Alarm system enhances security by using detection devices to identify intrusion and burglar events, activating alerts through a central control panel.
An alarm system provides layered protection through intrusion detection, automated response, and continuous monitoring of secured spaces. These security systems use sensors to identify burglar activity, forced entry attempts, and covert bypass techniques before significant losses occur. When detection devices sense movement or unauthorized access, the control panel processes signals and activates sirens, strobes, and notifications to monitoring centers. Modern alarm system platforms range from basic unmonitored local sounders to professionally monitored solutions with dual-path signaling, video verification, and smart home integration.
The effectiveness of any alarm system depends on proper security design, strategic sensor placement, and reliable communication paths meeting UL 681 and EN 50131 standards. Control panels evaluate inputs from sensors distributed across multiple zones while resisting panel tampering and signal jamming attempts. Communication modules transmit burglar alarm and intrusion signals through IP, cellular, or hybrid paths to monitoring centers around the clock. The architecture must include backup power, encrypted transmission, and redundant signaling to maintain detection capabilities during power outages or communication failures.
This cornerstone guide covers alarm system types, intrusion detection methods, verification techniques, communication reliability, industry standards, and smart security integration. Security engineers and alarm technicians will find practical information for designing and maintaining burglar alarm systems across residential, commercial, and industrial environments.
What Is Alarm System and How It Works
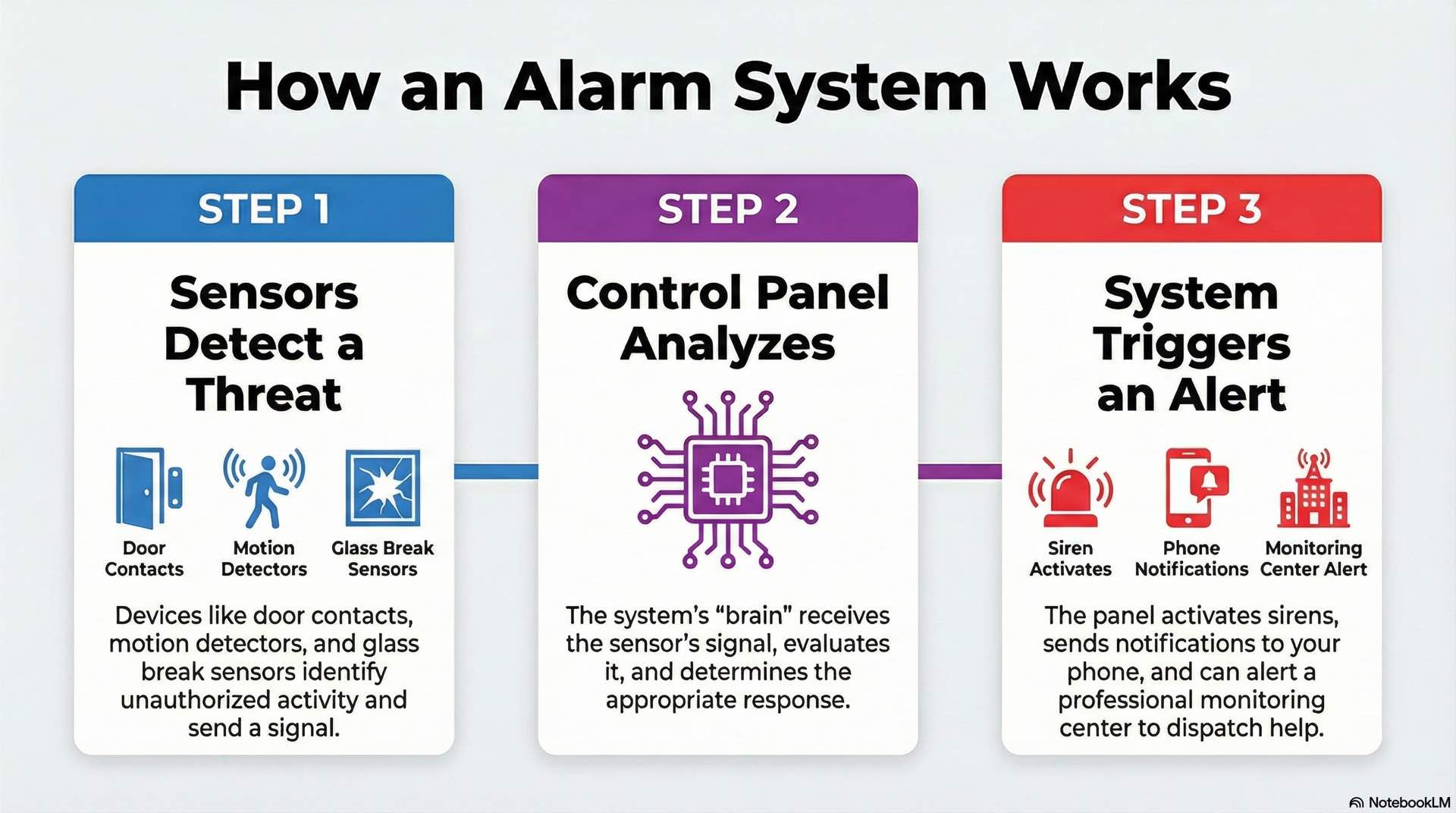
Alarm system functions and threat identification
An alarm system performs three core functions: detect threats, process signals, and initiate responses. Intrusion detection begins at the sensor level, where devices monitor door position, motion in protected areas, or glass breakage. Each security sensor translates physical events into electrical signals traveling to the control panel through wired connections or wireless radio links.
The control panel evaluates incoming signals against programmed parameters. When a sensor reports a condition matching burglar alarm criteria, the panel determines the appropriate response based on system configuration. Responses include activating local sirens, transmitting signals to monitoring centers, and sending push notifications to authorized users. The panel logs each detection event with timestamps for investigation and compliance purposes.
Alarm systems fall into two primary categories based on monitoring approach. Monitored alarm systems connect to professional central stations where trained operators verify events and dispatch emergency services. Unmonitored systems rely on local sirens and self-notification through mobile apps, placing response responsibility entirely on the property owner. Most security professionals recommend monitored systems for reliable burglar detection and rapid emergency response.
Detection roles and response workflow
The detection layer creates a virtual security perimeter around protected assets. Perimeter sensors monitor entry points like doors, windows, skylights, and roof hatches. Interior intrusion sensors provide backup by detecting movement within the facility after perimeter breach. Environmental sensors extend detection coverage to smoke, heat, carbon monoxide, and gas hazards.
Response workflow follows a defined sequence when the alarm system detects an intrusion event. Sensor activation generates an alarm condition at the control panel. Entry delays allow authorized users time to reach the keypad and disarm the security system. If no valid code is entered, the panel escalates to full alarm status. Local notification devices activate immediately. Communication modules transmit detection signals to monitoring centers within seconds.
Monitoring centers use Enhanced Call Verification (ECV) protocols before dispatching police. Operators attempt to reach the premises and at least one additional contact before requesting emergency response. This verification step reduces false dispatches while ensuring genuine burglar intrusion events receive immediate attention. Many jurisdictions now require ECV compliance for alarm system permits.
Alarm System Technologies and Intrusion Protection Methods
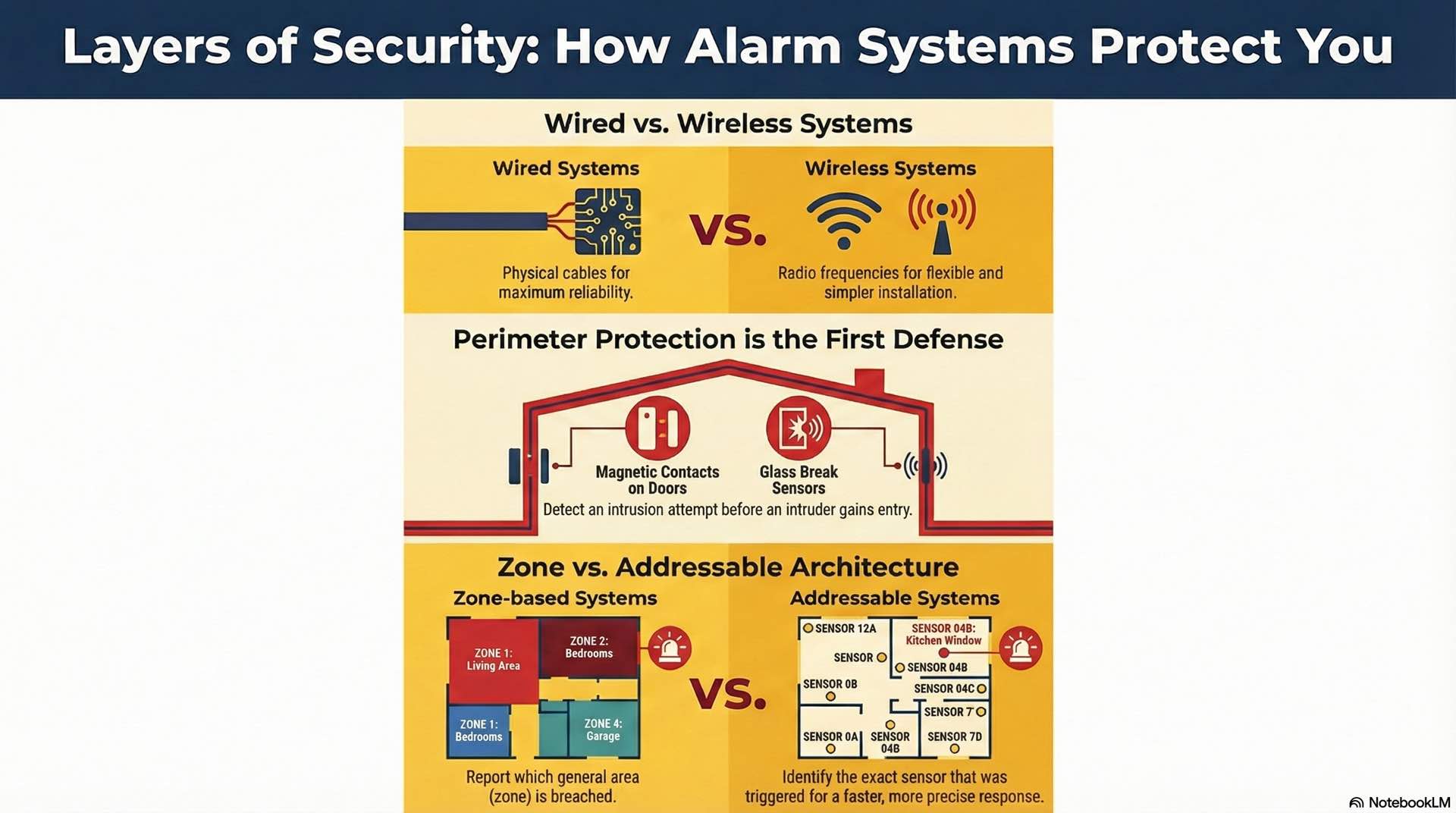
Wired and wireless alarm system formats
Wired alarm systems connect sensors to the control panel using physical cables, typically four-conductor or six-conductor alarm cable. This approach provides highly reliable communication with minimal signal interference and immunity to radio frequency jamming. Wired burglar alarm systems suit new construction where cables can be routed before walls are closed.
Wireless alarm systems use radio frequency transmission between sensors and panel. Modern wireless intrusion detection sensors operate on encrypted frequencies designed to penetrate building materials while resisting interference. Battery-powered sensors simplify installation in retrofit applications. However, wireless systems require jamming detection capabilities to identify attempts to block sensor signals.
Hybrid alarm systems combine wired and wireless components within a single security installation. Hardwired sensors protect critical entry points where maximum reliability is essential. Wireless sensors extend detection coverage to areas where running cables would be impractical. The control panel manages both sensor types through a unified interface, providing flexible alarm system design options that balance cost, reliability, and installation complexity.
Burglar and perimeter protection technologies
Perimeter protection focuses on detecting intrusion attempts at the boundary of protected space before intruders reach interior areas. Understanding threat categories helps design effective burglar alarm systems. Forced entry involves breaking doors, windows, or walls using physical force. Covert entry exploits unlocked openings or compromised access credentials. Bypass techniques attempt to defeat sensors through cutting wires, blocking signals, or exploiting coverage gaps.
Magnetic contacts on doors and windows detect forced entry in any burglar alarm system. When a protected opening is breached, the contact separates from its magnet and signals the security panel immediately. Supervised wiring detects cable cuts that could disable detection devices.
Glass break sensors monitor windows for forced entry attempts. Acoustic detectors use microphones tuned to shattering glass frequencies. Shock sensors mount on glass surfaces and detect impact vibrations, triggering the alarm system before breakthrough occurs. Fence-mounted sensors protect outdoor perimeters at industrial facilities, identifying climbing, cutting, or lifting of fence fabric along property boundaries.
Zone-based and addressable designs
Zone-based architecture groups multiple sensors into numbered detection zones. When any sensor activates, the panel reports the zone number but not the specific device. A typical residential security system might have eight to sixteen zones. Zone-based alarm systems cost less initially but provide limited diagnostic information for troubleshooting intrusion events.
sAddressable architecture assigns each sensor a unique digital address within the detection system. The panel identifies exactly which device activated, speeding security response by directing personnel to the exact alarm location. Addressable systems support SIA CP-01 false alarm reduction features, automatically adjusting sensitivity and verification requirements.
Large commercial and industrial installations specify addressable alarm systems for faster troubleshooting and superior event documentation. The granular information simplifies maintenance while providing detailed audit trails for burglar detection compliance.
How Alarm System Detection Process Operates
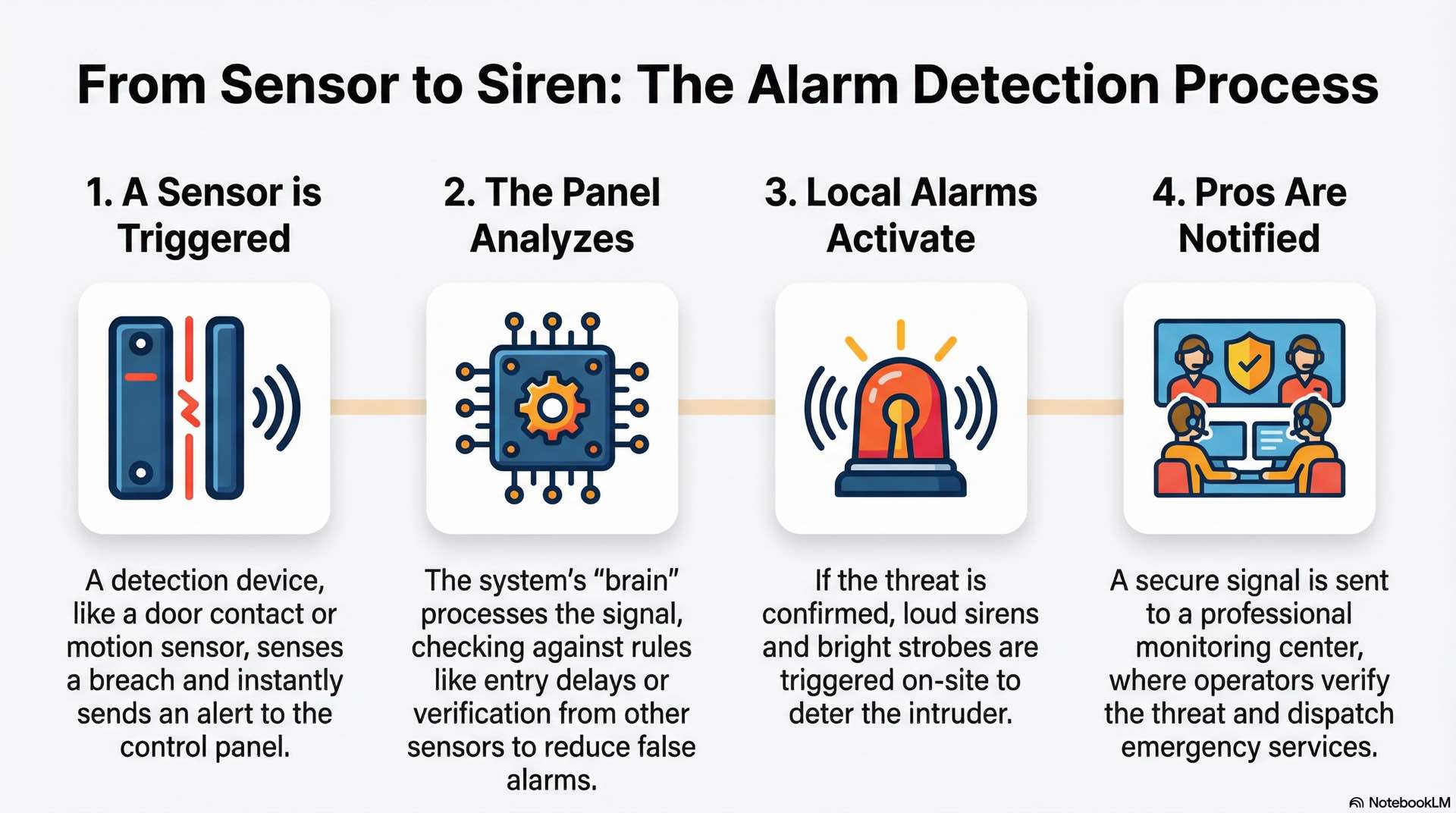
Event detection logic and verification
Detection logic determines how the alarm system interprets sensor signals. Simple logic triggers an alarm whenever a sensor activates during armed periods. More sophisticated security programming incorporates verification requirements before confirming a burglar intrusion and dispatching response.
Cross-zone verification reduces false alarms by requiring confirmation from multiple detection devices. If a motion detector activates but no perimeter sensor reports entry, the alarm system may suppress the alert. SIA CP-01 compliant panels implement cross-zone verification automatically, helping burglar alarm subscribers avoid false dispatch fines.
Video verification represents the most reliable confirmation method for intrusion events. When sensors activate, the alarm system captures video clips or images from nearby cameras and forwards them to monitoring operators. Operators view visual evidence before dispatching response, eliminating costly false dispatches while ensuring genuine security threats receive immediate attention. Video-verified alarms receive priority police response in many jurisdictions.
Intrusion pattern recognition
Pattern recognition analyzes sensor data to distinguish genuine intrusion events from false triggers in modern alarm systems. Environmental factors like HVAC airflow, sunlight, and temperature changes can cause sensor activations without actual burglar activity. Intelligent control panels track patterns and adjust sensitivity automatically.
Sequential activation analysis examines the order of detection events within the security system. An intruder entering through a window should trigger the perimeter sensor before the interior motion detector. Events in illogical sequences may indicate malfunction rather than actual intrusion. This analysis helps differentiate legitimate burglar events from environmental false alarms.
Panel tampering detection identifies attempts to disable the alarm system by opening enclosures, cutting power, or jamming wireless signals. Tamper switches trigger immediate alerts if enclosures are opened. Cellular backup maintains communication if landlines are cut. RF jamming detection identifies attempts to block wireless sensor transmission in the protected space.
Alarm thresholds, delays and decision rules
Entry and exit delays accommodate normal building access without triggering false burglar alarms. Entry delay provides a countdown after a protected door opens, allowing authorized users time to disarm the security system. Exit delay allows users time to leave after arming. Typical delays range from thirty to sixty seconds depending on building layout.
Alarm thresholds define how long a detection condition must persist before the system generates an alarm. Brief activations may be filtered as electrical noise. Sustained activations exceeding the threshold trigger full intrusion alarm processing. These threshold values balance sensitivity against false alarm rates for optimal burglar detection performance.
Decision rules determine escalation paths based on event type, time of day, and system status. Perimeter intrusion during armed periods generates immediate notification and monitoring center dispatch. Fire detection alarms typically override all other security conditions and activate regardless of arm status.
Alarm Sensors and Detection Device Types

Motion detectors and intrusion sensors
Passive infrared motion sensors detect body heat moving through coverage areas, essential components in any burglar alarm system. The sensor contains a pyroelectric element sensitive to infrared radiation in the wavelength range emitted by humans. Fresnel lenses divide coverage into detection zones, triggering when heat signatures move between zones.
Dual-technology sensors combine passive infrared with microwave intrusion detection. Both technologies must detect simultaneously to generate a security alarm. Microwave detection uses the Doppler effect to identify moving objects regardless of temperature. This approach dramatically reduces false alarms while maintaining reliableburglar detection. Standard models provide ninety-degree horizontal coverage with ranges of thirty to fifty feet.
Door and window magnetic contacts
Magnetic contacts consist of a reed switch and magnet, forming perimeter detection foundations in burglar alarm systems. The switch mounts on the door or window frame while the magnet attaches to the moving element. Opening separates components, signaling the security panel for intrusion response.
Surface-mount contacts install visibly on frames for basic alarm system applications. Recessed contacts hide within drilled holes for cleaner appearance. Supervised contacts monitor circuit continuity, detecting tampering or cable cuts that could disable sensors before a burglar event occurs.
Glass break and vibration sensors
Acoustic glass break sensors use microphones to detect shattering glass sounds in burglar alarm applications. Two-stage analysis examines both initial impact and subsequent high-frequency sounds, rejecting false triggers while maintaining reliable intrusion detection.
Shock sensors attach directly to glass surfaces and detect vibration energy from impact or cutting attempts. Combined sensors incorporate both acoustic and shock detection in a single security device, providing comprehensive glass break protection.
Panic buttons and duress devices
Fixed panic buttons install at reception desks and cash registers where employees may face security threats. Pressing sends a silent alarm to the monitoring center without alerting the intruder. Response protocols treat panic activations as confirmed emergencies requiring immediate dispatch.
Wireless pendant-style buttons allow mobile protection throughout facilities. Duress codes provide covert burglar alarm capability at keypads. When forced to disarm, users enter a special code that sends a silent intrusion alert while appearing to work normally.
Environmental detection (smoke, heat, gas)
Smoke detectors identify combustion particles using optical or ionization sensing, extending alarm system protection beyond intrusion to life safety. Heat detectors trigger based on temperature thresholds or rapid temperature rise. Gas detectors monitor for carbon monoxide and combustible gases as part of comprehensive security systems.
Alarm Control Panels and Security Hardware Components
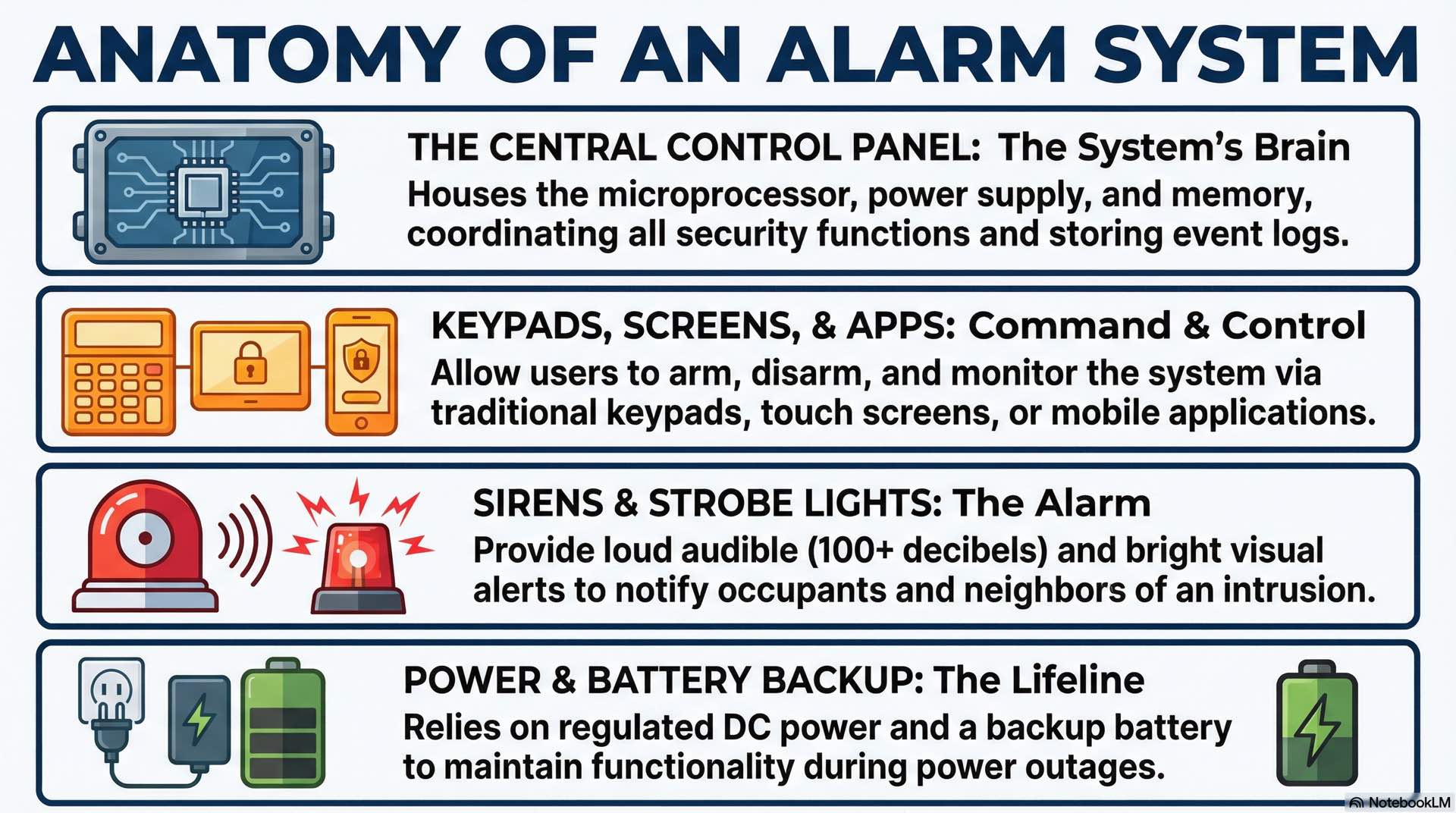
Main control panel architecture
The control panel serves as the alarm system brain, housing the microprocessor, power supply, and communication interfaces that coordinate all security functions. Onboard memory stores programming, user codes, and event logs. Panel capacity determines how many intrusion detection sensors the burglar alarm system supports.
Modern panels include anti-tamper features protecting against panel tampering attacks. Tamper switches detect enclosure opening. Encrypted bus communication prevents signal interception. Backup batteries maintain operation during power outages. These security hardening measures ensure the detection system remains operational when intruders attempt to disable protection.
Expansion modules add capacity for larger security installations. Zone expanders provide additional sensor inputs. Communication expanders support multiple signaling paths for redundancy. This modular architecture allows alarm systems to scale from residential to enterprise deployments while maintaining UL 681 certification compliance.
Keypad and user interface consoles
Traditional keypads feature numeric buttons for code entry plus function keys for arming and disarming the alarm system. Backlit displays show security system status and guide user interaction.
Touch screen consoles provide graphical interfaces for modern security systems. Mobile applications extend alarm system interfaces to smartphones for remote arm, disarm, and monitoring. Push notifications deliver instant alerts for burglar, intrusion, and environmental detection events. Cloud integration enables remote system managementand smart home automation.
Smart home integration connects alarm systems with IoT devices for unified security control. Smart locks allow remote locking and unlocking while reporting door status to the intrusion detection panel. Video doorbells provide visitor verification and motion-triggered recording, extending perimeter detection to approaching visitors before they reach entry points. These connected devices share status through the alarm system app, creating comprehensive property awareness.
Sirens, strobes and notification appliances
Interior sirens produce loud audible alarms, typically one hundred decibels or more, when the security system detects an intrusion. Exterior sirens notify neighbors of burglar alarm conditions. Self-contained units include backup batteries for continued operation during power outages. Strobe lights provide visual indication essential for hearing-impaired occupants.
Power supplies and battery backup units
Control panels require regulated DC power for reliable alarm system operation, typically twelve or twenty-four volts. Battery backup maintains burglar alarm functionality during power outages, with standby capacity ranging from four hours for residential to twenty-four hours for commercial installations per UL requirements. Power supervision monitors AC power, battery voltage, and charging status continuously.
Alarm Communication and Monitoring Methods
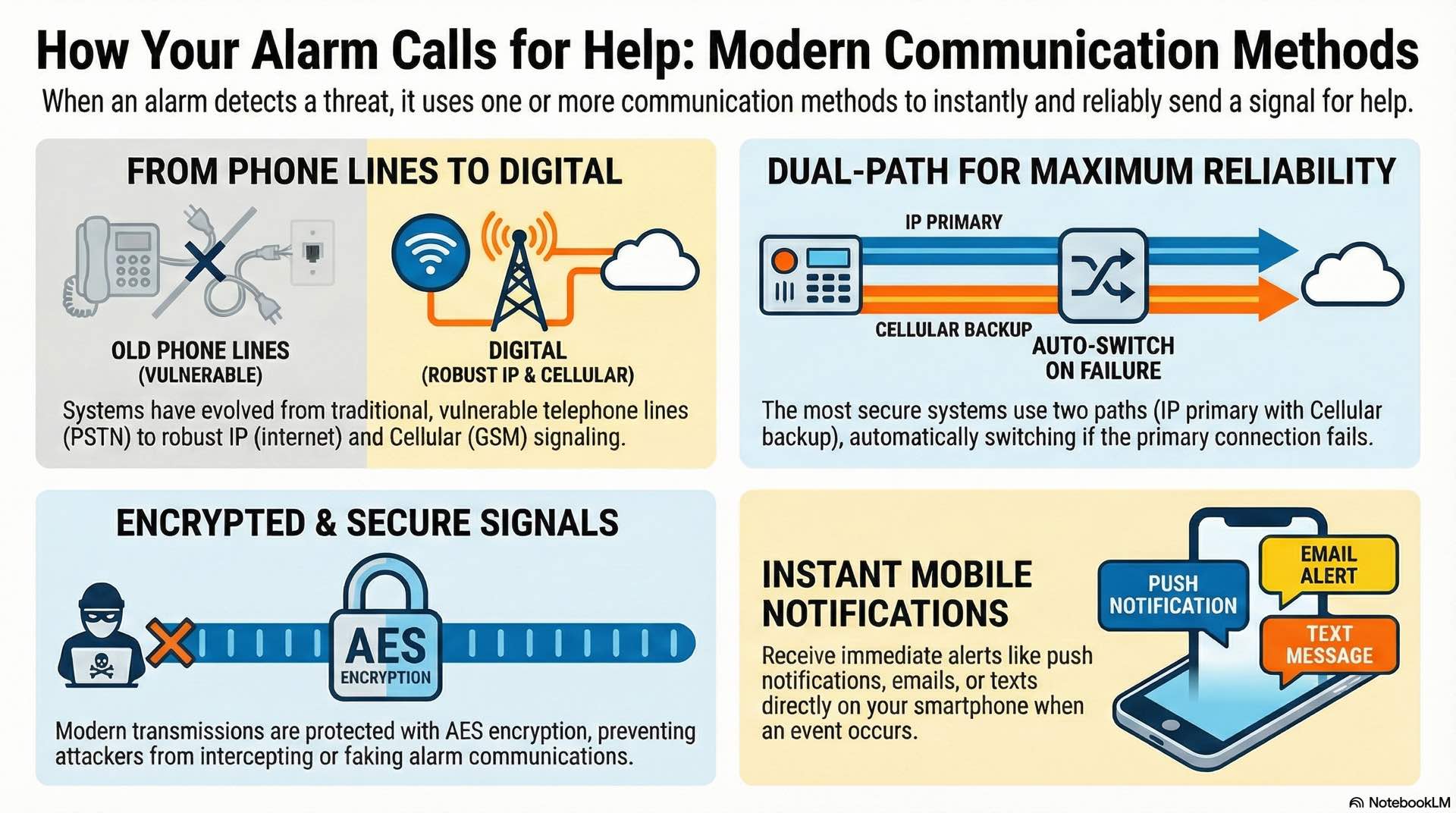
PSTN, GSM, IP and radio signaling
Traditional PSTN signaling uses telephone lines to connect alarm system premises to monitoring centers. While reliable, telephone line vulnerability to cuts makes PSTN unsuitable as the sole communication path for critical security applications.
Cellular GSM communication uses mobile networks for burglar alarm transmission. Cellular signals are much harder to intercept or disable than landline connections. IP communication transmits alarm system data over broadband connections, supporting continuous supervision that detects communication failures within seconds.
Dual-path signaling combines IP primary with cellular backup for maximum reliability. When the primary path fails, the alarm system automatically switches to backup communication. Signal supervision requirements per UL 681 mandate testing communication paths at least once every twenty-four hours, with some high-security applications requiring supervision every few minutes.
Event reporting to monitoring centers
Alarm system panels transmit coded signals identifying account, zone, and event type for every burglar or intrusion detection. Contact ID format uses standardized event codes. Central station receivers decode signals and presentthem to operators with response instructions.
Event prioritization ensures critical conditions receive immediate attention. Fire and medical alarms queue ahead of burglar alarms. Panic activations typically trigger immediate dispatch without extended verification.
Encrypted communication paths
Encryption protects alarm system signals from interception and manipulation. AES-128 or AES-256 encryption secures transmissions over IP and cellular paths. End-to-end encryption protects intrusion detection data from the panel through the network to the monitoring receiver.
Authentication prevents unauthorized devices from accessing security networks. These anti-tamper measures prevent sophisticated attackers from intercepting or spoofing burglar alarm communications.
Remote alerts and mobile notifications
Push notifications deliver instant alerts when alarm system events occur. Interactive apps allow users to acknowledge alarms, view camera feeds, or cancel false burglar alarms directly from smartphones. Email and text alerts provide backup notification through multiple communication channels.
Alarm Software and Monitoring Platforms
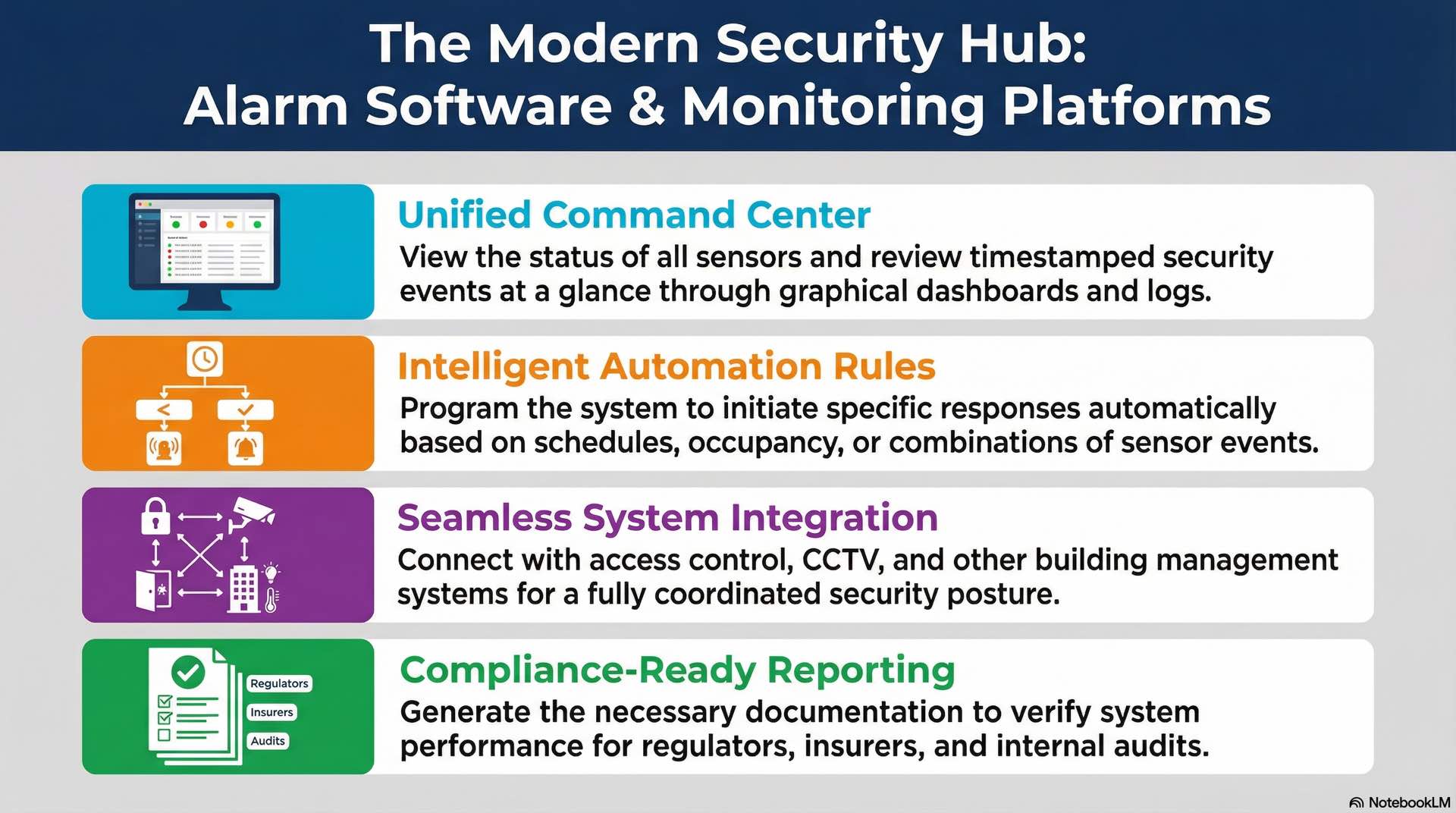
System dashboards and alarm logs
Software dashboards present alarm system status through graphical interfaces. Operators see sensor states and recent intrusion events at a glance. Event logs record every security system occurrence with timestamps for investigation and compliance purposes.
Automation rules and event handling
Programmable rules define alarm system responses to specific conditions. Smart security integration enables automatic responses based on occupancy, schedules, or sensor combinations. Integration with building management enables coordinated responses to intrusion events.
Security integration and data reporting
Modern alarm systems integrate with access control for coordinated security management. Card readers and credential systems communicate door access events to the intrusion detection panel. Electronic locks can automatically secure when the alarm system arms, and valid credential presentation can trigger automatic disarming for authorized users. This integration links physical access credentials with burglar alarm permissions, ensuring departing employees lose both door access and security system codes simultaneously.
CCTV integration links video recording to alarm events, automatically positioning cameras and capturing evidence when burglar detection occurs. Intrusion events trigger instant video clips sent to monitoring operators for verification and evidence preservation.
Open architecture platforms use standard APIs for third-party integration. Compliance reporting generates documentation required by regulators and insurers for alarm system verification.
Alarm System Installation and Commissioning Process
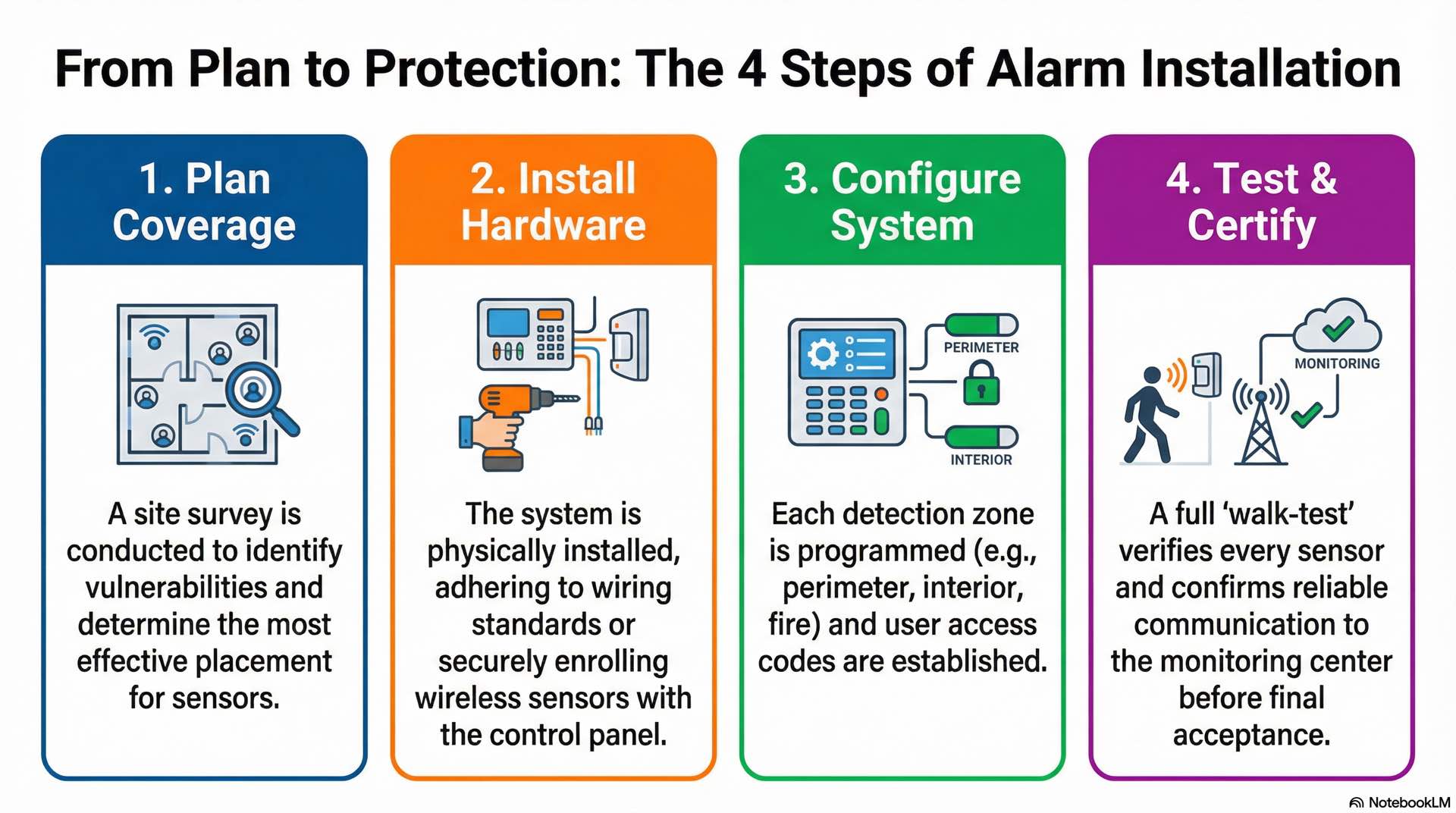
Sensor placement and coverage planning
Effective sensor placement requires understanding intrusion detection technology and the protected environment. Motion detectors should face across likely intruder paths. Coverage planning identifies vulnerable entry points and creates overlapping security zones.
Site surveys identify environmental factors influencing burglar alarm system design. High ceilings may require ceiling-mount sensors. Pet-immune sensors accommodate facilities with animals. Each environment presents unique challenges for security designers.
Wiring standards and wireless enrollment
Alarm system wiring follows NEC and manufacturer standards for safety. Low-voltage cables must maintain separation from line-voltage wiring. Wireless enrollment registers each sensor with the control panel and verifies reliable communication from all intrusion detection locations.
System configuration and zone setup
Zone configuration defines how the alarm system interprets sensor inputs. Each zone receives a designation: entry/exit, perimeter, interior, fire, or panic. User code programming establishes credentials for security system access with appropriate permission levels.
Testing, calibration and acceptance procedures
Commissioning requires comprehensive testing of all alarm system components. Walk testing verifies intrusion detection sensor performance throughout coverage areas. Communication path testing confirms reliable signalingto monitoring centers.
Certification documents system compliance with applicable standards including UL 681 for commercial burglar alarm installations and EN 50131 for European requirements. Acceptance testing demonstrates the security system meets design specifications before handover to the customer.
Alarm System Operations, Maintenance and Security Checks
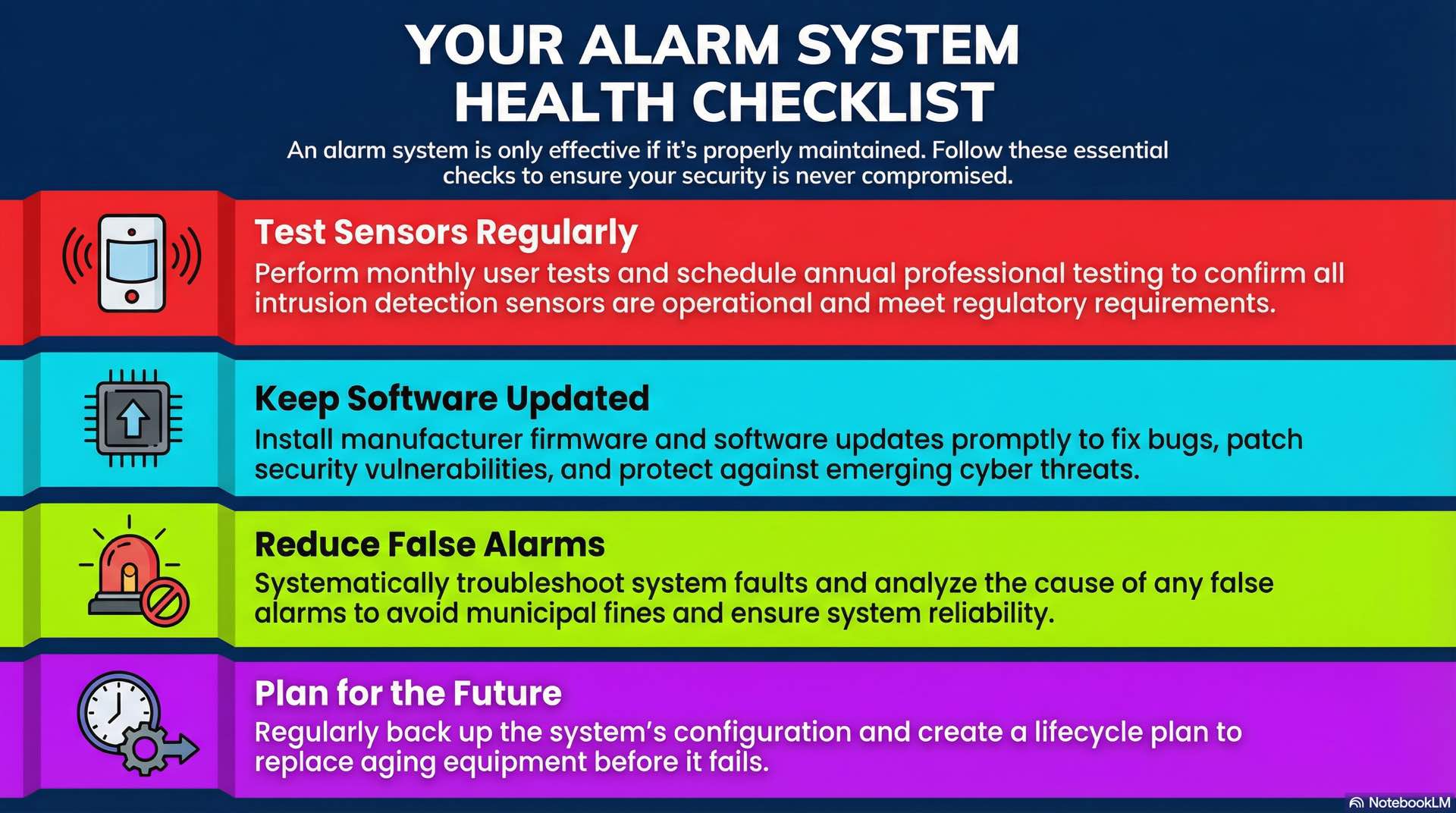
Periodic sensor testing and recalibration
Regular testing confirms intrusion detection sensors remain operational. Annual system testing meets insurance and regulatory requirements for burglar alarm installations. Monthly user testing identifies problems before missed alarms occur.
Environmental changes may require security system recalibration. Battery replacement maintains wireless sensor reliability, typically every three to five years.
Firmware, software and panel updates
Manufacturers release firmware updates to fix bugs and address security vulnerabilities. Prompt patching maintains alarm system integrity against emerging cyber threats. Lifecycle planning identifies replacement timelines for aging intrusion detection equipment.
Fault diagnosis and false alarm reduction
Systematic troubleshooting identifies root causes of alarm system faults. False alarm analysis examines circumstances surrounding unwanted activations. SIA CP-01 compliant programming reduces false dispatchesthrough intelligent verification. Successful programs help burglar alarm subscribers avoid municipal fines.
Backup, restore and lifecycle planning
Configuration backup preserves alarm system programming. Documentation maintains current security records. Lifecycle planning anticipates intrusion detection equipment replacement based on manufacturer support timelines and evolving threat requirements.
Alarm System Compliance, Policy and Security Requirements
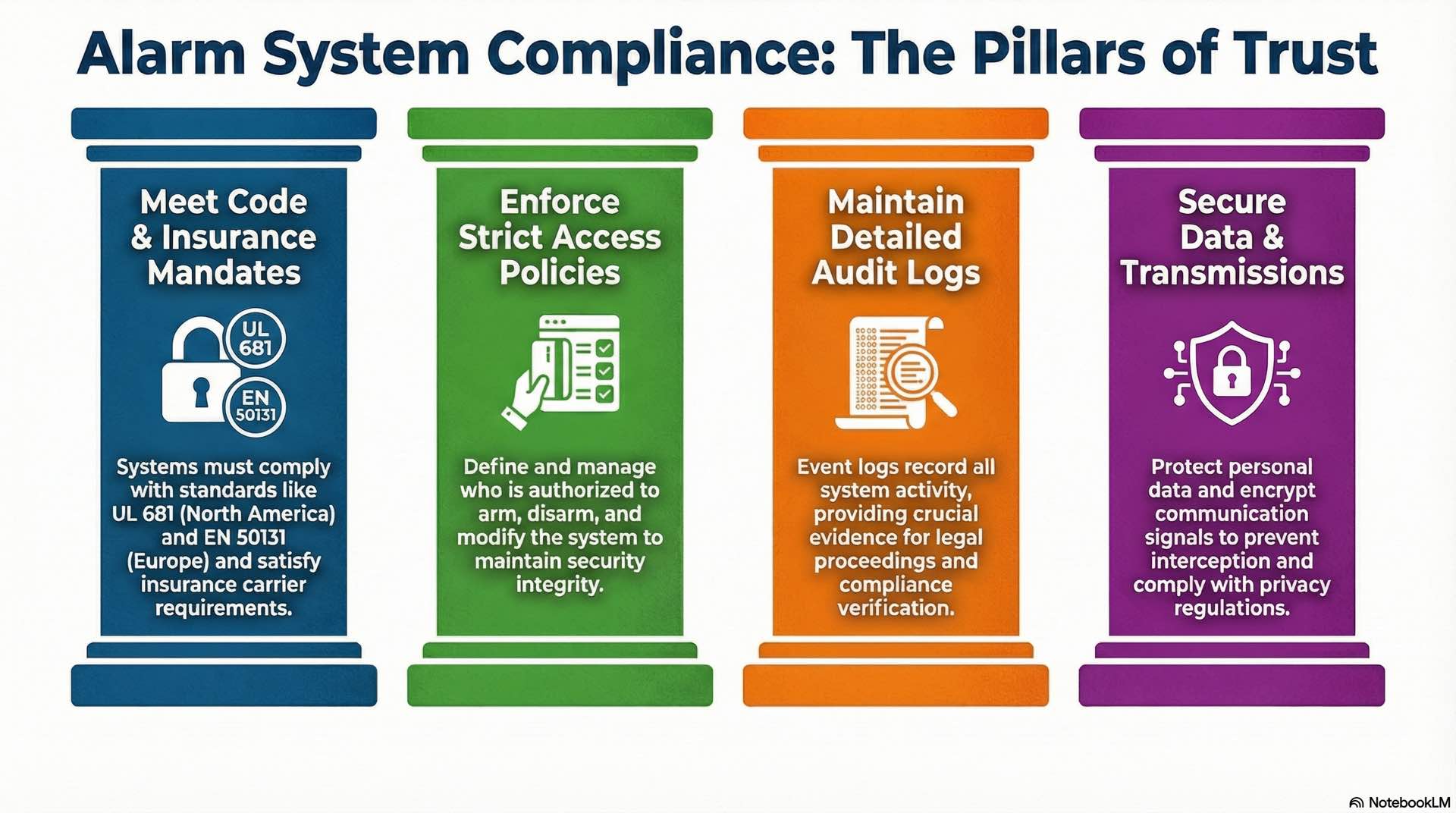
Local code compliance and insurance requirements
Building codes establish minimum alarm system requirements. UL 681 certification applies to commercial burglar alarm installations in North America. EN 50131 establishes graded security requirements across Europe. Insurance carriers often mandate professionally monitored security systems as coverage conditions.
User authorization and access policies
Access policies define who may arm, disarm, and modify alarm systems. Code management protects security system integrity. Audit logs track all intrusion detection access for accountability and compliance.
Audit logs and event record management
Event logs capture alarm system activity for compliance purposes. Retention periods must meet regulatory and legal requirements. Evidence preservation protects log integrity for legal proceedings involving burglar or intrusion events.
Data security and transmission rules
Personal data regulations apply to alarm system monitoring information. Transmission security protects intrusion detection signals from interception. Vendor assessments verify third-party compliance for burglar alarm monitoring services.
An effective alarm system combines intrusion detection technologies, reliable control panels, and redundant communication paths to protect against burglar threats and security risks. From magnetic contacts to video-verified addressable sensors, each detection device contributes to comprehensive protection meeting UL 681 and EN 50131 standards. Proper installation, commissioning, and annual testing ensure these security systems perform reliably when threats emerge. Organizations investing in professionally monitored, dual-path burglar alarm equipment with smart integration achieve the intrusion protection their facilities require while maintaining compliance with codes, insurance requirements, and industry best practices.





