent customer access to accounts. The decision to pay ransom or restore from backups carries significant implications for business continuity and regulatory compliance. Many financial services institutions now maintain offline backups and regularly test recovery procedures to minimize ransomware impact. Strong backup strategies support both disaster recovery and fraud prevention objectives.
Distributed denial-of-service attacks aim to overwhelm online banking platforms and prevent legitimate customer access. While these attacks typically do not result in data theft, they disrupt services, damage customer confidence, and often serve as distractions while attackers pursue more serious objectives. Financial services availability represents a critical business requirement. Modern DDoS attacks can generate massive traffic volumes that challenge even well-provisioned infrastructure.
Emerging threats and advanced attack techniques
Supply chain compromises represent a growing concern for financial institutions that rely on third-party software, hardware, and services. Attackers inject malicious code into trusted vendor products, gaining access to banking networks through legitimate channels. These attacks are particularly difficult to detect because the compromised components often have authorized access to sensitive systems.
Advanced persistent threats demonstrate patience and sophistication that distinguishes them from opportunistic attackers. These campaigns unfold over months or years, with attackers gradually expanding access, mapping internal systems, and positioning themselves to extract maximum value. Financial institutions must implement layered defenses including cybersecurity monitoring and fraud prevention systems to detect these threats early. Institutions must assume persistent adversaries exist within their networks and design defenses accordingly.
Insider threats combine authorized access with malicious intent or negligence. Employees with legitimate system access can exfiltrate customer data, manipulate transactions, or sabotage operations. Organizations must implement strong data protection and fraud prevention controls that address insider risks. The challenge lies in distinguishing normal work patterns from suspicious activities without creating a hostile work environment that undermines productivity.
API vulnerabilities emerge as financial institutions expose functionality to third-party developers and partners. Poorly designed or inadequately secured APIs can leak sensitive data, allow unauthorized transactions, or provide entry points for broader network compromise. The rapid growth of financial technology partnerships increases this exposure. These evolving attack techniques pressure financial services organizations to update controls continuously.
Regulatory and Compliance Frameworks in Financial Cybersecurity
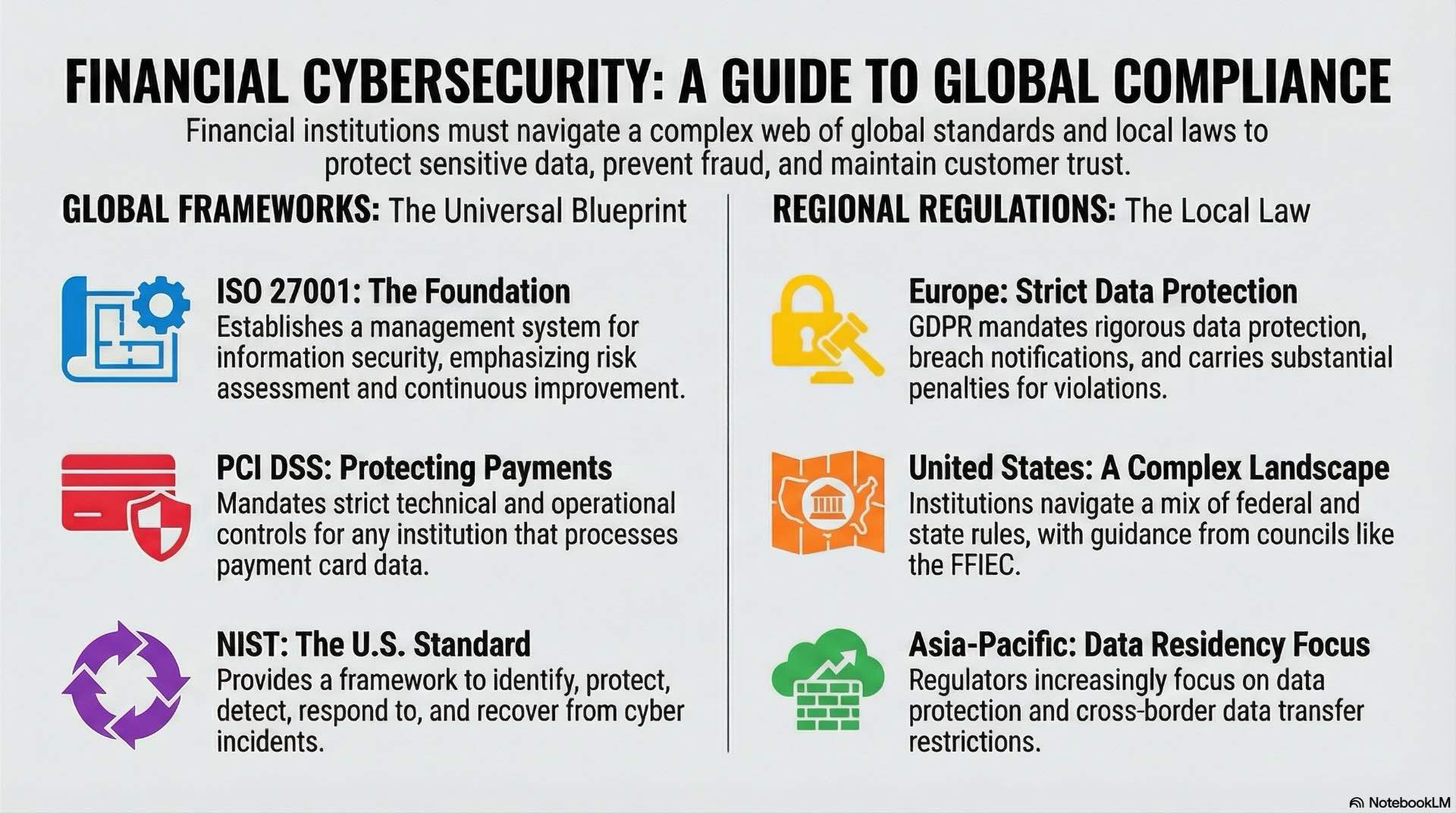
Global standards such as ISO 27001, PCI DSS and NIST
ISO 27001 provides a comprehensive framework for information security management systems that many financial institutions adopt as their foundation. The standard emphasizes risk assessment, control implementation, and continuous improvement through regular audits and reviews. Certification demonstrates to customers and regulators that the organization takes security seriously and follows recognized best practices.
Data protection requirements under PCI DSS specifically address payment card processing and storage. Financial institutions that handle card transactions must comply with detailed technical and operational controls covering network segmentation, encryption, access control, and monitoring. PCI compliance forms a critical component of comprehensive data protection programs. Regular assessments verify ongoing compliance and identify areas requiring improvement.
NIST frameworks offer detailed guidance on cybersecurity controls suitable for critical infrastructure and financial services. The NIST Cybersecurity Framework helps organizations identify, protect, detect, respond to, and recover from cyber incidents through structured processes and measurable outcomes. Many regulators reference NIST standards when evaluating institutional security programs. GDPR has become a reference point for data protection obligations worldwide.
These frameworks share common principles around defense in depth, least privilege access, and continuous monitoring. Strong data protection and fraud prevention capabilities form the foundation of regulatory compliance. The reality is that compliance alone does not guarantee security, but it establishes a baseline that reduces common vulnerabilities and provides structure for security programs.
Local banking regulations and supervisory expectations
National banking regulators impose specific cybersecurity requirements that reflect local risk environments and policy priorities. European institutions operate under GDPR requirements that mandate strict data protection measures, breach notification procedures, and customer consent mechanisms. Strong data protection compliance reduces legal exposure and builds customer confidence. Violations carry substantial penalties calculated as percentages of global revenue.
United States financial institutions navigate a complex regulatory landscape with federal agencies, state regulators, and industry-specific rules. The Federal Financial Institutions Examination Council provides guidance through its cybersecurity assessment tool, while individual regulators impose examination procedures and enforcement actions. Recent guidance emphasizes third-party risk management and incident response preparedness.
Asian-Pacific regulators increasingly focus on data protection and cross-border data transfer restrictions. Singapore, Hong Kong, and Australia have implemented comprehensive frameworks that require financial institutions to demonstrate adequate security controls, conduct regular testing, and report significant incidents within tight timeframes. Local data protection laws often impose residency requirements for customer data storage.
Regulatory expectations continue to evolve as threats change and incidents expose weaknesses. Data protectionrequirements become stricter as privacy concerns grow globally. Financial institutions must maintain awareness of pending regulatory changes and adjust security programs proactively rather than reacting to enforcement actions.
Security Architecture for Financial Institutions
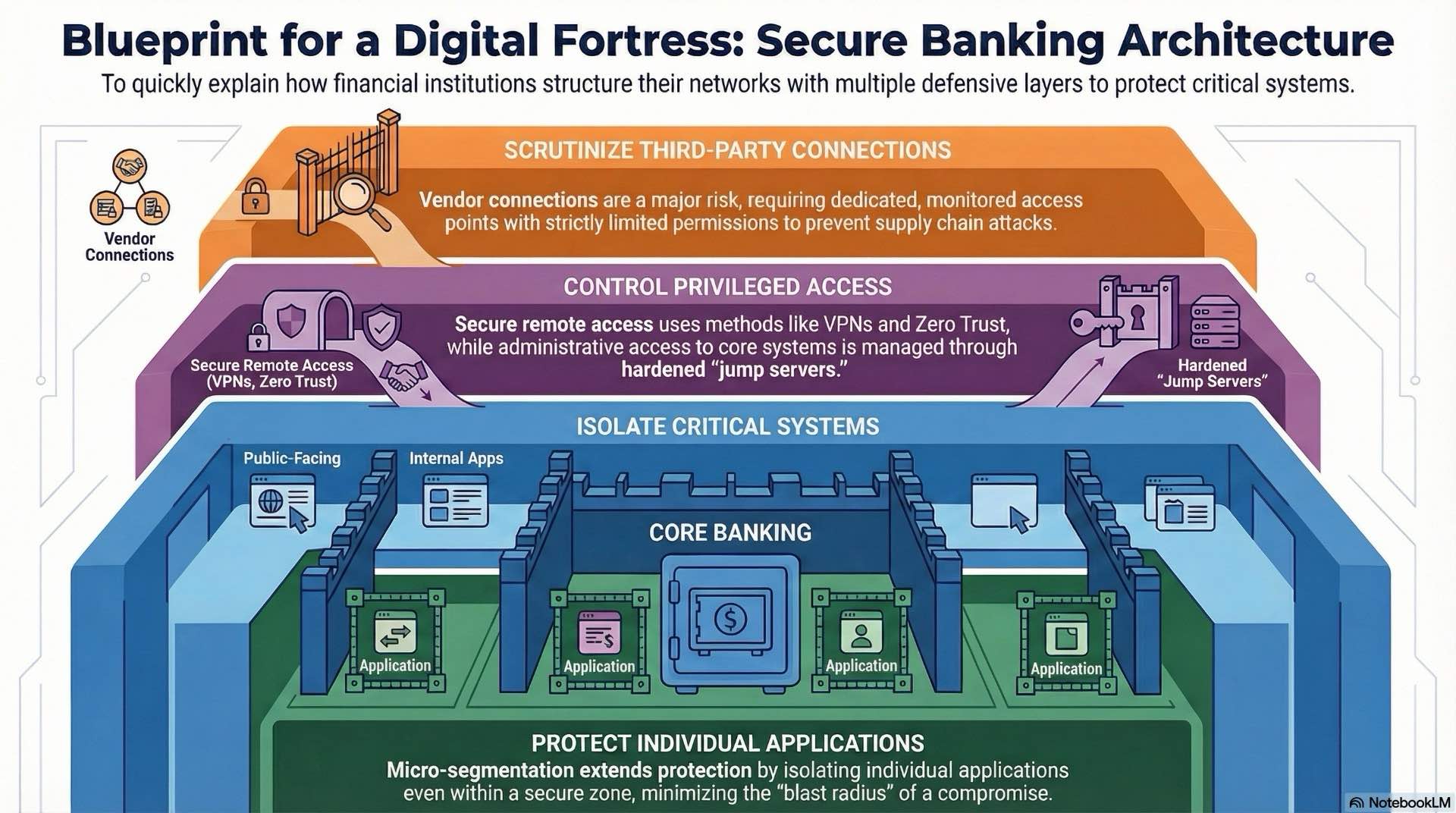
Network segmentation and secure security zones
Proper network segmentation isolates critical banking systems from less sensitive infrastructure and external connections. Core banking platforms, payment processors, and customer databases reside in highly restricted zones with carefully controlled access paths. This architecture limits lateral movement opportunities for attackers who compromise perimeter systems.
Security zones typically include external-facing web servers and APIs in a demilitarized zone, internal application servers in a protected zone, and core banking systems in a highly restricted zone. Each zone implements appropriate controls based on the sensitivity of systems and data it contains. This layered approach forms the foundation of financial services network security. Firewalls, intrusion prevention systems, and access control lists enforce zone boundaries.
The design must account for legitimate business flows while preventing unauthorized access. Transaction processing requires controlled pathways between customer-facing systems and backend databases. The challenge lies in maintaining security without introducing latency that degrades user experience or prevents real-time processing.
Micro-segmentation extends this concept within zones, creating isolated environments for individual applications or services. This approach limits blast radius when compromise occurs and simplifies security policy management by grouping systems with similar risk profiles and control requirements. Proper segmentation supports both cybersecurity and fraud prevention objectives by containing incidents quickly.
Secure remote access and third-party connectivity
Remote access for employees, contractors, and third-party service providers requires robust authentication and encryption. Virtual private networks create secure tunnels through public networks, protecting sensitive traffic from interception. Modern zero-trust approaches verify every connection attempt regardless of network location or previous authentication.
Third-party connections pose particular challenges because financial institutions must balance business requirements with security concerns. Service providers need sufficient access to perform contracted functions but should not have unrestricted network access. Many financial services organizations now require vendors to undergo security assessments before connectivity. Dedicated connection points with carefully scoped permissions and continuous monitoring reduce third-party risk.
Jump servers and privileged access workstations provide controlled pathways for administrative access to critical systems. These hardened platforms limit attack opportunities by restricting available tools, logging all activities, and requiring strong authentication. Administrators cannot bypass these controls even during emergency situations.
Remote access policies should enforce least privilege principles, granting only the minimum permissions necessary for specific tasks. Strict access controls protect both operational security and data protection objectives. Time-limited access credentials expire automatically, requiring renewal for extended work sessions. This approach reduces exposure from compromised credentials and ensures that access rights remain current.
Identity, Access and Authentication Controls
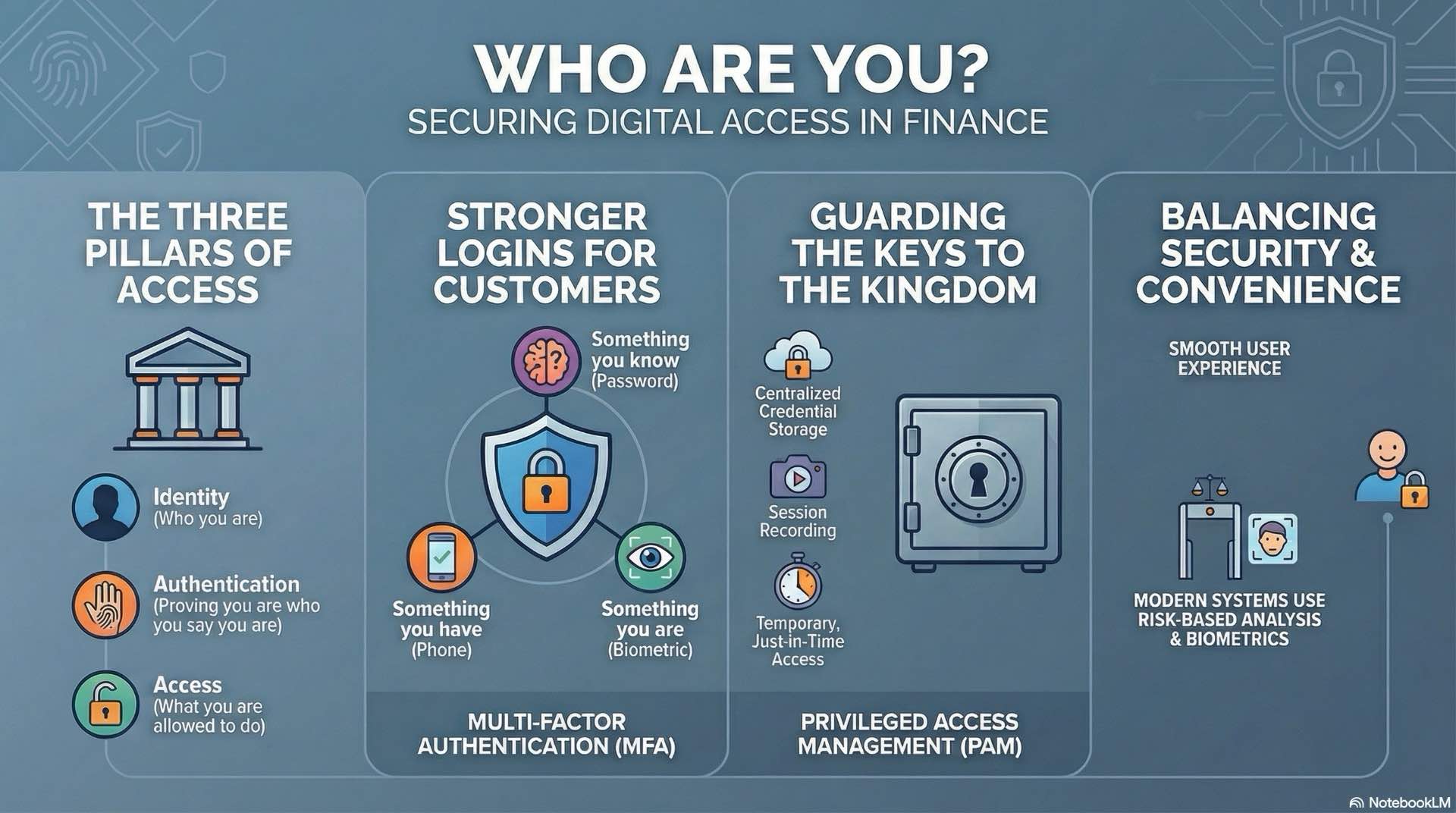
Strong customer authentication and multi-factor login
Multi-factor authentication combines something the user knows (password), something they have (token or phone), and something they are (biometric) to verify identity. Financial institutions increasingly mandate MFA for online banking access, recognizing that passwords alone provide insufficient protection against credential theft and account takeover.
Implementation must balance security with usability. Customers resist authentication methods that feel cumbersome or unreliable. Modern approaches use risk-based authentication that applies additional verification only when transaction patterns or login contexts trigger suspicion. This balance proves critical for financial services competitiveness. Low-risk actions proceed with minimal friction while high-risk transactions require stronger authentication.
Biometric authentication offers improved user experience by eliminating password memorization while providing strong security. Fingerprint readers, facial recognition, and voice authentication have become standard features in mobile banking applications. Biometric systems enhance both user convenience and fraud prevention effectiveness. The technology must include liveness detection to prevent spoofing attacks using photographs or recordings.
Fraud prevention systems analyze authentication attempts in real time, comparing current login behavior against historical patterns. Geographic location, device fingerprints, network characteristics, and timing all contribute to risk scoring. Suspicious attempts trigger additional verification steps or temporary account locks pending investigation.
Privileged access management in core banking systems
Privileged accounts with administrative rights to core banking systems require enhanced controls beyond standard user authentication. These accounts can modify system configurations, access sensitive data, and bypass normal security controls. Compromise of privileged credentials represents a critical risk that could result in massive data breaches or system manipulation.
Privileged access management platforms centralize credential storage, enforce approval workflows, and record all administrative actions. Administrators request temporary access for specific tasks rather than maintaining persistent elevated privileges. The system automatically revokes access when the approved timeframe expires or the task completes.
Session recording captures detailed keystroke logs and screen activity during privileged sessions. Security teams can review recordings to detect policy violations, investigate incidents, or verify that authorized changes were implemented correctly. Session monitoring supports both internal audits and fraud prevention investigations. The knowledge that sessions are recorded also serves as a deterrent against malicious insider activity.
Just-in-time provisioning eliminates standing privileged accounts entirely. When administrative access is required, the system creates temporary credentials with precisely scoped permissions, then destroys them after use. This approach enhances data protection by minimizing credential exposure windows and reducing opportunities for credential theft or misuse.
Data Protection for Financial Information
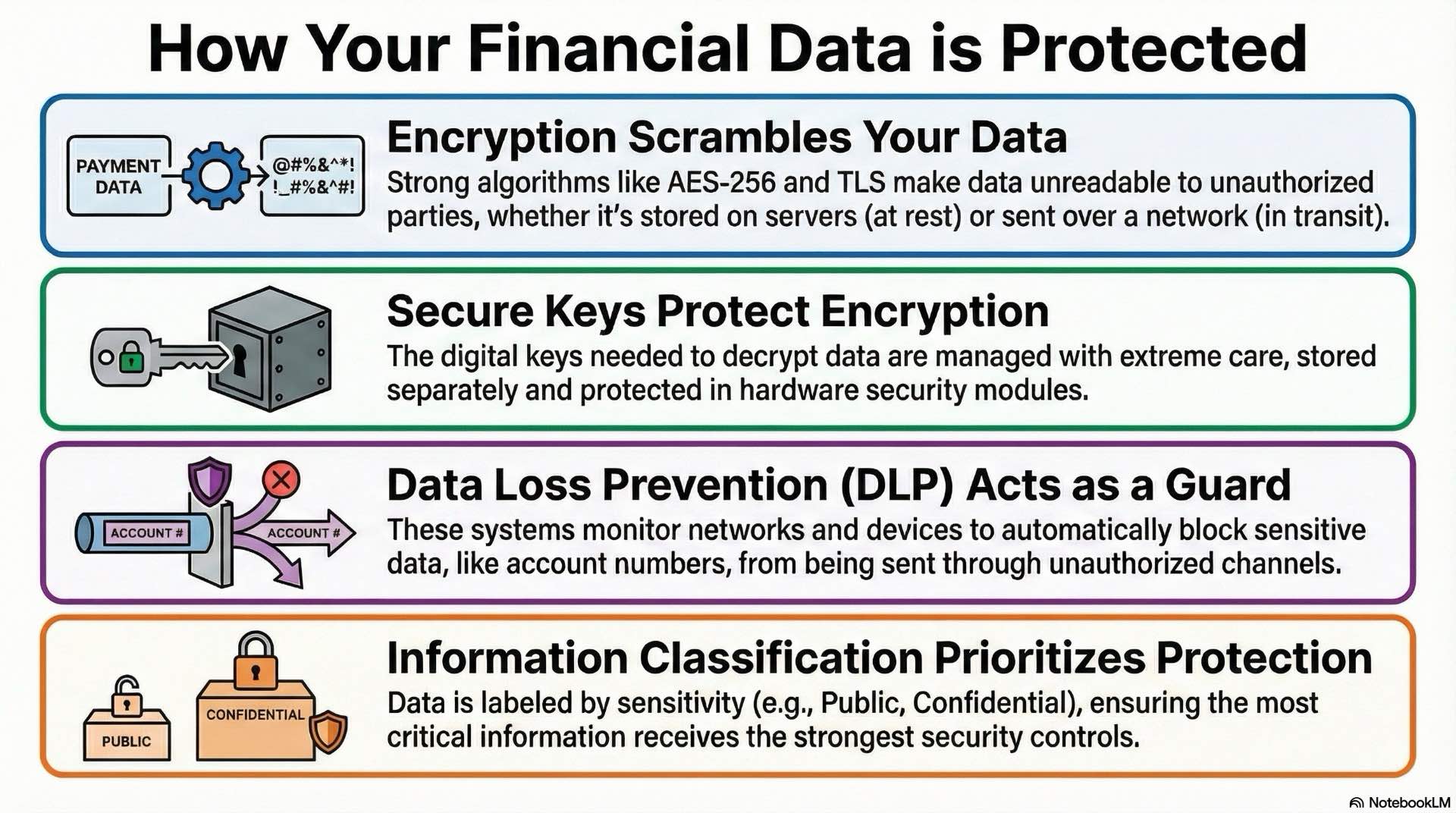
Encryption of data at rest and in transit
Encryption protects sensitive financial data from unauthorized access during storage and transmission. Industry-standard algorithms like AES-256 for stored data and TLS for network traffic provide computational security that renders encrypted information useless without proper decryption keys. Financial institutions must encrypt customer account information, transaction records, and personal identification data across all systems to meet data protection obligations.
Key management represents the most critical aspect of encryption deployment. Encryption keys must be stored separately from encrypted data, protected by hardware security modules or key management services. Proper data protection depends on secure key lifecycle management. Regular key rotation limits exposure from potential key compromise while maintaining backward compatibility for data encrypted under previous keys.
Database-level encryption applies protection to entire database files or specific tables containing sensitive information. This approach simplifies key management and ensures consistent coverage but can impact query performance. Effective data protection strategies balance security with system performance requirements. Column-level encryption offers more granular control, protecting individual data elements while allowing unrestricted access to non-sensitive columns.
Transport encryption protects data moving between systems, across networks, or through APIs. Strong cipher suites prevent eavesdropping and man-in-the-middle attacks. Comprehensive data protection includes both storage and transport encryption. Certificate validation confirms the identity of communication endpoints and prevents connections to imposter systems.
Data loss prevention and information classification
Data loss prevention systems monitor network traffic, endpoint activity, and storage systems for sensitive information moving through unauthorized channels. These tools identify credit card numbers, account identifiers, and personal information based on patterns and context, then block or quarantine suspicious transfers for review. Proper data protection strategies combine DLP with encryption and access controls.
Information classification frameworks label data according to sensitivity and regulatory requirements. Public information receives minimal protection while confidential customer data requires encryption, access restrictions, and audit logging. Effective data protection requires clear classification and consistent policy enforcement. Clear classification enables appropriate control application without over-protecting low-sensitivity information or under-protecting critical assets.
Email filtering examines outbound messages for sensitive data attachments or content that could indicate data exfiltration. Policies can block, quarantine, or require approval for messages containing classified information. Email remains a primary vector for data protection breaches. The system maintains detailed logs of all actions taken, supporting both security investigations and compliance reporting.
Endpoint agents monitor file operations, clipboard activity, and removable media connections for unauthorized data transfers. When users attempt to copy sensitive files to USB drives or cloud storage services, the agent can block the action or require justification and approval. These endpoint controls extend data protection beyond the network perimeter to individual devices.
Fraud Prevention and Transaction Security
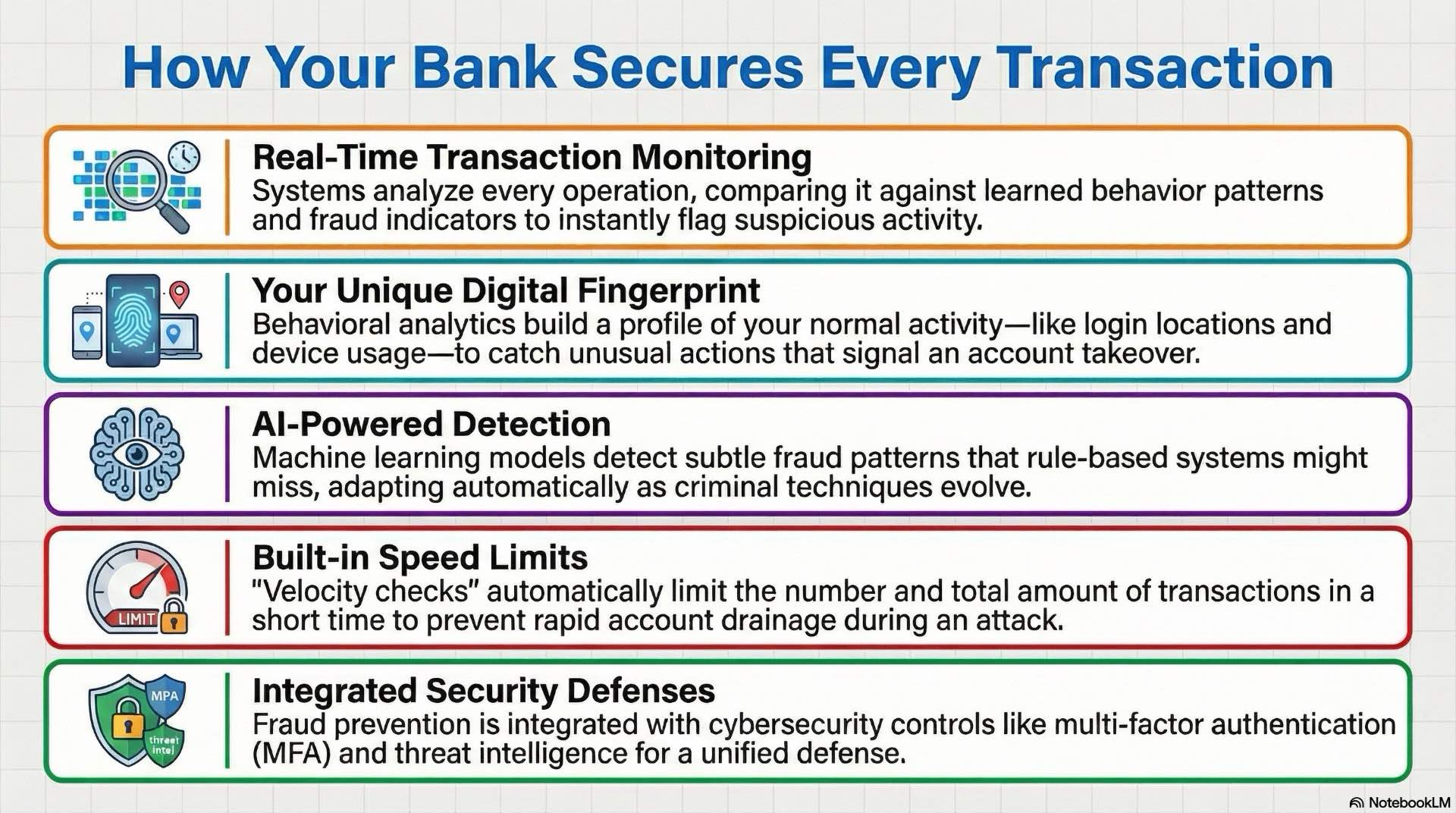
Online and mobile banking transaction monitoring
Transaction monitoring systems analyze every banking operation in real time and compare activity against learned behavior patterns and fraud indicators. Unusual transaction amounts, beneficiaries, or timing trigger alerts that can pause transactions pending additional verification. Effective fraud prevention balances security with customer convenience, minimizing false positives that frustrate legitimate users.
Machine learning models detect subtle patterns that rule-based systems might miss. These models learn from historical transaction data, identifying correlations between specific behaviors and fraud outcomes. As fraud techniques evolve, the models adapt without requiring manual rule updates. These models now sit at the core of digital fraud preventionstrategies. The challenge lies in maintaining model accuracy while managing the volume of alerts security teams must review.
Behavioral analytics build profiles of normal activity for each customer account. Sudden changes in transaction patterns, login locations, or device usage suggest potential compromise. Modern fraud prevention relies heavily on these behavioral signals. The system can automatically impose temporary restrictions while notifying customers through verified communication channels. This approach catches account takeover attempts before significant losses occur.
Velocity checks limit transaction counts and aggregate amounts within defined timeframes. If an account suddenly executes many transfers or withdraws large sums, the system intervenes regardless of whether individual transactions appear suspicious. These controls prevent rapid account drainage that could occur during the window between compromise and detection. Fraud prevention velocity rules adapt based on account history and customer behavior patterns.
Integrating fraud detection with cybersecurity controls
Effective fraud prevention requires coordination between fraud operations teams and cybersecurity functions across financial services organizations. Fraud indicators often signal broader security incidents, while cybersecurity alerts can predict upcoming fraud attempts. Shared visibility into threats and incidents enables faster response and more comprehensive protection.
Security information and event management platforms aggregate logs from fraud detection systems, authentication platforms, and network security controls. Correlation rules identify connections between seemingly unrelated events, revealing coordinated attack campaigns. A failed login attempt followed by a password reset request and then suspicious transactions might indicate social engineering combined with account takeover.
Threat intelligence feeds inform fraud and security teams about new attack techniques, credential dumps, and malware families targeting financial institutions. This information guides defensive priorities and enables proactive controls before attacks occur. Intelligence sharing enhances both cybersecurity and fraud prevention capabilities. Sharing indicators between institutions through industry groups multiplies the effectiveness of threat intelligence.
Incident response procedures must account for fraud scenarios specifically. Traditional cybersecurity incidents focus on containing malware and restoring systems, while fraud incidents require immediate transaction reversal, customer notification, and coordination with law enforcement. Effective fraud prevention includes both proactive controls and rapid incident response. Separate playbooks address these distinct requirements while maintaining overall coordination.
Security Operations and Monitoring in Financial Services

SIEM, SOC and use of threat intelligence
Security operations centers provide 24/7 monitoring of security events across financial institution networks. Analysts review alerts from intrusion detection systems, authentication platforms, and endpoint protection tools, investigating potential incidents and coordinating response activities. SOC analysts coordinate closely with fraud prevention teams when transaction anomalies appear. The SOC serves as the central nervous system for cybersecurity operations, maintaining awareness of current threats and defensive status.
SIEM platforms collect and analyze logs from diverse sources throughout the environment. Advanced correlation capabilities identify attack patterns that manifest across multiple systems and timeframes. For large financial servicesinstitutions, SIEM platforms must scale to billions of daily events. The platform enriches raw security events with context from threat intelligence, asset inventories, and user directories, helping analysts prioritize investigations.
Threat intelligence integration provides context about attacker tactics, techniques, and procedures. Financial services organizations subscribe to commercial feeds, participate in information sharing groups, and maintain internal threat research capabilities. Current intelligence about active campaigns targeting the financial sector guides defensive priorities and enables faster incident detection.
Automated response capabilities allow security operations teams to contain threats at machine speed. When the SIEM identifies a compromised account, automated workflows can disable the account, terminate active sessions, and notify relevant security personnel simultaneously. Automation accelerates both incident response and fraud preventionactions. This reduces the window between detection and containment from hours to seconds.
Incident response planning and tested playbooks
Incident response plans define roles, responsibilities, and procedures for handling security incidents of various types and severities. Plans address technical response actions alongside communication requirements, regulatory notifications, and business continuity considerations. Regular testing through tabletop exercises and simulations reveals gaps and builds muscle memory for crisis situations.
Playbooks provide step-by-step procedures for specific incident types, from ransomware infections to data breaches to DDoS attacks. Each playbook specifies decision points, escalation paths, and success criteria. Specialized playbooks address fraud prevention scenarios that require rapid financial transaction controls. Detailed documentation ensures consistent response even when key personnel are unavailable or incidents occur simultaneously.
Post-incident reviews analyze response effectiveness, identify lessons learned, and drive continuous improvement. Root cause analysis determines how attackers gained access and what additional controls could prevent recurrence. The financial impact of incidents informs future security investments and risk prioritization. Many financial servicesregulators now require documented post-incident reviews.
Regulatory reporting requirements demand rapid incident assessment and notification. Financial institutions must determine within hours whether an incident constitutes a reportable event under various regulatory frameworks. Pre-established communication channels with regulators, legal teams, and executive management enable fast, accurate reporting.
Governance, Risk Management and Cybersecurity Roadmap
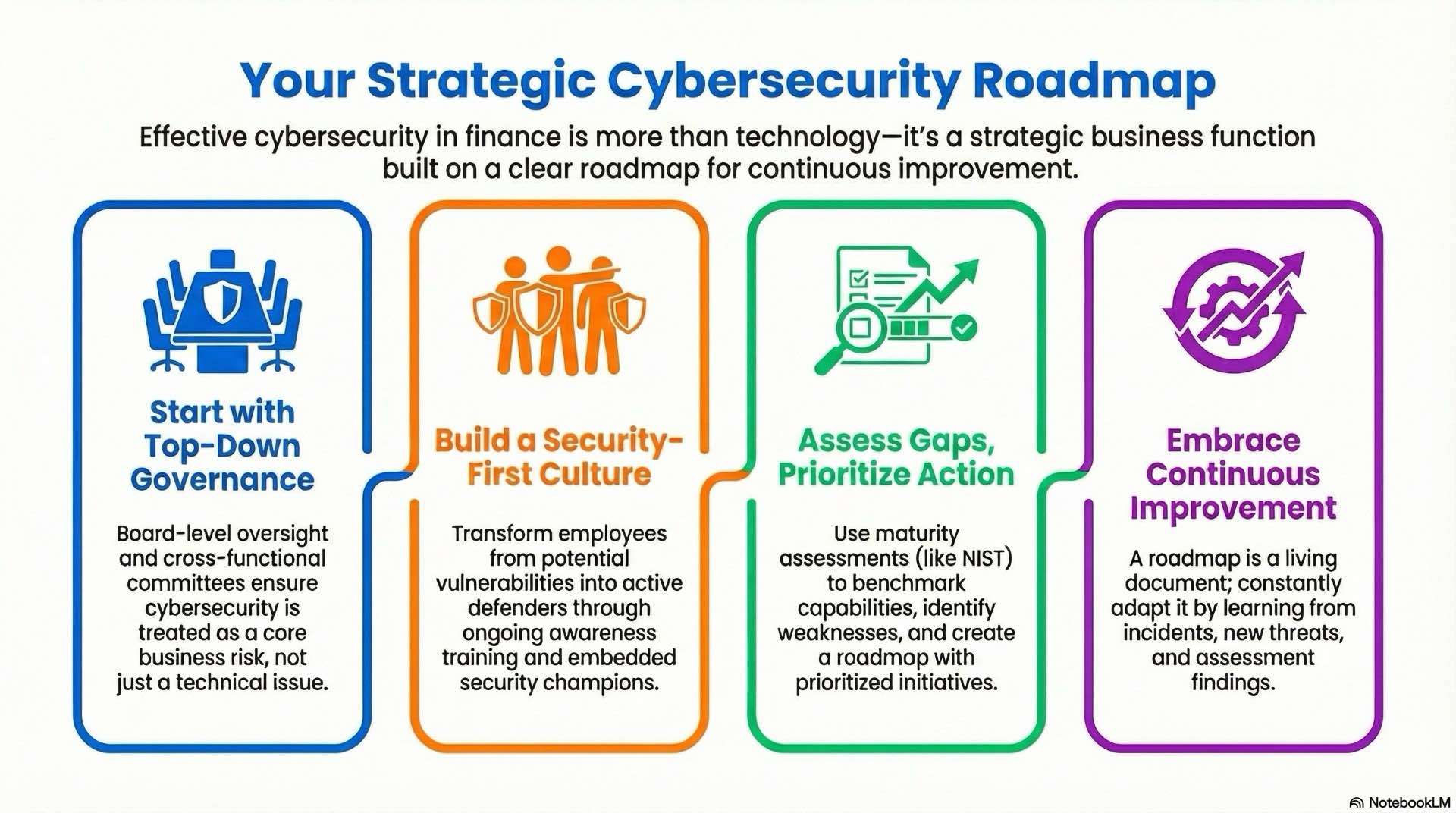
Roles, responsibilities and security culture in banking
Board-level oversight ensures cybersecurity receives appropriate attention and resources. Directors review key risk indicators, major incidents, and security program investments regularly. Clear reporting lines from chief information security officers to executive management emphasize that cybersecurity represents a business risk, not merely a technical concern.
Cross-functional security committees coordinate activities across information technology, operations, compliance, and business units. These forums resolve policy conflicts, prioritize initiatives, and ensure security considerations influence business decisions. Representation from multiple disciplines prevents security from becoming isolated or disconnected from institutional objectives.
Security awareness training transforms employees from potential vulnerabilities into active defenders. Regular training covers phishing recognition, password hygiene, and reporting procedures. Training should address both cybersecurity threats and fraud prevention techniques employees can apply. Simulated attacks test employee readiness and identify areas requiring additional education. The goal extends beyond compliance checkboxes to genuine behavioral change.
Security champions embedded within business units and technology teams advocate for security considerations during project planning and system design. These individuals understand both security principles and operational realities, bridging the gap between security teams and the broader organization. Champions often coordinate closely with fraud prevention specialists on customer-facing applications. Their influence ensures security becomes integral rather than an afterthought.
Maturity assessments and continuous improvement initiatives
Regular maturity assessments benchmark current capabilities against industry standards and best practices. Financial institutions use frameworks like the NIST Cybersecurity Framework or FFIEC assessment tool to identify gaps and track progress. Risk dashboards should highlight data protection gaps alongside other cyber risks. These evaluations inform strategic planning and demonstrate improvement to regulators and stakeholders.
Cybersecurity roadmaps translate assessment findings into prioritized initiatives with defined timelines, resource requirements, and success metrics. The roadmap balances quick wins that address immediate vulnerabilities with longer-term architectural improvements that strengthen overall resilience. Executive support and adequate funding enable consistent progress.
Continuous improvement processes incorporate lessons from incidents, assessment findings, and emerging threats. Security teams regularly review and update controls, policies, and procedures based on changing risk profiles. Organizations should integrate fraud prevention lessons into broader security improvement cycles. This adaptive approach ensures defenses remain effective as attack techniques evolve and business requirements change.
Investment in security capabilities must keep pace with digital transformation initiatives. As financial services organizations expand services, enter new markets, or adopt emerging technologies, cybersecurity resources scale accordingly. The alternative creates security debt that accumulates until a major incident forces reactive spending.
Modern financial services depend on robust cybersecurity that meets data protection requirements while enabling innovation. Success requires sustained investment, cross-functional collaboration, and adaptive strategies that anticipate emerging threats. Banking institutions that embed security throughout operations rather than treating it as a compliance checkbox build customer trust and competitive advantage. The integration of fraud prevention with technical security controls creates comprehensive defense against both external attackers and internal risks.





